VMware just released NSX-T 3.0 which is a major upgrade for this SDN product. It is already an 8th iteration and VMware was pushing hard the development, leaving the NSX-V behind, phased out.
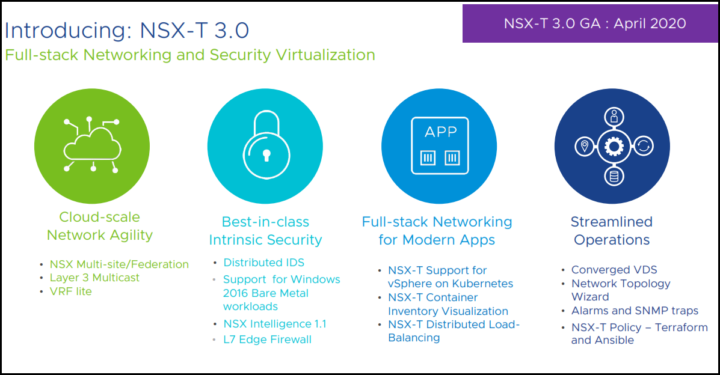
In this new release, there are many new features and innovations such as NSX Federation, Intrinsic security or networking for modern apps (Kubernetes workloads).
NSX-T 3.0 is fully compatible with VMware vSphere 7.0 released just last week. It is possible to run NSX straight on vSphere Distributed Switch (VDS 7.0) which is part of vSphere 7.0. There is a new, simplified deployment from Center UI.
When deploying NSX there is no disruption to existing VDS, no VM traffic disruption either.
NSX-T 3.0 has new Getting started wizard to prepare clusters for micro-segmentation. This allows you to deploy micro-segmentation faster, in 3 easy steps.
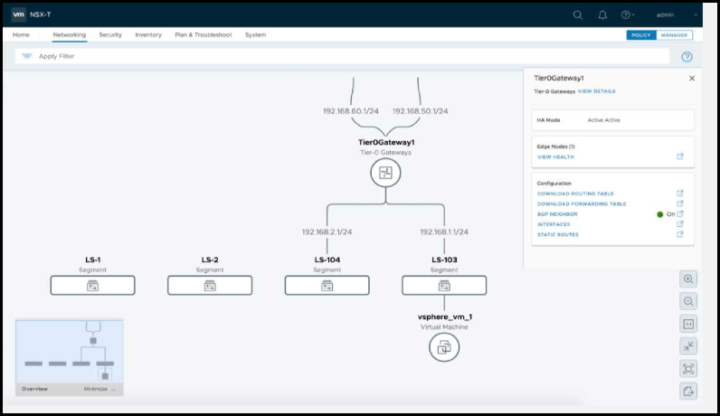
There is also a new graphical visualization of the network infrastructure and you have a possibility to export the topology as a PDF.
It gives you end to end visibility for easier configuration.
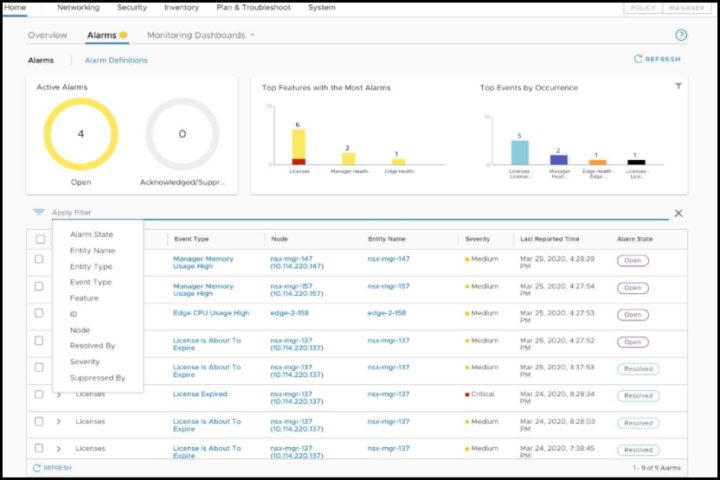
There is also a new Alarm dashboard allowing you to manage alarms. To define, acknowledge and suppress alarms.
