Veeam Backup repositories (but not only Veeam's) are one of the principal targets of ransomware. When your backups are wiped out or encrypted, you're left with nothing to restore. Designing your backup infrastructure against ransomware attacks is one of the keys in order to succeed (or rather not fail) when dealing with ransomware attacks.
When you detect that your company was hit by ransomware, you can be sure that the bad guys will go after your backup files, no matter what. How to protect those files? How to protect your backup infrastructure? How to architect it to be safe? In this post, we'll give you some practical tips to protect your Backup Repositories.
3-2-1-1-0 rule: Three different copies of data, two different media, one of which is off-site. That’s where the rule starts, have comprehensive ransomware protection with at least one copy being immutable and zero surprises with recovery verification. Use Copy Jobs and/or Replication as an additional layer of protection. It's easy to set up a secondary site with a single ESXi which will be used as a target for your most critical VM's replicas.
Storage Snapshots can save you – Many SAN devices support storage snapshots. Use it! Take storage snapshots on backup storage if possible. If the storage device holding backups supports this capability it may be definitely worth using this feature to prevent ransomware attacks!
Stay away from Microsoft AD – Veeam Backup Server should stay away from your Microsoft Active Directory (AD) Domain. If you're getting attacked, most likely they'll go after your Domain admin or privileged credentials to make as much damage as possible on maximum systems within your organization.
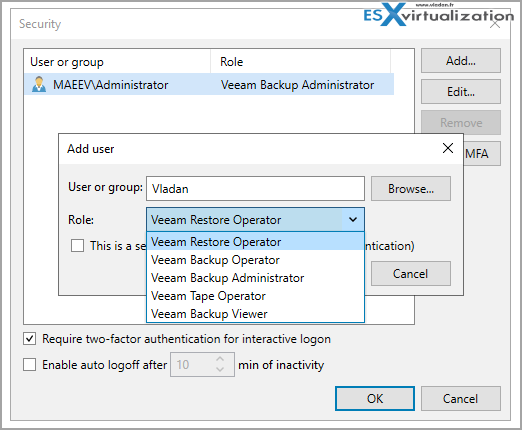
Separate user accounts – By default, Veeam is configured to allow anyone in the local administrator's group full access to the Veeam console. Veeam has separate roles to assign to each user depending on what job they will be performing.
It is also important to follow proper password change policies for accounts that have access to do operations in Veeam. This is especially the case if someone leaves the company, as it is time to change the password.
Do Not use RDP on the Veeam Backup server – Why? It's because it's more secure to install a Veeam Backup console for day-to-day operations. Also, you can use ILO, Drac, iPMI to remote access your server. Or you can go directly to the server room and from the console do your patching, upgrading etc.
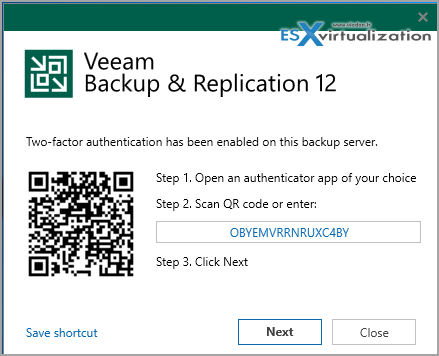
Use Multi-factor authentication – de facto a standard nowadays. Veeam's latest version 12 allows directly enabling MFA on an account and login to the Veeam console. Even if someone has access to your Veeam server, he/she will not be able to start your Veeam Backup console and do possible damage.
Let Veeam Backup Server be only a backup server – It's fairly often, especially with small businesses, that I see that the Veeam backup server has to hold other roles, such as file server, WSUS, app-server…. Not good.
Close Windows Firewall ports except the ones needed by Veeam – Keep the firewall on for all domains (public, private, and if applicable domain). Check the help page at Veeam here for those necessary ports.
