Ransomware recovery as a service, delivered under disaster recovery services. It is very difficult problem when you're hit by ransomware. You usually experience downtime, possibly with loss of data.
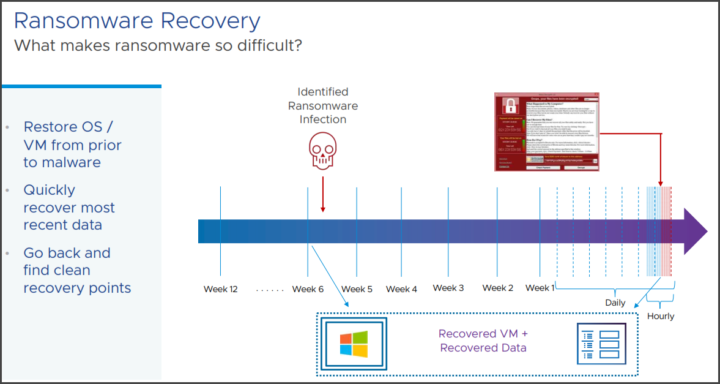
Usually, it's not a usual disaster where like you lose power so you have to reboot your hosts etc. The ransomware might be inside your environment for a long time and just dormant, undetected. One of the most difficult points is to detect the ransomware infection within your backup files.
This is an upcoming product release (or SaaS) that VMware is working on. Ransomware is a huge problem as its complex. Restore? Yes, but from which restore point? As we don't know which restore point is clean from ransomware.
VMware cloud ransomware recovery
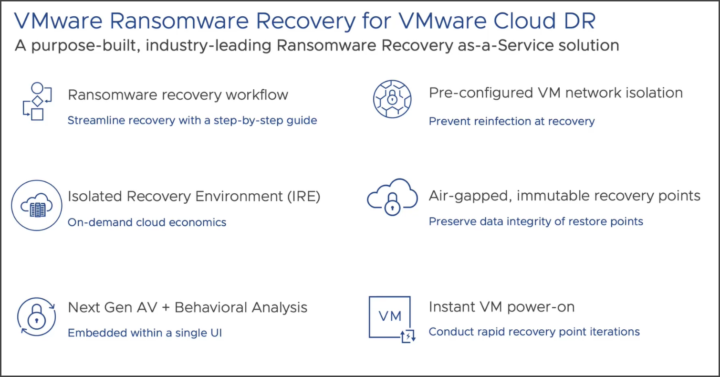
Recovery workflow – it is a step-by-step process for recovery. It starts with validating your recovery points that are free of ransomware. VMware ransomware recovery for VMware cloud will be set as an isolated environment.
You have a single UI and management workflow, they embedded Antivirus and behavioral analysis. Pre-configured VM network isolation.
VMware ransomware recovery is built in the VMware Cloud DR.
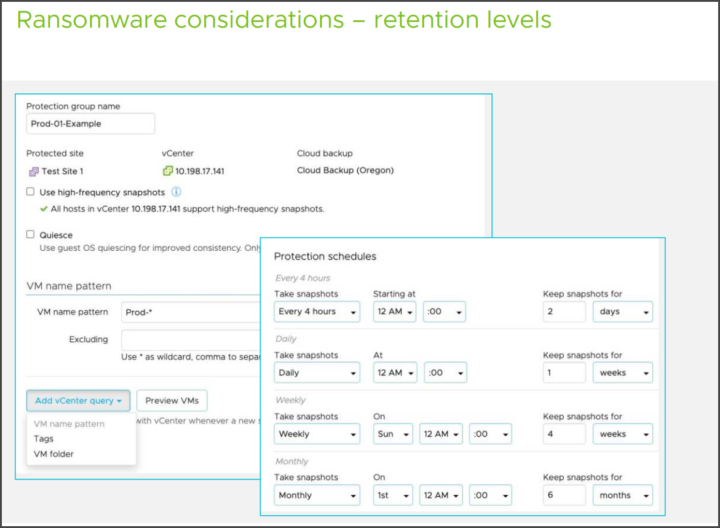
- Deep snapshot history
- Immutable snapshots, air-gapped, data integrity checks, role-based access control, and MFA
- Instant power-on (zero copy, no rehydration), recovery orchestration, VMware Cloud SDDC as isolated recovery environment (IRE)
- File/folder level restore, individual VM restore, Multi VM orchestrated recovery.
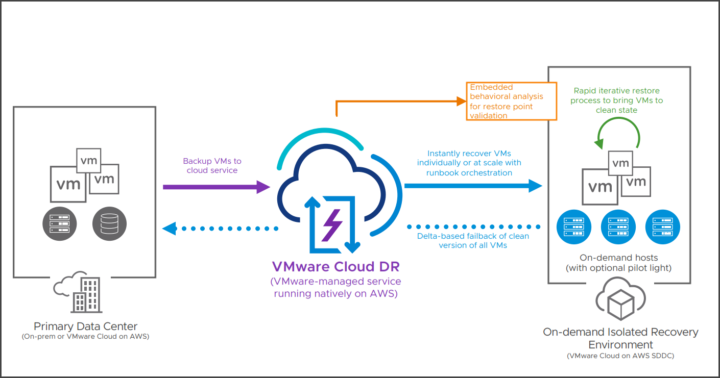
The architecture looks like this actually.
To find the good restore points quickly. Because if you don't have clean recovery points you'll be restoring data already infected again so it's pretty much useless. That's why it's important to find the latest clean recovery points you have in the archives.
- Dedicated ransomware recovery workflow – bring VMs from backup to a validation area. The validation area will scan the VM until a clean state is found, then the VM is staged and recovered.
- Behavioral Analysis – it needs powered on VMs, and via ML/AI inspect normally vs suspicious activity. (a simple file scanning will not be sufficient).
- Optimize Total cost of ownership – pay-as-you-go failover capacity model. Delta-based failback. You won't need a secondary data center just for ransomware recovery.
- Isolated recovery environment (IRE) – you can have an on-demand testing environment that is built on-demand.
The system will have preconfigure VM network isolation (via NSX). It's build on the top of scale-out-file-system.
This is about all we have today, but stay tuned during VMware EXPLORE as VMware will talk quite a lot about this new SaaS solution.
Check out our vSphere 8 page for other articles about vSphere 8, VMware EXPLORE and new tutorials.
Shop:
- VMware vSphere 7.0 Essentials PLUS
- VMware vSphere 7.0 Essentials
- VMware vSphere 7.0 Enterprise PLUS
- VMware vSphere 7.0 with Tanzu
- VMware vSphere for Remote Office 7.0 – ROBO Standard
- VMware vSphere for Remote Office 7.0 – ROBO Advanced
- vSphere Essentials Per Incident Support
- VMware Workstation 16 Pro and Upgrade
- VMware Fusion 12 and Upgrade
- VMware Fusion 12 Pro and Upgrade
- Upgrade to vSphere Enterprise Plus
- VMware Current Promotions
More posts from ESX Virtualization:
- More Patches for VMware – vCenter 7.0U3f and ESXi 7.0U3f
- VMware vCenter Server 7.0 U3e released – another maintenance release fixing vSphere with Tanzu
- VMware vCenter Converter Discontinued – what’s your options?
- How to upgrade VMware VCSA 7 Offline via patch ISO
- vSphere 7.0 U3C Released
- vSphere 7.0 Page[All details about vSphere and related products here]
- VMware vSphere 7.0 Announced – vCenter Server Details
- VMware vSphere 7.0 DRS Improvements – What's New
- How to Patch vCenter Server Appliance (VCSA) – [Guide]
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)