From the release notes:
NSX-T Data Center 3.0 includes a variety of new features to provide new functionality for virtualized networking and security for private, public, and multi-clouds. Highlights include the following focus areas and new features:
- Cloud-scale Networking: NSX Federation
- Intrinsic Security: Distributed IDS, Micro-Segmentation for Windows Physical Servers, Time-based Firewall Rules, and a feature preview of URL Analysis
- Modern Apps Networking: NSX-T for vSphere with Kubernetes, container networking and security enhancements
- Next-Gen Telco Cloud: L3 EVPN for VM mobility, accelerated data plane performance, NAT64, IPv6 support for containers, E-W service chaining for NFV
The following new features and feature enhancements are available in the NSX-T Data Center 3.0.0 release.
L2 Networking
NSX-T support on VDS 7.0
NSX-T now has the capability to run on the vSphere VDS switch version 7.0. It is recommended that new deployments of NSX and vSphere take advantage of this close integration and start to move toward the use of NSX-T on VDS. The N-VDS NSX-T host switch will be deprecated in a future release. Going forward, the plan is to converge NSX-T and ESXi host switches. The N-VDS remains the switch on the KVM, NSX-T Edge Nodes, native public cloud NSX agents and for bare metal workloads.
The current NSX-T ESXi host switch, the N-VDS, continues to be supported for this release and it is recommended that NSX deployments that currently use the N-VDS on ESXi continue to utilize the same switch. The reason for this is two-fold:
- The conversion of N-VDS to VDS 7.0 for existing NSX deployments is a manual process. Please contact your VMware representative for further details if required.
- The APIs between N-VDS and VDS are different. There are no changes to N-VDS or VDS APIs. However, if you move to use the VDS in your environment you will have to start invoking the VDS APIs instead of N-VDS APIs. This ecosystem change will have to be made before converting the N-VDS to VDS.
The following deployment considerations are recommended when moving from N-VDS to VDS:
- VDS is configured through vCenter. N-VDS is vCenter independent. With NSX-T support on VDS and the eventual deprecation of N-VDS, NSX-T will be closely tied to vCenter and vCenter will be required to enable NSX.
- The N-VDS is able to support ESXi host specific configurations. The VDS uses cluster-based configuration and does not support ESXi host specific configuration.
- This release does not have full feature parity between N-VDS and VDS.
- The backing type for VM and vmKernel interface APIs is different for VDS when compared to N-VDS.
RHEL support: We add RHEL 7.6 and RHEL 7.7 to the list of supported operating systems for NSX. This applies to KVM and Bare Metal workloads.
Edge Bridge:
Segments that have been configured for Guest VLAN tagging can now be extended to VLAN through an edge bridge. The feature is enabled by configuring a range of VLAN IDs when mapping a segment to a bridge profile. Segment traffic with a VLAN ID in the range is bridged to VLAN, keeping their VLAN tag. Traffic received on the VLAN side of the bridge with a VLAN ID falling in the configured range in the segment to bridge mapping is bridged into the segment, keeping their VLAN ID as a guest VLAN tag.
Policy-based UI support is now available for the edge bridge.
MAC Limit per VNI: The default value of default MAC limit per Logical switch is 2,048 in ESXi dataplane. NSX now provides the ability to change the MAC limit per logical switch from the default value to match customer requirements.
Support for Windows 2016 Bare Metal Server
NSX supports the following use cases:
- Connectivity with VLAN-backed virtualized workloads
- Connectivity with overlay-backed virtualized workloads
- Security for communication between virtual and physical workloads
- Security for communication between physical workloads
Support is available for:
- Two PNICs case (Mgmt. and Application use separate IP)
- One PNIC case (Mgmt. and Application use same IP)
See the VMware Configuration Maximums for currently supported maximums.
Enhanced Data Path
- Zero tx copy support in ENS – For bigger packet sizes (600-700B), zero tx copy is now supported. This is supported from vSphere 7.0, improves l2/l3 cache miss, which leads to better overall performance.
- FPO Flow Director offload & associated vmkapi changes – N-VDS support for NIC offloads and hence improved performance in Enhanced Data Path.
- U-ENS Dataplane Consolidation – ENS (Enhanced Network Stack) and FC (Flow Cache) provide fast-path on N-VDS (or vswitch) for NSX-T. ENS is for general purpose while FC is more for telco use cases.
- ENS performance optimizations – Performance Improvements with respect to cache utilization and packet sizes have been made.