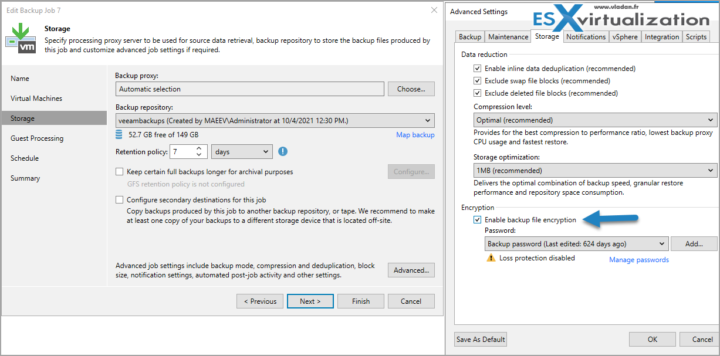
Encrypt backups – you might think that encrypting your backups is not necessary. I'd say, it's an extra layer of protection as attacker if he/she get access to the backup files, those will be unreadable so it will be much harder to access your data. However, it will not prevent the attacker (if he's already in your system) from wiping those backups out, even encrypted.
Edit your job > Storage > Advanced > Storage TAB
Use storage of different kind – Tapes, Tapes, Tapes. Yes, but virtual! As you might already heard, you can use software to simulate tapes. One of those is StarWind VTL.
We have more articles about StarWind VTL:
- Protect your Backups with Wasabi Immutable Storage Buckets and StarWind VTL
- Free StarWind VTL, VSAN Storage and more news
- Veeam 3-2-1 Backup Rule Now With Starwind VTL
- StarWind Virtual Tape Library (VTL) – Another layer of protection against Ransomware
Final Words
Every architecture is different. You have also different underlying hardware which offers different possibilities for ransomware protection and architecture. Immutability everywhere is a must. Coupled with strict access to your Veeam backup server you should eliminate a 90% of cases where your backups got into the hands of hackers. And if you have backups, you can restore…
Detailed articles about v12 new features:
- Veeam Backup and Replication 12 (Beta2) Installation
- Veeam Backup and Replication 12 (BETA) – adding Hardened Linux Repository
- Veeam Backup and Replication v12 – news from Barcelona 2022
- Veeam v12 direct backup to Wasabi – New UI
- Veeam Immutable Backups – Your protection against Ransomware
More about Veeam on ESX Virtualization Blog:
- What is Veeam VHR and how to quickly install and create hardened repository?(NEW)
- Veeam Backup for Microsoft 365 v7 Released
- Veeam Bare Metal Recovery Without using USB Stick (TIP)
- Veeam v12 direct backup to Wasabi – New UI
- Veeam VMCE – Why become Veeam Certified Engineer?
- Veeam Backup and Replication v12 – news from Barcelona 2022
- Veeam Backup for AWS – FREE backup of 10 instances
- Veeam Backup for Microsoft 365 v6a – What’s New?
- Veeam Backup for Google Cloud Platform – FREE 10 instances backup
- Veeam Immutable Backups – Your protection against Ransomware
- Veeam Backup and Replication 12 (Beta2) Installation
- Veeam Backup and Replication 12 (BETA) – adding Hardened Linux Repository
- Quickly setup a Veeam immutable repository via this GitHub Script
More posts from ESX Virtualization:
- VMware vSAN 8 Update 2 with many enhancements announced during VMware Explore (NEW)
- VMware vSphere 8 Update 2 New Upgrade Process for vCenter Server details (NEW)
- VMware vCenter Server 8.0 U1b resolves further upgrade issues and adds bunch of security patches
- VMware vCenter Server Appliance 8.0U1a Released
- Homelab v 8.0
- vSphere 8.0 Page
- Veeam Bare Metal Recovery Without using USB Stick (TIP)
- ESXi 7.x to 8.x upgrade scenarios
- A really FREE VPN that doesn’t suck
- Patch your ESXi 7.x again
- VMware vCenter Server 7.03 U3g – Download and patch
- Upgrade VMware ESXi to 7.0 U3 via command line
- VMware vCenter Server 7.0 U3e released – another maintenance release fixing vSphere with Tanzu
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)