Regular readers of our blog certainly noticed few articles and one product review of Runecast Analyzer for VMware vSphere environments. This product correlates VMware vSphere KB articles to your environment and points out misconfigurations, vulnerabilities or shows the best practices which should be applied to your vSphere environment in order to be not only fully protected, but also to avoid you many hours or searching and tweaking your vSphere infrastructure.
Today there is a big news coming from Runecast, which just released a new version, 1.6.5. This release is able to detect the latest chip/CPU vulnerabilities which makes a lot of buzz since about a week. In fact, Spectre or Meltdown can be detected by Runecast Analyzer.
Runecast exposes potential issues before they cause major outages. Runecast also uses the vSphere Security Hardening guides and Best Practices to scan your VMware infrastructure for compliance. Runecast updates itself automatically.
The updates are very frequent and as soon as new VMware KB articles are updated, the product takes it into consideration and matches this update with your environment. So your environment's vulnerabilities, best practices or misconfigurations are detected immediately. You have always up to date information about your environment without going to seek if you're impacted and if a solution exists.
Runecast Analyzer 1.6.5 – What's New?
– This update brings an important check of recent worldwide chip/CPU vulnerabilities called Meltdown and Spectre
– Added new definitions (KB)
– Minor bug-fixes on reports
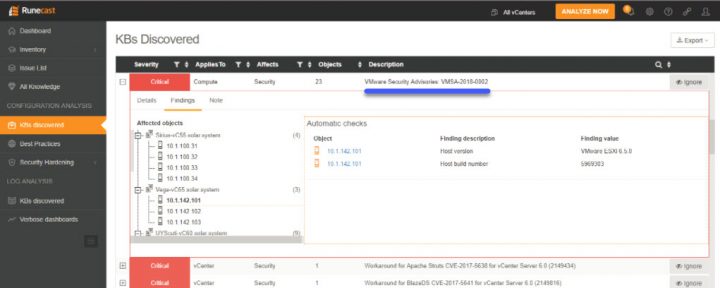
Screenshot from Runecast's blog post showing the VMware KB concerning Spectre and Meltdown vulnerabilities.
If you haven't heard about Runecast yet, I'd highly recommend taking a look at one of our previous posts or the product review (sponsored).
More about Runecast Analyzer by ESX Virtualization:
- Runecast Analyzer – working with the product
- Runecast Analyzer Product Review [Sponsored]
- Runecast Analyzer 1.6 with New REST API and vSphere Web Client Plugin
To remind you, Spectre or Meltdown are vulnerabilities in the Intel, AMD and ARM processors. A VMware patch has to be applied – VMSA-2018-0002 for vSphere 5.5, 6.0 and 6.5.
Quote:
CPU data cache timing can be abused to efficiently leak information out of miss-speculated CPU execution, leading to (at worst) arbitrary virtual memory read vulnerabilities across local security boundaries in various contexts. (Speculative execution is an automatic and inherent CPU performance optimization used in all modern processors.) ESXi, Workstation and Fusion are vulnerable to Bounds Check Bypass and Branch Target Injection issues resulting from this vulnerability.
There are many KB articles which are released by VMware. Those frequent updates is quite impossible to track manually. Also, there are new practices which gets updated and new ones added on regular basis. Lastly, there are those hardening guides from VMware.
You as an admin don't have time to read everything and apply to your environment every day. If you're running VMware environment in your organization, Runecast Analyzer gives you more freedom by anticipating PSODs, misconfiguration, performance bottlenecks and follows best practices.
Check out Runecast Analyzer.
Source: Runecast blog
More from ESX Virtualization
- VCP6.5-DCV Study Guide
- VMware Virtual Hardware Performance Optimization Tips
- Three Simple Steps to Install 3CX Debian Appliance
- Ditch Your HDDs For ACloudA Gateway
- What is VMware vSphere Update Manager?
- VMware vSphere Client Download Page
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)