Federation
NSX-T 3.0 introduces the ability to federate multiple on-premises data centers through a single pane of glass, called Global Manager (GM). GM provides a graphical user interface and an intent-based REST API endpoint. Through the GM, you can configure consistent security policies across multiple locations and stretched networking objects: Tier0 and Tier1 gateways and segments.
Edge Platform
- New Edge VM XLarge form factor provides more scale for advanced services and better throughput.
- Enhanced convergence time on Tier-0 gateway with lower BFD interval supported on Edge VM down to 500ms and 50ms on Bare Metal Edge.
- Enhanced Edge VM deployment: During Edge VM deployment through NSX, the following actions are taken:
- Auto start the Edge VM on ESX reboot
- Disable edit settings of Edge VM in vCenter
- Edge VM added in the DFW exclude list
- Configuration of the following parameters: allow SSH, allow root login, NTP server list, domain search list, DNS server list and default users credentials
- AMD EPYC support: Edge Nodes, VM and Bare Metal can now be deployed on AMD EPYC series CPU:
- AMD EPYC 7xx1 Series (Naples)
- AMD EPYC 3000 Embedded Family and newer
- AMD EPYC 7xx2 Series (Rome)
L3 Networking
- Change of Tier0 Gateway HA mode through UI/API offers the option to change Tier-0 gateway High Availability mode from Active/Active to Active/Standby and vice versa through UI and API.
- VRF Lite support provides multi-tenant data plane isolation through Virtual Routing Forwarding (VRF) in Tier-0 gateway. VRF has its own isolated routing table, uplinks, NAT and gateway firewall services.
- L3 EVPN support provides a northbound connectivity option to advertise all VRFs on a Tier-0 gateway through MP-BGP EVPN AFI (Route Type 5) to a Provider Edge and maintain the isolation on the dataplane with VXLAN encapsulation by using one VNI per VRF.
- Rate-limit support on Tier-1 gateways provides the ability to rate-limit all the traffic going egress and ingress of the Tier1 gateway uplink.
- Metadata Proxy support in policy and UI enhances the intent-based API and policy UI to configure Metadata Proxy.
- DHCP server policy and UI enhances the intent-based API and policy UI to configure a DHCP server locally to a segment.
- Policy API for L3 enhances the intent-based API and policy UI to retrieve runtime information on the gateways.
- L3 Multicast (Phase1):
- NSX-T 3.0 introduces Multicast in NSX-T for the very first time.
- Multicast replication is only supported on T0, and any host expecting to have multicast workloads will have to be connected to T0. T1 will be supported in future releases.
- There is also just one uplink from the Edge to the TOR in NSX-T 3.0. In future releases, redundancy will be built-in and there could be multiple uplinks to a TOR supporting PIM.
- RP always has to be programmed outside the NSX domain.
- No Edge Services are supported for Multicast Traffic in NSX-T 3.0.
IPv6
- NAT64 offers a transition mechanism from IPv4 to IPv6. It provides stateful Network Address Translation from IPv6 to IPv4 following standard RFC 6146.
- Stateful DHCPv6 Support – NSX now supports stateful delivery of IPv6 addresses and associated parameters through NSX native DHCP server hosted on Edge nodes.
Firewall
- Consistent Security Policy across multiple sites using NSX Federation – NSX-T 3.0 introduces the concept of a Global Manager (GM) that can manage multiple NSX Managers. With NSX-T 3.0, the global manager has the capability of consistent security policy across multiple sites through a single pane of glass.
- Introducing Security Dashboards – NSX-T 3.0 introduces new Security Overview Dashboards for security and firewall admins to see at-a-glance the current operational state of firewall and distributed IDS.
- Time-based Scheduling of Firewall Rules – With NSX-T 3.0, you can now schedule enforcing of specific rules for specific time intervals.
- Introducing wizards to quickly do VLAN-based Micro-Segmentation – You can configure your data centers to introduce segmentation using NSX-T in very easy steps.
- Micro-Segmentation for Windows Physical Servers – Introducing micro-segmentation for windows physical servers in NSX-T 3.0.
- URL Analysis – Feature Preview – Introducing a preview of URL Filtering with detection, classification and reputation scores of URLs. This feature preview is available only on the gateway firewall.
- Supporting TCP/UDP and ICMP Session Timer Configuration for FW in KVM – Supporting firewall timer configuration changes in KVM for workloads running on KVM.
