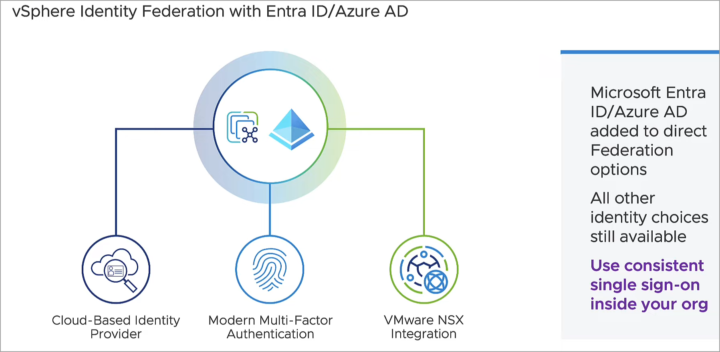
One of the security enhancements that came out with vSphere 8 U2 and we haven't talked yet is vSphere 8 U2 Identity Federation with Entra ID/Azure AD. This feature is an enhancements of the vSphere identity federation feature that are part of VCP exam topics here – VCP-DCV on vSphere 8.x Objective 1.10 – Describe identity federation – and here VCP-DCV on vSphere 8.x Objective 1.10.2 Recognize use cases for Identity Federation.
VMware vSphere 8 identity federation provides organizations with a powerful tool to simplify identity management and enhance security across different domains, vCenter servers. The U2 adding more choices for identity providers. Because it is federates identity it means that vSphere never sees the users credentials. It helps with security, but also for compliance.
vSphere 8 U2 Identity Federation with Entra ID/ Azure AD is a feature that allows vCenter Server to delegate user authentication and authorization to Azure AD, using the OpenID Connect (OIDC) and System for Cross-domain Identity Management (SCIM) protocols.
Screenshot from VMware
How does it works?
When trying to login into vSphere, you're redirected to the identity service and once you're authenticated, you're redirected back to your vCenter.
Quote:
The user credentials are no longer provided to vCenter Server directly. Instead, the user provides credentials to the external identity provider. vCenter Server trusts the external identity provider to perform the authentication. In the federation model, users never provide credentials directly to any service or application but only to the identity provider. As a result, you “federate” your applications and services, such as vCenter Server, with your identity provider.
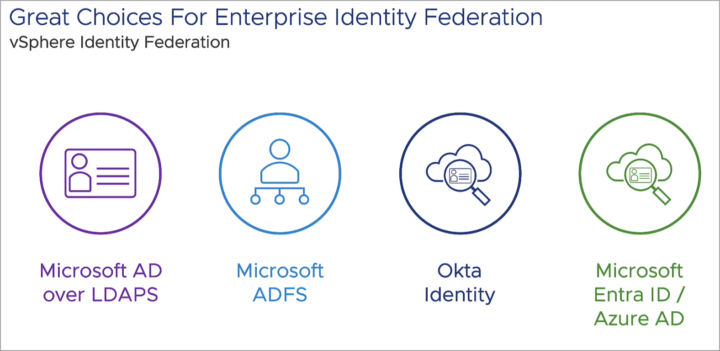
Right now, there are several choices you have.
vCenter Server supports the following external identity providers:
- AD FS (vSphere 7.0 and later)
- Okta (starting in vSphere 8.0 Update 1 and later)
- Azure AD (starting in vSphere 8.0 Update 2)
Screenshot from VMware
vSphere 8 U2 Identity Federation with Entra ID/Azure AD Requirements
Quote:
- You are customer of Microsoft and have a Azure AD account.
- You have created enterprise (non-gallery) application with OpenID Connect as a sign-on method.
- Add authorization code, refresh token and resource owner password as grant types in the created application.
- For user and group sync, you need to configure VMware Identity Services Gallery
- Application for SCIM 2.0 provisioning in Azure AD with OAuth 2.0 Bearer Token.
- vCenter server is connected to Azure AD discovery endpoint and authorization, token, logout, JWKS and any other endpoints advertised in the discovery endpoint metadata
- You need the VcIdentityProviders.Manage privilege to create, update, or delete a vCenter Server Identity Provider that is required for federated authentication. To limit a user to view the Identity Provider configuration information only, assign the VcIdentityProviders.Read privilege
- If you have previously added vCenter group memberships for any remote AD/LDAP users or groups, vCenter attempts to prepare these memberships so that they are compatible with the new identity provider configuration. This preparation process happens automatically at service startup, but it must complete in order to continue with this configuration wizard. Click the button below to check the status of this process before proceeding.
Interesting facts (from VMware documentation):
link here.
Quote:
Starting in vSphere 8.0 Update 2, VMware Identity Services provide integration with Azure AD as a federated identity provider. You can think of the VMware Identity Services as a “slimmed” down version of VMware Workspace ONE that is built-in to vSphere.
When you either install or upgrade to vSphere 8.0 Update 1, VMware Identity Services are activated by default on vCenter Server. When you configure Okta or Azure AD as an external identity provider, vCenter Server uses VMware Identity Services to communicate with your Okta or Azure AD server.
vCenter Server supports Okta or Azure AD as an external identity provider in an Enhanced Linked Mode configuration. Even though, in an Enhanced Linked Mode configuration, multiple vCenter Server systems are running VMware Identity Services, only a single vCenter Server and, its VMware Identity Services communicate with your external IDP server. For example, if you have an Enhanced Linked Mode configuration of three vCenter Server systems, A, B, and C, and you configure the Okta identity provider on vCenter Server A, vCenter Server A is the only system to handle all the Okta logins. vCenter Server B and vCenter Server C do not directly communicate with the Okta server.
The process of configuring can be found here in VMware documentation or watch the configuration video below.
Video from VMware (no wording):
Sources: VMware documentation , here too.
Few more links:
- vSphere 8.0 Update 2: Federated Authentication with Azure Active Directory
- Configure vCenter Server Identity Provider Federation for Azure AD
- How to Enable Azure AD for vCenter Server
Final Words:
vSphere 8 U2 Identity Federation with Azure AD is a powerful feature that allows vSphere administrators to integrate vCenter Server with Azure AD, and enjoy the benefits of single sign-on, multi-factor authentication, and user and group synchronization. This feature can improve the security and resilience of vSphere environments, by leveraging the existing identity provider infrastructure, facilitating functional separation of duties, and enabling additional authentication methods.
More posts from ESX Virtualization:
- VMware vSphere 8.0 U2 Released – ESXi 8.0 U2 and VCSA 8.0 U2 How to update
- What’s the purpose of those 17 virtual hard disks within VMware vCenter Server Appliance (VCSA) 8.0?
- VMware vSphere 8 Update 2 New Upgrade Process for vCenter Server details
- VMware vSAN 8 Update 2 with many enhancements announced during VMware Explore
- What’s New in VMware Virtual Hardware v21 and vSphere 8 Update 2?
- Homelab v 8.0
- vSphere 8.0 Page
- Veeam Bare Metal Recovery Without using USB Stick (TIP)
- ESXi 7.x to 8.x upgrade scenarios
- A really FREE VPN that doesn’t suck
- Patch your ESXi 7.x again
- VMware vCenter Server 7.03 U3g – Download and patch
- Upgrade VMware ESXi to 7.0 U3 via command line
- VMware vCenter Server 7.0 U3e released – another maintenance release fixing vSphere with Tanzu
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)