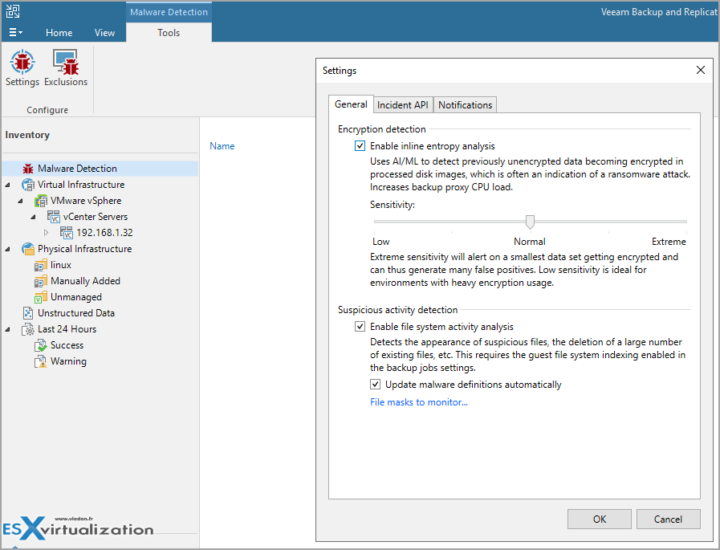
Veeam Backup and Replication 12.1 introduced an interesting feature. This feature is called Encryption Detection and it is an Inline entropy analysis that uses Artificial Intelligence and Machine learning (AI/ML) to detect previously unencrypted data which becomes encrypted within the processed disk images. This shows that you possibly starting to be a victim of a ransomware attack. The Inline Entroyp Analysis does analyze the data on the fly during backups.
This encryption (if any), as it progresses more and more within your network, will put down more and more systems. The detection of the beginning of encrypted data is a key element within your protection against ransomware. The Inline entropy analysis as well as the Suspicious activity detection features are good help to fight ransomware and make sure you're not backing up already half-corrupted systems.
Note: By default, the Encryption detection is unchecked. The suspicious activity detection is checked.
Click OK to validate.
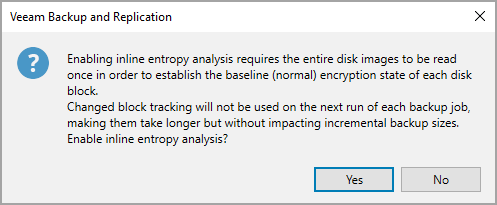
You'll receive a pop-up message saying that the inline entropy analysis requires reading the entire disk image to establish a baseline. This is only happening once. And that the CBT won't be used on the next run of each backup job, but without impacting size.
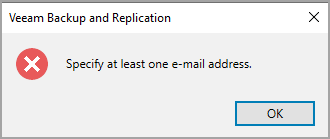
Note: if you haven't filled an email notification within the settings (3rd tab from the left), the system will warn you about it because it needs an email to send the results.
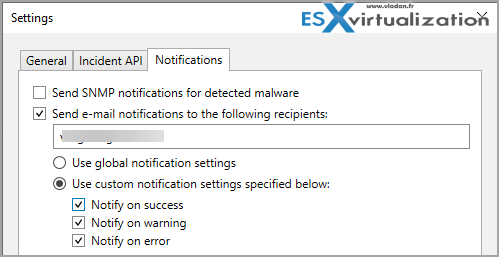
The notification settings looks as follows:
From Veeam's documentation:
To scan blocks in a data stream, Veeam Backup & Replication uses file entropy analysis. During the backup job, the following malware activity can be detected:
- Files encrypted by malware. A malware detection event will be created if the amount of encrypted data exceeds scan sensitivity limits.
- Text artifacts created by malware:
- V3 onion addresses that consist of 56 symbols in the [a-z2-7]{56}.onion format. For example, vykenniek4sagugiayj3z32rpyrinoadduprjtdy4wharue6cz7zudid.onion. A malware detection event will be created if at least one onion address is found.
- Ransomware notes created by Medusa and Clop. A malware detection event will be created if at least one ransomware note is found.
Which type of VMs (or systems) are scanned with Veeam Intropy Analysis?
- VMware VMs including VMware Cloud Director VMs
- Hyper-V VMs
- Machines with Veeam Agent for Microsoft Windows operating in the managed mode (volume-level backup only)
- Machines backed up to tape devices
The following file systems are supported: NTFS, ext4, ext3, ext2.
How It Works?
During the backup job, Veeam Backup & Replication analyzes data blocks metadata and saves ransomware data in the temporary folder on the backup proxy.
A file in the RIDX format is created for each disk and contains the following information:
- Disk metadata (disk name, creation time, disk size, used size, sector size, partition table)
- Ransomware data for each data block (the amount of encrypted data, anomalous magic numbers of file types, onion addresses and ransomware notes)
NOTE:
If LZMA headers are found, they will be excluded from encrypted data calculation to decrease the number of false-positive events.
When the backup job is complete, ransomware data is saved in the VBRCatalog folder on the backup server. The Veeam Guest Catalog Service notifies the Veeam Data Analyzer Service about new data that need to be scanned. The Veeam Data Analyzer Service checks last scan results in the RansomwareIndexAnalyzeState.xml file located in the VBRCatalog folder and initiates a new scan session. The scan session is also initiated if the Veeam Data Analyzer Service gets new indexing data after the service starts.