Identity Firewall
- Filter ICMP traffic for VDI environments as part of Identity Firewall rules – This allows the creation of Identity Firewall rules for VDI users to filter traffic based on the ICMP protocol. This is limited to VDI and not available for RDSH users.
- Selectively sync AD groups for Identity Firewall groups – This allows syncing of specific AD groups to be used as endpoints in Identity Firewall rules. This capability optimizes the performance and usability of the AD Groups. This capability is currently available using the API only.
- Filter UDP traffic for Identity Firewall rules – This allows filtering UDP traffic as part of Identity Firewall rules.
Distributed Intrusion Detection System (D-IDS)
Introducing in NSX Platform the capability of Distributed Intrusion Detection as a part of the platform's Threat & Vulnerability Detection capabilities. This feature allows you to enable intrusion detection capabilities within the hypervisor to detect vulnerable network traffic. This distributed mechanism can be enabled on a per VM and per vNIC of a VM basis with granular rule inspection. As part of this feature set, the NSX Manager is able to download the latest signature packs from the NSX Signature Service. This keeps the NSX Distributed IDS updated with the latest threat signatures in the environment.
Service Insertion and Guest Introspection
- E-W Service Chaining for NFV-SFC at the Edge – The ability to chain multiple services was earlier available only to distributed traffic but is now available for edge traffic. The East-West service chains can now also be extended to redirect edge traffic.
- Disable cloning of NSX Service VMs – Cloning of Service VMs is now prevented from the vSphere Client to prevent malfunctioning of the VMs.
Load Balancing
- Load Balancer Health Check Support for Multiple Monitors and ‘AND' Condition – This enhancement allows multiple active health monitors to be configured as one health monitoring policy. All active health monitors must pass successfully for the member to be considered healthy.
- Connection Drop for Layer 4 and Layer 7 Virtual Servers – Layer 4 Virtual Servers have a new option to allow or deny connections from specified networks. LB rules for Layer 7 Virtual Servers allow Group to be used to specify networks and have a new action “Drop” to drop requests silently instead of returning an HTTP status code.
- IPv6 Support for LB Virtual Servers and Members – Load balancing IPv6 VIP to IPv6 members is supported.
- JSON Web Token Support – Load Balancer can validate JSON Web Token or JWT and grant access based on its payload.
- SSL-passthrough and Dynamic SSL Termination by Load Balancer Rules – Load Balancer can select a pool based on SNI in SSL Client Hello without terminating SSL. Also, it can perform SSL-passthrough, SSL offload or end-to-end SSL based on SNI.
- Load Balancer Extra Large Support – Extra Large form factor is introduced for XLarge Edge for better scale.
- DLB for vSphere with Kubernetes – Distributed Load Balancer is supported for k8s cluster IPs managed by vSphere with Kubernetes. DLB is NOT supported for any other workload types.
VPN
- Intel QAT Support for VPN Bulk Encryption – Intel QAT card is supported to offload VPN bulk encryption on Bare Metal Edge.
- Local egress for L2VPN – Two local gateways can be connected to the stretched network with the same gateway IP address to allow outbound traffic to egress through the local gateway.
- On-demand DPD – On-demand DPD is supported to avoid a short interval of DPD keep-alive while providing a fast detection of a remote failure.
- L2 VPN on Tier-1 LR – L2 VPN service is supported on Tier-1 Gateway.
- Stateful Fail-over for VPN Sessions – IKE SAs and IPsec SAs are synchronized to the standby VPN service in real-time for stateful fail-over.
- PMTU Discovery – PMTU discovery is supported for both L2 and L3 VPN services to avoid packet fragmentation.
Automation, OpenStack and other CMP
- Search API available – Exposes NSX-T Search capabilities (already available in UI) through API. This allows you to craft powerful queries to return NSX-T objects based on their tags, types, names or other attributes and simplify automation. The detailed usage of the Search API is described in the API guide.
- Terraform Provider for NSX-T – Declarative API support – The Terraform Provider offers the capability to configure logical objects from the declarative API for NSX-T on premises. This allows the benefits of Terraform with the flexibility and additional features of NSX-T policy API model. The new resources and data sources allow infrastructure as code by covering a wider range of constructs from networking (Tier-0 Gateway, Tier-1 Gateway, segments), security (centralized and distributed firewall, groups) and services (load balancer, NAT, DHCP). More details are available in the Terraform Provider release notes.
