VMware has rolled out new update on vCenter server 5.5 U1a. This update fixes a Heartbleed bug in OpenSSL third party library. HearbleThere are no new features in this release and only vCenter server and vCenter server appliance are on the list of updated products. The bug was affecting a Windows based vCenter server and VMware Client integration plugin . vCSA (Linux based vCenter server appliance) is not affected, but the product got an update as well passing from build 1624811 (5.5 U1) to 1750781 (5.5 U1a).
The procefure of updating of vCenter certificates, Single sign-on directory service and is well documented and once SSO is upgraded and new certificates are generated, a new password for [email protected] (default admin for SSO) must be created. Details are in the KB – Resolving OpenSSL Heartbleed for VMware vCenter Server 5.5
Quote from the release notes:
- Vulnerability in OpenSSL third party library
The OpenSSL library is updated to version openssl-1.0.1g to resolve the Heartbleed issue.
The Common Vulnerabilities and Exposures Project (cve.mitre.org) has assigned the nameCVE-2014-0160 to this issue.
Details on this vulnerability can be found in VMware Security Advisory VMSA-2014-0004.Note:- After upgrading to vCenter Server 5.5 Update 1a, to remediate the issue, you need to replace certificates and reset passwords. For more information, see Resolving OpenSSL Heartbleed for vCenter Server 5.5 (KB 2076692).
- After upgrading the vSphere Web Client, you also need to update the Client Integration plugin by performing the following steps:
- Open a web browser and enter the URL for the vSphere Web Client:https://client-hostname:port/vsphere-client.
- At the bottom of the vSphere Web Client login page, click Upgrade the Client Integration Plug-in.
- Download and install the Client Integration Plug-in.
Since some users are currently running vCenter sever 5.5 (a, b or c version) and others runs on vCenter server 5.5 U1. There are different upgrade paths concerning vCenter server and also the certificates, and changing of passwords for SSO admin and other users (if created) on the SSO.
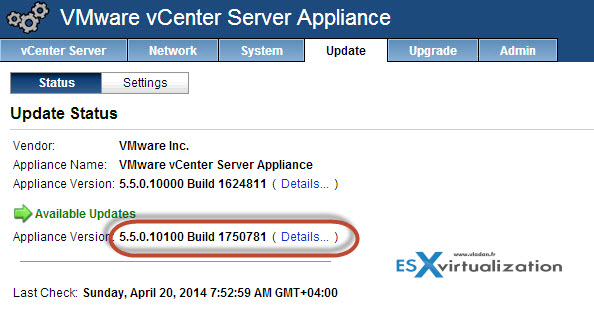
Screenshot from my lab showing the change in release builds.
Quote from the Resolving OpenSSL Heartbleed for VMware vCenter Server 5.5 KB article:
There are two vCenter Server 5.5. releases issued to overcome the issue:
- If you are currently running vCenter Server 5.5 GA build 1312298, 1378903 or 1476327 you should upgrade to vCenter Server 5.5.0c build 1750596.
Note: vCenter Server 5.5.0c should not be updated to vCenter Server 5.5 Update 1. You can upgrade vCenter Server 5.5.0c to vCenter Server 5.5 Update 1a build 1750787.
- If you are currently running vCenter Server 5.5 Update 1 build 1623101 you should upgrade to vCenter Server 5.5 Update 1a 1750787
Well this is certainly interesting as most users aren't yet on the latest 5.5 U1 or not even on the 5.5 GA. However it's a fast reaction from VMware part to fix a critical vulnerability affecting a critical (vCenter server ) system.
Links:
- Resolving OpenSSL Heartbleed for VMware vCenter Server 5.5
- VMware Release Notes of the Update for vCenter server 5.5 U1a
- VMware Product Updates