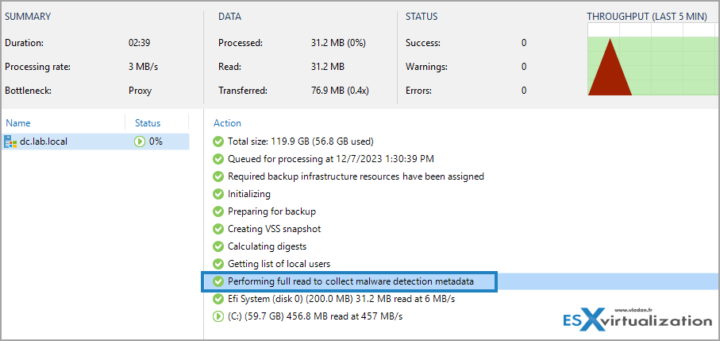
Screenshot from the lab.
After activation, you'll see that during the first backup, the system needs to read the whole disks to collect malware detection metadata.
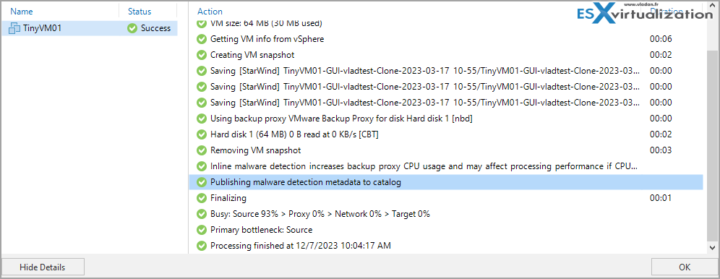
And this is the screenshot after backup taken (different, smaller VM from the lab).
The Veeam Data Analyzer Service compares the last and previous RIDX files and updates the RansomwareIndexAnalyzeState.xml file. If malware activity is detected, the service will create a malware detection event and mark objects as Suspicious. If the previous RIDX file is not found, the Veeam Data Analyzer Service will perform a full disk read operation to create a RIDX file. In this case, the job session will last longer than usual but the size of the incremental backup file will not be affected. A full disk operation will also be performed if you add a new disk to the VM.
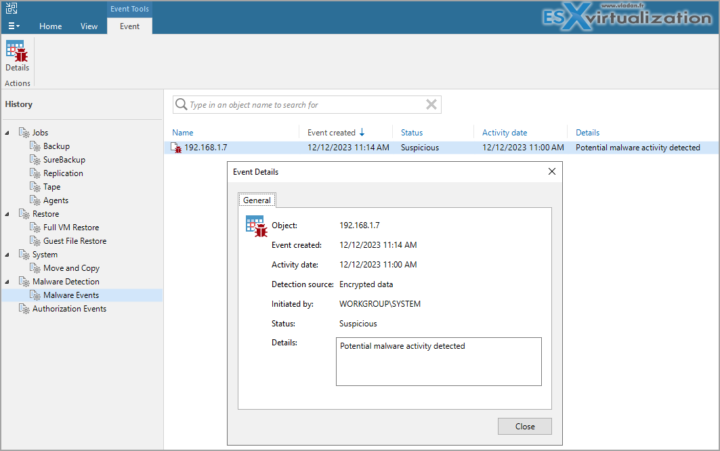
Example from the lab by “infecting” my domain controller VM…. (created a text file with a code that looks like suspicious …)
Final Words
The inline entropy analysis feature is a powerful and innovative tool that enhances the security and reliability of your backup data. It can help you detect and prevent ransomware attacks and minimize the impact of data loss and downtime. It is one of the reasons why Veeam Backup & Replication is a leading software in the data protection industry.
Detailed articles about v12 new features:
- Veeam 12.1 Biggest Features
- Your repository is full – How to move your backups to another repository with Veeam backup?
- Practical Tips to protect your Veeam Backup Repositories
- Veeam Backup and Replication v12 – Get the latest ISO
- What is Veeam VHR and how to quickly install and create hardened repository?
- Don’t miss this Veeam v12 Download with latest cumulative patches
- Practical Tips to protect your Veeam Backup Repositories
- Veeam Backup and Replication 12 (Beta2) Installation
- Veeam Backup and Replication 12 (BETA) – adding Hardened Linux Repository
- Veeam Immutable Backups – Your protection against Ransomware
More posts from ESX Virtualization:
- VMware vSphere 8.0 U2 Released – ESXi 8.0 U2 and VCSA 8.0 U2 How to update (NEW)
- What’s the purpose of those 17 virtual hard disks within VMware vCenter Server Appliance (VCSA) 8.0?
- VMware vSphere 8 Update 2 New Upgrade Process for vCenter Server details
- VMware vSAN 8 Update 2 with many enhancements announced during VMware Explore
- What’s New in VMware Virtual Hardware v21 and vSphere 8 Update 2?
- Homelab v 8.0
- vSphere 8.0 Page
- Veeam Bare Metal Recovery Without using USB Stick (TIP)
- ESXi 7.x to 8.x upgrade scenarios
- A really FREE VPN that doesn’t suck
- Patch your ESXi 7.x again
- VMware vCenter Server 7.03 U3g – Download and patch
- Upgrade VMware ESXi to 7.0 U3 via command line
- VMware vCenter Server 7.0 U3e released – another maintenance release fixing vSphere with Tanzu
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)