- Ansible Module for NSX-T – Upgrade and Logical object support – The Ansible Modules for NSX-T are enhanced to support upgrade in addition to install. They also allow set up of the environment by configuring Tier-0 Gateway, Tier-1 Gateway, segments and distributed firewall rules from the declarative API. This allows you to automate the setup of its environment, its upgrades and the creation of the base topology. More details are available in the Ansible Module release notes.
- OpenStack Integration Improvements – extended IPv6, VPNaaS support, vRF lite support – The Neutron plugin for NSX-T declarative API expands and covers IPv6 and VPNaaS. The IPv6 implementation adds load balancer support to all the functionality already in previous releases while the VPNaaS allows you to configure from OpenStack IPsec VPNs created in NSX-T. The OpenStack Neutron plugin also has validated the use of a Tier-0 vRF-lite as an External network in addition to the Tier-0, allowing large enterprise and service providers to provide isolation and flexibility with a minimum amount of edge resources. More details are available in the OpenStack Neutron Plugin Release Notes.
Container Networking and Security
- Container Inventory & Monitoring in User Interface – Container cluster, Namespace, Network Policy, Pod level inventory can be visualized in the NSX-T User Interface. Visibility is also provided into co-relation of Container/K8 objects to NSX-T logical objects.
- IPAM Flexibility – The NSX Policy IP Block API has been enhanced to carve out IP subnets of variable sizes. This functionality helps the NSX Container Plugin carve out variable size subnets for Namespaces using Policy API.
- NCP Component Health Monitoring – The NSX Container Plugin and related component health information like NCP Status, NSX Node Agent Status, NSX Hyperbus Agent Status can be monitored using the NSX Manager UI/API.
NSX Cloud
- App-ID and URL Filtering – App-ID and URL feature for Selective Native services in Public Cloud through NSX Cloud is now possible. This expands the scope of workloads/services that can be protected in public cloud using a single consistent policy in NSX Cloud. We are starting with the most commonly used services in AWS and Azure.
- Support for AWS and Azure Gov Clouds – All functionalities of NSX Cloud on commercial clouds (AWS and Azure) are now extended to Gov Cloud (across all gov cloud regions inside the US). Features are subject to API/availability support from the respective public cloud providers.
- Support SLES 12sp3 (SUSE 12 SP3) – Public Cloud VMs that have an agent running SLES 12sp3 are now supported.
- Support for VPNs in agentless VPCs and VNets – VPN connections can be established between Edges that are located on premises, or in a public cloud (AWS and Azure), even if the VPCs and VNETs are running in agentless mode.
- Improved VPN Performance & Throughput – For a given packet size, VM family and VPN scale in AWS and Azure, NSX offers more than 2x the throughput than that offered by VGWs from Public Cloud providers.
Operations
- Support for both Thin and Thick Disk Mode – The NSX Manager and NSX Intelligence appliances now support both thin and thick mode and provide that choice upon deployment.
- Increased disk size of NSX Manager – Starting in NSX-T 3.0, the disk size of NSX Manager will be increasing from 200 GB to 300 GB (per NSX Manager node in a cluster). During a new NSX Manager installation, please ensure that the underlying datastore has adequate disk space. During an upgrade to NSX-T 3.0, please ensure that the new datastore has been added prior to upgrading NSX Manager.
- Reduction of VIB size in NSX-T – NSX-T 3.0 has a smaller VIB footprint in all NSX host installations so that you are able to install ESX and other 3rd party VIBs along with NSX on their hypervisors.
- Support for Federation Upgrade – With NSX Federation, the admin can upgrade Global Manager and Local Manager asynchronously, following the detailed compatibility matrix in the Upgrade Guide.
- Periodical MTU/VLAN Healthcheck for N-vDS – Healthcheck is now available for the NSX host switch, i.e., N-vDS.
- Non-disruptive in-place upgrades – More enhancements have been made to the in-place upgrades of NSX Transport Nodes with fewer caveats, details of which are available in the Upgrade Guide.
- Traceflow Policy support – The traceflow debugging tool is now available under the Policy tab (previously known as the Simplified tab).
- Ability to follow TN install at a per-host level and provide progress bar – An admin can view in the UI a detailed progress of the installation of NSX on hypervisors.
- Traceflow observations for Spoofguard – The traceflow debugging tool will now show any packet drops that may happen due to the Spoof-guard feature.
