This is the first VCP6.5-DCV Objective 1 from the exam guide for preparation for VMware VCP6.5-DCV Datacenter virtualization exam. Find all exam topics directly on our new VCP6.5-DCV Study Guide Page. Note that it is a work in progress which started just recently so we need to add more content to it.
VMware certification exam is important to have when you start with the IT, data center administration. It's important to have it on your CV, but that's not all.
During your career, you'll certainly need to study further. Stay up to date with the knowledge. It's a continuous process where the next step for some is VCAP, while for others even VCDX as an ultimate VMware certification.
Note that VCP certs expire after 2 years, where VCAPs doesn't. This might also be a reason to continue to study and pass a higher, more difficult exams. VCAP 6.5 – design and (or) VCAP 6.5 deploy exams are the ones you might wish to pass after passing your VCP.
Tip: There is a new VCP6.5-DCV Study Guide Page on the blog. Accessible through the main menu Study Guides > VCP6.5-DCV
You can download your free copy via this link – Download Free VCP6.5-DCV Study Guide at Nakivo.
Let's get back to our today's chapter – VCP6.5-DCV Objective 1 – Configure and Administer Role-based Access Control. Compared to the VCP6-DCV Study guide, this chapter is a little bit more demanding, with more topics to cover.
While the VCP6-DCV chapter has had only 7 topics, within the VCP6.5-DCV as you can see, there are 11 topics below. Links on this page go directly to the paragraph (not external links).
VCP6.5-DCV Objective 1 – Configure and Administer Role-based Access Control
- Compare and contrast propagated and explicit permission assignments
- View/Sort/Export user and group lists
- Add/Modify/Remove permissions for users and groups on vCenter Server inventory objects
- Determine how permissions are applied and inherited in vCenter Server
- Create/Clone/Edit vCenter Server Roles
- Configure VMware Identity Sources
- Apply a role to a User/Group and to an object or group of objects
- Change permission validation settings
- Determine the appropriate set of privileges for common tasks in vCenter Server
- Compare and contrast default system/sample roles
- Determine the correct permissions needed to integrate vCenter Server with other VMware products
Compare and contrast propagated and explicit permission assignments
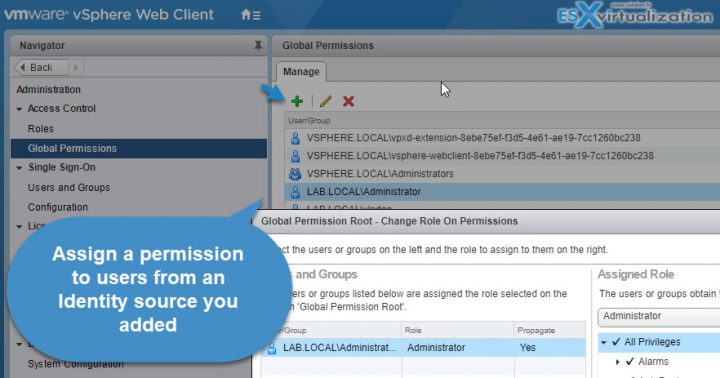
To check the propagated and explicit permission assignments, we have to connect to our vCenter server > Global Administration. But before doing this, it's important to know the difference between Permissions and Users and Groups.
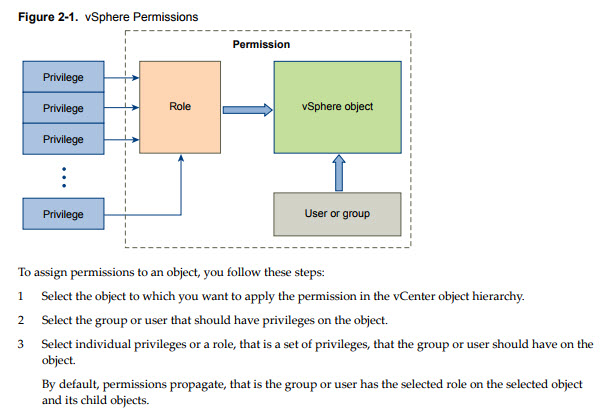
- Permissions – each object in the vCenter hierarchy has associated permissions. Each permission
- Privileges – access controls to the resource. You group privileges into roles, which are mapped to users or groups.
