Enterprise Administrators to keep their systems up to date are usually in situation when they have to deal with tons of patches. Depending on many factors like for example how many different OS and types of OS they run in their (virtualized) environments. Patching of VMs or physical servers is important, however patching of routers isn't less important either. Even very small environments, which sometimes do their business based on consumer hardware shall consider patching as critical and as a part of the global security strategy of the enterprise.
Recent shellshock bug hit mostly Linux systems, sure, but there are other exploits which are affecting daily – our routers. For example patches Linksys routers using SMART Wi-fi firmware were recently released. Those routers are fairly popular. I'm using the Linksys EA6900 model in my lab actually, and the patching is pretty simple, especially when you enable the checkbox for automatic updates. IMHO everyone should.
Router is usually the entry point where the attacker can put his nose to obtain password information, redirect traffic or read configuration informations about the LAN behind.
Let's stay with Linksys (now owned Netgear). Apparently the vulnerabilities has been known for at least 6 months and exploits available through some websites. But the patches released has been released only recently – the Oct. 23 in E4200v2, EA4500, EA6200, EA6300, EA6400, EA6500, EA6700, and EA6900 models.
This sucks. I mean, we always point at Microsoft that their patching is slow and there is many vulnerabilities that stays long days un-patched, but Microsoft (even if it takes some time) almost always finishes and patches their products at the end. We cannot say the same when we look at the network devices ecosystem, which is very different and complex.
We can see the problem with vulnerabilities slowly slipping from OS servers to web applications, and then to client side applications and network devices. However the patching cycles of network devices are way behind Server OS…
VMware did a good job and reacted very fast to the shellshock vulnerability. Plus in addition, they also released patches for older products which were affected. Like ESX 4.0 hypervisor using the Linux bash console. It usually takes much longer to release patches for vendors of network devices. And that's where the main danger lays now.
Back to the lab, finish patching and enabling that check box… -:)
The Linksys Model is actually a dual-band Wi-fi rouer which I bought few months back to replace my old WRT-54G. It's an easy to setup router, with some assistants.
Some specs:
- Up to N600 Mbps (2.4 GHz) + AC1300 Mbps (5.0 GHz) speeds with Simultaneous Dual Band
- 3 adjustable external antennas provide maximum range
- Includes Linksys Smart Wi-Fi providing easy CD free set-up, remote network management, parental control and app enabled networking
- 1 USB 3.0 and 1 USB 2.0 port to print, share and store content
- Beam forming technology follows your Tablet, Smartphone or Notebook to ensure a great connection as you move around your home
- 4 gigabit ports to connect wired devices
- DLNA certified for home media management
- Dual Core 800Mhz CPU for lightning fast processing

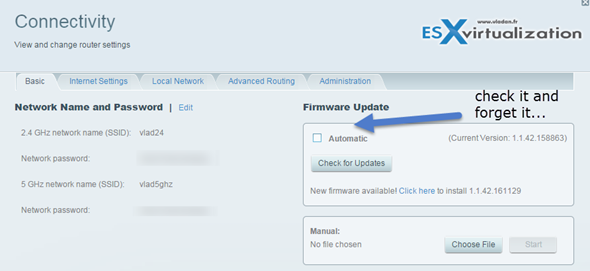
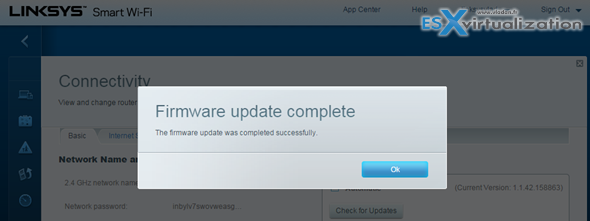
But how do you define when it should perform the update? ^^
Will it perform it randomly , maybe interrupting people in their work
Every company does have different strategy on that. It depends on many factors.