- Ability to automatically uninstall NSX when a host leaves a VC cluster – NSX will be automatically uninstalled once a user moves a Transport Node to outside a vSphere cluster. More details on this are available in the Upgrade Guide.
- Central Appliance Configuration – NSX now supports the ability to configure settings that are common across NSX Managers and Edge Nodes in a centralized way instead of requiring the administrator to use the local CLI configuration on a per node basis.
- SNMP Traps – NSX now supports the ability to generate SNMP trap notifications from the NSX Manager, Edge Node and the NSX components of supported hypervisor hosts. These trap notifications are for events and alarms generated by NSX. The NSX MIB is provided as part of the deliverables of NSX on the NSX download site.
- NSX Alarm Framework and System Alarms/Events – With this release of NSX, the product now supports an alarm framework that improves the delivery of alerts and alarms to aid in running NSX successfully in a production environment. A list of supported alarms is provided in the NSX documentation.
Inventory
- NSX Tag Listing and Bulk Action Support – NSX-T adds UI/API support for listing NSX Tags, and assigning/un-assigning NSX Tags to multiple virtual machines.
- Physical Servers Listing – NSX-T adds UI support for listing physical servers.
Usability and User Interface
- Graphical Visualization of Network Topology – Provides an interactive network topology diagram of Tier 0 Gateways, Tier 1 Gateways, Segments, and connected workloads (VMs, Containers), with the ability to export to PDF.
- New Getting Started Wizards – A new getting started wizard is introduced for preparing clusters for VLAN Micro-Segmentation in three easy steps.
- Quick Access to Actions and Alarms from Search Results – Enhanced search results page to include quick access to relevant actions and alarms. Added more search criteria across Networking, Security, Inventory, and System objects.
- User Interface Preferences for NSX Policy versus Manager Modes – You can switch between NSX Policy mode and NSX Manager mode within the user interface, as well as control the default display. By default, new installations display the UI in NSX Policy mode, and the UI Mode switcher is hidden. Environments that contain objects created through NSX Manager mode (such as from NSX upgrades or cloud management platforms) by default display the UI Mode switcher in the top right-hand corner of the UI.
- UI Design Improvements for System Appliances Overview – Improved UI design layout for displaying resource activity and operational status of NSX system appliances.
Licensing
- New VMware NSX Data Center Licenses – Adds support for a new Add-On license, VMware NSX Data Center Distributed Threat Prevention, introduced in April 2020, and continues to support NSX Data Center licenses (Standard, Professional, Advanced, Enterprise Plus, Remote Office Branch Office) introduced in June 2018, and previous VMware NSX for vSphere license keys. Additionally, the license usage report captures micro-segmentation, federation usage in core, CPU, CCU and VM metrics. Distributed Intrusion Detection usage is per CPU basis. See VMware knowledge base article 52462 for more information about NSX licenses.
- vShield Endpoint Management Support – NSX-T supports management of vShield Endpoint anti-virus offload capabilities. For more information, see VMware knowledge base article 2110078.
- Change in default license & evaluation key distribution – The default license upon install is “NSX for vShield Endpoint”, which enables use of NSX for deploying and managing vShield Endpoint for anti-virus offload capability only. Evaluation license keys can be requested through VMware sales or the VMware evaluation web site.
- NSX Evaluation License Expiration – Upon expiration of the 60-day NSX Evaluation license, you can delete but will not be allowed to create or edit objects.
AAA and Platform Security
- Native AD-based Authentication via LDAP – This feature adds support for NSX administrators and users to authenticate and on-board to the NSX-T platform via direct AD (Active Directory) integration with LDAP (Lightweight Directory Access Protocol). The majority of enterprise/business user credentials are stored in Microsoft-based AD. Direct AD configuration simplifies user on-boarding without the hassle of configuring additional identity systems where its use is not suitable or adds operational complexity. In addition, this feature allows consumption of NSX-T RBAC capabilities with powerful search options to identify relevant AD users/groups for role assignments. Both secure (LDAPS, startTLS) and regular LDAP configurations are supported. NSX-T customers now have the flexible option to either configure Workspace One Access (formerly VIDM) or native AD configuration, or in some cases, a combination of VIDM and direct AD configuration, as suitable, to meet their operational needs.