- Users and groups – pretty obvious. Only users authenticated through Single Sign-ON (SSO) can be given some privileges. Users must be defined within the SSO or users from external identity sources such as Microsoft AD.
- Roles – what is a role? A role allows you to assign permission to an object. Administrator, Resource Pool administrator, etc are predefined roles. You can clone them or change them (except Administrator).
When you assign a permission to an object, you can choose whether the permission propagates down the object hierarchy. You set propagation for each permission. Propagation is not universally applied. Permissions defined for a child object always override the permissions that are propagated from parent objects.
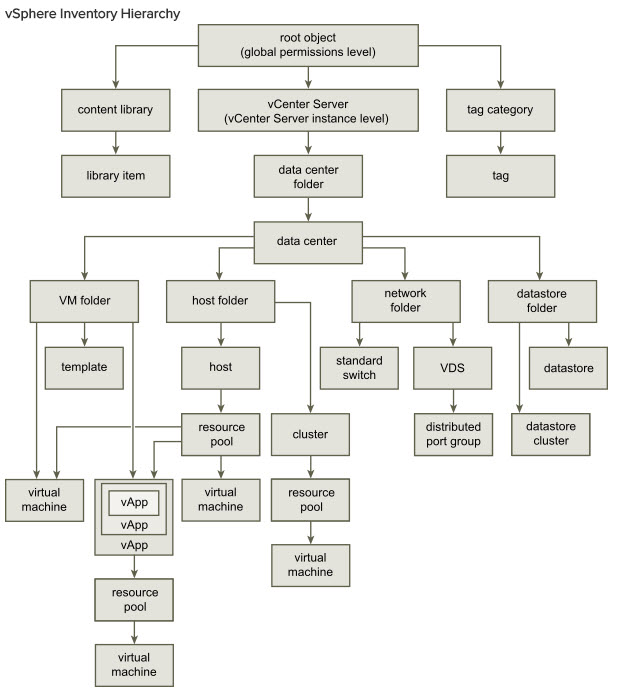
The image below (from vSphere 6.5 Security guide) illustrates the inventory hierarchy and the paths by which permissions can propagate
View/Sort/Export user and group lists
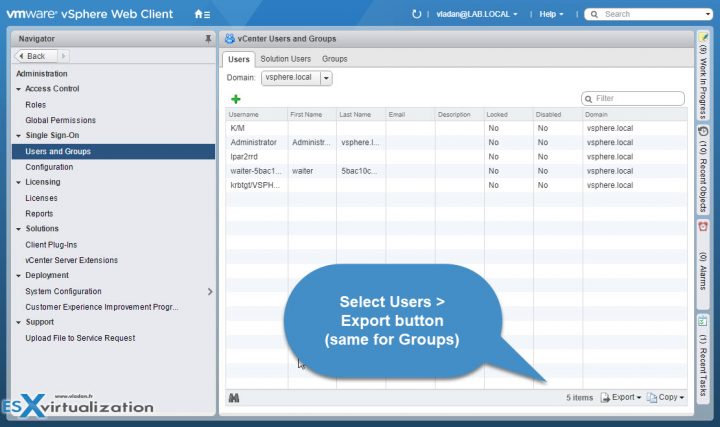
Home > Administration > SSO > Users and Groups. You can click the top of each column to sort username, view the details or add an additional user (group).
User lists can be exported via the export button in the bottom right of the Users and Groups page, located under Administration > SSO. Select the user(s) by holding shift or CTRL key for multiple, then click the export button.
Add/Modify/Remove permissions for users and groups on vCenter Server inventory objects
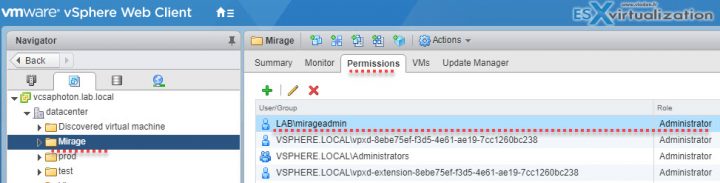
To Add/Modify/Remove permission for a user and group from vCenter inventory you have to Select an object from the inventory > click Permissions TAB > there you can add, edit, and remove permissions.
