As you might hear, there is a new flaw in Apache Log4j, a Java library for logging error messages in applications. This vulnerability is the most high-profile security vulnerability on the internet right now as it impacts many different platforms that run Java.
VMware strongly recommends that organizations who are impacted by CVE-2021-44228 review the guidance in the context of all workloads and other systems. This issue affects billions of systems, software packages, and devices globally.
How does it work? The hacker can send a request to any endpoint which writes its content into the application's log file. The application can get rerouted, and then load and execute untrusted code from a malicious external server.
If an attacker manages to exploit it on a vulnerable server, they basically are able to execute arbitrary code and potentially take full control of the system. This information has been published publicly as Proof-of-Concept and apparently the vulnerability is easy to exploit so this makes this situation particularly dangerous.
Log4Shell Vulnerability Scan
Runecast offers the possibility to detect this issue within your environment. Simply go to this page and request a free scan. You'll be offered a 7 day Runecast trial for unlimited assets. Please note that this applies only to qualified organizations so putting in some erroneous information won't cut it. I'd imagine that trying it with some free e-mail accounts won't be useful and most likely rejected as well. So please don't do that. Runecast folks simply trying to help you to discover this vulnerability within your environment.
Runecast customers can simply update their Runecast VA to the latest version and initiate a scan as the definition of remote code execution vulnerability CVE-2021-44228 is now integrated into the product.
Quote from Runecast blog:
The latest version of Runecast (6.0.1.0) has this VMSA implemented and is available as an update. Where automatic updates are enabled, Runecast users should already have this VMSA covered, with offline updates available through the Runecast customer portal as usual. There were a number of affected VMware products that we support: vCenter Server, Horizon, NSX-T, but please note, the list might be expanded as VMware evaluates the vulnerability.
Runecast Product Update
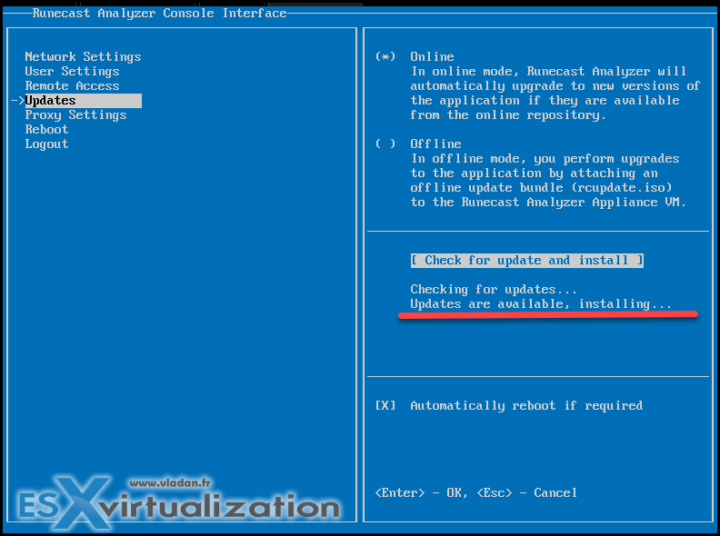
If your Runecast product is not set to update automatically, you can do it manually via the console. (F1 for login)/
BTW, do you remember the console default login and password?
- login: rcadmin
- pass: admin
Preferably to change into something different of course.
The appliance reboots itself automatically.
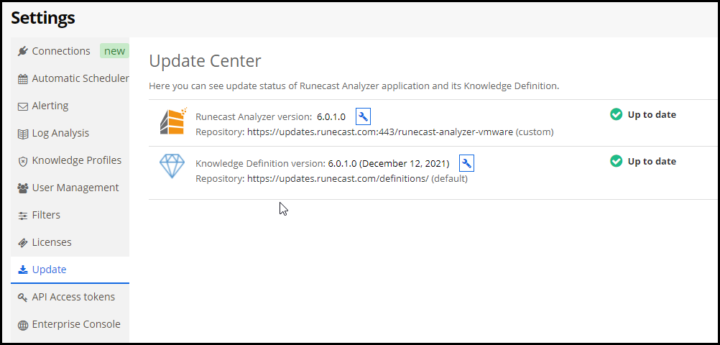
When you connect via UI, you can check that you're running the latest Runecast product and the knowledge definition version within the Settings > Update section.
Which products are affected?
VMware reacted quickly and released a new KB 87068 covering the details. The long list of products that are currently vulnerable can be found here (currently 40 VMware products, but still in evolution !!).
With each product, VMware has a workaround that can be applied manually or automatically. The list of products and the workaround is pretty impressive. VMware is working towards resolutions and will be issuing patches for each of their products itself.
The latest updates on the matter are also covered via Apache Software Foundation which is maintaining the log4j components. They recently issued an updated workaround for CVE-2021-44228, as well as guidance on a second vulnerability, CVE-2021-45046. New information is often learned during an incident, requiring a change in strategy.
Final Words
If you're using Apache or Java within your environment within any of the VMware products, you should definitely be interested as this vulnerability is here. The vulnerability was discovered in December (this month) so it's pretty new. Many admins will “sleep” through by ignoring it and that's the danger.
The Common Vulnerabilities and Exposures (CVEs) and VMware Security Advisories (VMSA) are not there to be pretty but shall be taken seriously especially with flaws affecting so many products. Runecast's expertise via detection of vulnerabilities, misconfiguration, and threads allows admins to have a central point of security and be aware of steps that needs to be taken in order to mitigate the risk by following VMware KB articles and workarounds.
Request your Log4Shell Vulnerability scan here.
Source: Runecast Blog