- Integration with OpenLDAP – In addition to supporting native AD integration, NSX-T 3.0 offers the flexibility to authenticate and on-board users who are using OpenLDAP directory services.
- AAA for NSX-T features in vSphere with Kubernetes – Users running containerized applications and Kubernetes features in vSphere 7.0 appliance can leverage and troubleshoot a limited number of NSX networking features without additional authentication via vSphere appliance.
- “On-behalf of” API feature – Allows tracking of derived user actions, especially when using Principle Identity (PI) or Service Accounts to perform API calls, by indicating if the API action was invoked on-behalf of another NSX user. Any API call with the “X-NSX-EUSER: <username>” header will result in audit log with additional user activity information – “euser=<username>”. This feature is useful for in-depth user-accounting, i.e., maintaining a rich audit trail with contextual data on “who” did “what.”
- Session Based Authentication for Remote Users – NSX-T 3.0 has enhanced authentication capabilities to allow both local and remote users to create cookie-based sessions – to authenticate and persist API based activities. The new enhancements simplify session creation for API users and facilitates efficient API operations and security compliance, by avoiding repeated authentication. Both VIDM- and LDAP-based remote users are supported.
- Separate Audit Log for API Write Calls – This feature supports the ability to retrieve audit log content that solely contains information on API write calls. Improves readability of audit trail by tracking “before & “after” states.
- Enable/Disable Cookie-based Authentication – NSX admins can now turn off cookie (session-based) based API authentication to improve the security posture of NSX-T platform operations. Cookie-based authentication is available by default and can be re-enabled after being turned off.
- Enable/Disable Basic Authentication – NSX admins concerned about secure use of basic authentication can now disable (or re-enable) basic authentication for API and CLI use. By default, basic authentication support is available.
NSX Data Center for vSphere to NSX-T Data Center Migration
- Migration Coordinator with Maintenance Mode – When you are using vSphere 7.0 and vDS 7.0, the Migration Coordinator will migrate hosts to an existing vDS (version 7.0) instead of migrating to an N-VDS. This minimizes the impact of the migration on the customer environment.
- Migration from NSX Data Center for vSphere to NSX-T Data Center using vDS 7.0 – The NSX Migration Coordinator now supports maintenance mode for the final host migration step. This mode allows the migration of virtual machines from a host prior to converting the host from NSX for vSphere to NSX-T. By placing a host into maintenance mode, a virtual machine can be migrated using vMotion to minimize the impact to the data traffic to and from the virtual machine.
NSX Intelligence
- New features and feature enhancements introduced in NSX Intelligence 1.1 are detailed in the VMware NSX Intelligence 1.1 Release Notes.
- Documentation to help you install, configure, update, use, and manage NSX Intelligence is now separately available on NSX Intelligence Documentation.
Compatibility and System Requirements
For compatibility and system requirements information, see the NSX-T Data Center Installation Guide.
API Deprecations and Behavior Changes
- Removal of Application Discovery – This feature has been deprecated and removed.
- Change in “Advanced Networking and Security” UI upon Upgrading from NSX-T 2.4 and 2.5 – If you are upgrading from NSX-T Data Center 2.4 and 2.5, the menu options that were found under the “Advanced Networking & Security” UI tab are available in NSX-T Data Center 3.0 by clicking “Manager” mode.
- API Deprecation Policy – VMware now publishes our API deprecation policy in the NSX API Guide to help customers who automate with NSX understand which APIs are considered deprecated and when they will be removed from the product in the future.
API and CLI Resources
See code.vmware.com to use the NSX-T Data Center APIs or CLIs for automation.
The API documentation is available from the API Reference tab. The CLI documentation is available from the Documentation tab.
Available Languages
NSX-T Data Center has been localized into multiple languages: English, German, French, Japanese, Simplified Chinese, Korean, Traditional Chinese, and Spanish. Because NSX-T Data Center localization utilizes the browser language settings, ensure that your settings match the desired language.
Links:
- VMware NSX-T Data Center 3.0.0 Release Notes
- Download Here
More from ESX Virtualization
- vSphere 7.0 Download Now Available
- vSphere 7.0 Page [All details about vSphere and related products here]
- VMware vSphere 7.0 Announced – vCenter Server Details
- VMware vSphere 7.0 DRS Improvements – What's New
- Upgrade from ESXi 6.7 to 7.0 ESXi Free
- What is VMware Skyline?
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)