Example:
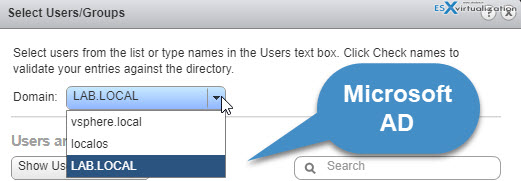
Click Home > Host and clusters (or VMs and templates view from where you can assign permission to the other node, folder, cluster, datacenter > Select vCenter Server (or other nodes…) > Permissions TAB > Add new permission. From there you can pick a user/group from SSO domain or from other identity sources. Use the drop-down selection to pick an AD user for example.
For example, MirageAdmin user from AD has an Administrator role (with it's associated permissions) to the whole Mirage folder within the vCenter hierarchy…. I have worked on the VMware Mirage Guide recently.
It really depends on your needs. You can also create a custom role and then assign a user to this role.
Where possible, assign a role to a group rather than individual users to grant privileges to that group.
Grant permissions only on the objects where they are needed, and assign privileges only to users or groups that must have them.
If you assign a restrictive role to a group, check that the group does not contain the Administrator user or other users with administrative privileges. If not, the admin won't be happy…
The best is to group objects into folders, (including hosts). Then you can assign permissions to folders containing hosts and other objects.
In most cases, enable propagation when you assign permissions to an object. This ensures that when new objects are inserted into the inventory hierarchy, they inherit permissions.
Mask specific areas of the vCenter hierarchy – Use the No Access role to mask specific areas of the hierarchy if you do not want for certain users or groups to have access to the objects in that part of the object hierarchy.
Determine how permissions are applied and inherited in vCenter Server
From vSphere security documentation web page we have found this image showing the vSphere Inventory Hierarchy:
After assigning a permission to an object, on the same page you can check the box to propagate permissions down the object hierarchy. You have to set the propagation for each permission. (or not).
Permissions defined for a child object always override the permissions that are propagated from parent objects.
Most inventory objects inherit permissions from a single parent object in the hierarchy. For example, a datastore inherits permissions from either its parent datastore folder or parent data center. Virtual machines inherit permissions from both the parent virtual machine folder and the parent host, cluster, or resource pool simultaneously.
Create/Clone/Edit vCenter Server Roles
To edit, create or clone vCenter roles it’s necessary to use vSphere Web client > Administration > Roles OR Home > Roles. Default roles are:
- Administrator
- Read-Only
- No Access
To clone role click the icon…
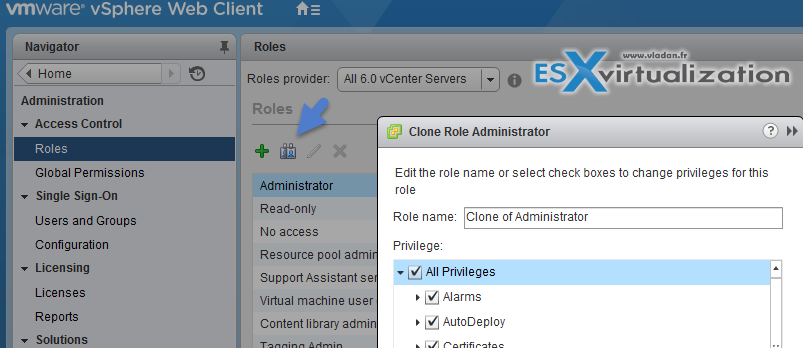
- Log in to vCenter Server with the vSphere Web Client.
- Select Home, click Administration, and click Roles.
- Select a role, and click the Clone role action icon.
- Type a name for the cloned role.
- Select or deselect privileges for the role and click OK.
When you edit a role, you can change the privileges selected for that role. When completed, these privileges are applied to any user or group that is assigned the edited role.
Configure VMware Identity Sources
During the login process, the user tries to log in to vCenter, and it's vCenter Single Sign-On who does the verification of default identity source whether that user can authenticate. When a user logs in and enters the domain name in the login screen, vCenter SSO checks the domain to see, whether the domain has been added as an identity source. If yes, the user can succesfully login.
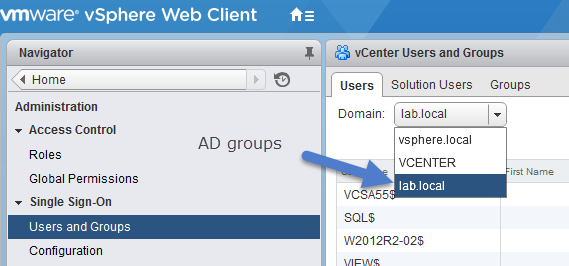
Home > Administration > Single Sign-ON > Configuration > Identity sources > Add
The user administrator@vsphere.local can perform tasks that are associated with services included with the Platform Services Controller.
After installation the only identity sources and users are:
- Local OS – All local operating system users. If you are upgrading, those local OS users who can already authenticate can continue to authenticate. Using the local OS identity source does not make sense in environments that use an embedded Platform Services Controller.
- vsphere.local – Contains the vCenter Single Sign-On internal users.
After adding the Microsoft AD as an identity source, all users can be authenticated but have the No access role. You can, however, change it (login as [email protected]) and you can assign to users or groups of users privileges that enable them to log in to vCenter Server and view and manage objects.
Apply a role to a User/Group and to an object or group of object
A role is a predefined set of privileges. A role allows you to assign permission to an object. Administrator, Resource Pool administrator, etc are predefined roles. Privileges define rights to perform actions and read properties. For example, the Virtual Machine Administrator role allows a user to read and change virtual machine attributes
vCenter Server has some system roles and some sample roles you can play with.
- System Roles – System roles are permanent, not editable. You cannot edit the privileges associated with these roles.
- Sample roles – Sample roles are useful because they have been created for frequently performed tasks. Those roles are modifiable, so you are allowed to clone, modify, or remove these roles.
Change permission validation settings
vCenter Server systems that use a directory service regularly validate users and groups against the user directory domain. Validation occurs at regular intervals specified in the vCenter Server settings;
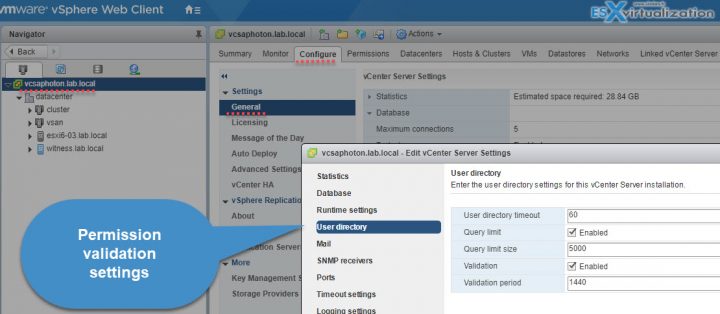
Home > Hosts and clusters > Select vCenter server > Configure > Settings > General > Edit and select User directory > Change the values as needed.
The Options:
- User directory timeout – Timeout interval, in seconds, for connecting to the Active Directory server. This value specifies the maximum amount of time vCenter Server allows a search to run on the selected domain. Searching large domains can take a long time.
- Query limit – Select the checkbox to set a maximum number of users and groups that vCenter Server displays.
- Query limit size – This is a maximum number of users and groups from the selected domain that vCenter Server displays in the Select Users or Groups dialog box. If you enter 0 (zero), all users and groups appear.
- Validation – Deselect the checkbox to disable validation
- Validation Period – Specifies how often vCenter Server validates permissions, in minutes.
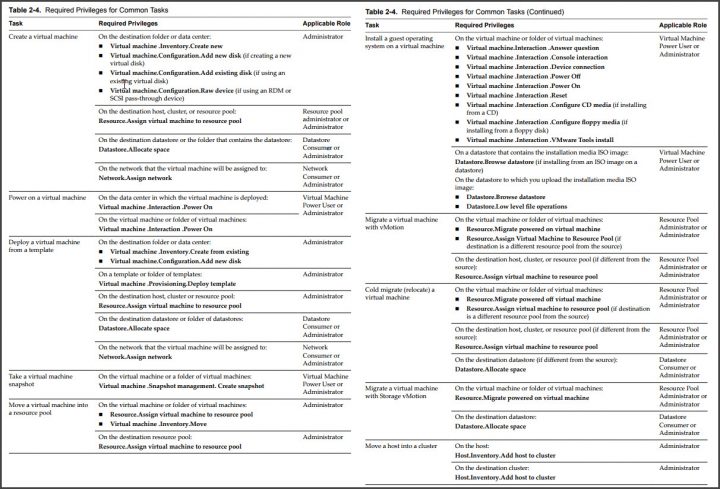
Determine the appropriate set of privileges for common tasks in vCenter Server
Many tasks require permissions on multiple objects in the inventory. If the user who aĴempts to perform the task only has privileges on one object, the task cannot complete successfully.
Any operation that consumes storage space requires the Datastore.Allocate Space privilege on the target datastore, and the privilege to perform the operation itself. You must have these privileges, for example, when creating a virtual disk or taking a snapshot.
Moving an object in the inventory hierarchy requires appropriate privileges on the object itself, the source parent object (such as a folder or cluster), and the destination parent object.
Each host and cluster has its own implicit resource pool that contains all the resources of that host or cluster. Deploying a virtual machine directly to a host or cluster requires the Resource.Assign Virtual Machine to Resource Pool privilege.
Screenshot directly from the vSphere 6.5 security guide
Compare and contrast default system/sample roles
vCenter Server provides a few default roles. You cannot change the privileges associated with the default roles. The default roles are organized as a hierarchy. Each role inherits the privileges of the previous role.
For example, the Administrator role inherits the privileges of the Read Only role. Roles that you create do not inherit privileges from any of the system roles.
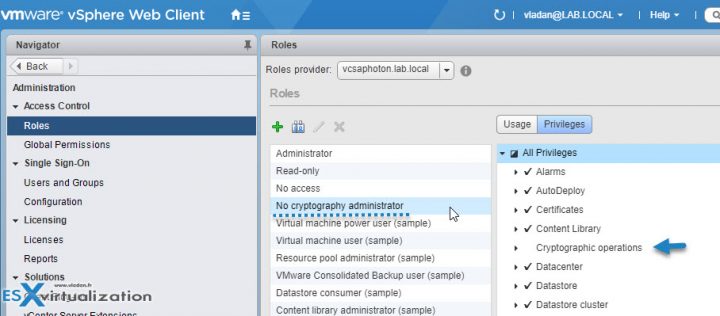
Administrator Role – Users with the Administrator role for an object are allowed to view and perform all actions on the object. This role also includes all privileges inherent in the Read Only role. If you are acting in the Administrator role on an object, you can assign privileges to individual users and groups. If you are acting in the Administrator role in vCenter Server, you can assign privileges to users and groups in the default vCenter Single Sign-On identity source. Supported identity services include Windows Active Directory and OpenLDAP 2.4.
By default, the [email protected] user has the Administrator role on both vCenter Single Sign-On and vCenter Server after installation. That user can then associate other users with the Administrator role on vCenter Server.
No Cryptography Administrator Role – Users with the No cryptography administrator role for an object have the same privileges as users with the Administrator role, except for Cryptographic operations privileges. This role allows administrators to designate other administrators that cannot encrypt or decrypt virtual machines or access encrypted data, but that can perform all other administrative tasks.
No Access Role – Users with the No Access role for an object cannot view or change the object in any way. New users and groups are assigned this role by default. You can change the role on an object-by-object basis.
The administrator of the vCenter Single Sign-On domain, [email protected] by default, the root user, and vpxuser are assigned the Administrator role by default. Other users are assigned the No Access role by default.
Read Only Role – Users with the Read Only role for an object are allowed to view the state of the object and details about the object. For example, users with this role can view virtual machine, host, and resource pool aĴributesǰ but cannot view the remote console for a host. All actions through the menus and toolbars are disallowed.
Determine the correct permissions needed to integrate vCenter Server with other VMware products
The detailed tables can be found in the vSphere 6.5 security document (Chapter 11), there are too many to list them all here. They list the default privileges that, when selected for a role, can be paired with a user and assigned to an object.
vCenter Server extensions might define additional privileges not even listed in the PDF. Check the vSphere 6.5 security guide.
There is more to come, more to study. Check our VCP6.5-DCV Study Guide Page.
More from ESX Virtualization:
- What Is VMware ESXi Lockdown Mode?
- How to reset Single Sign-On (SSO) password in vSphere
- Patch vCenter Server Appliance configured with High Availability (HA)
- V2V Migration with VMware – 5 Top Tips
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)