This is a usual situation. You connect to vCenter with self-signed certificate installed and you get this warning on your web browser, that the security certificate presented by this website was not issued by a trusted certificate authority. It's normal as the certificate isn't really trusted by nobody, but you. And it's you who gets this message. It's possible to Stop the Self-Signed Cert warning when connecting to vCenter quite easily (if you know how to do that). That's why this post.
This walk through is valid for Internet explorer. For Firefox it's a bit easier as you just have to follow the link called I Understand the risk and add a Security Exception. But IE users might be interested.
Let's get started. Basically when you first connect to vCenter server you'll see your web browser complaining about problem with this website's security certificate. It's a web page like this. Click the Continue to this website link (not recommended).
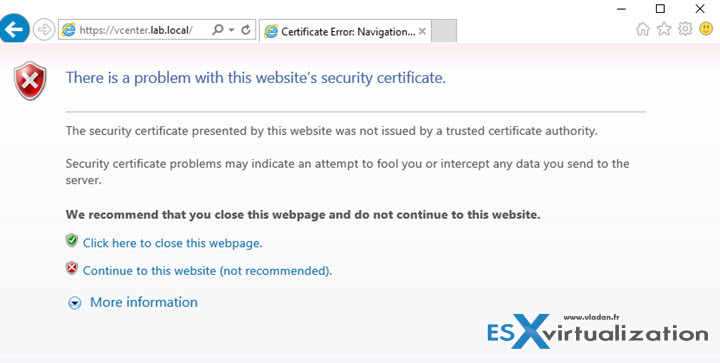
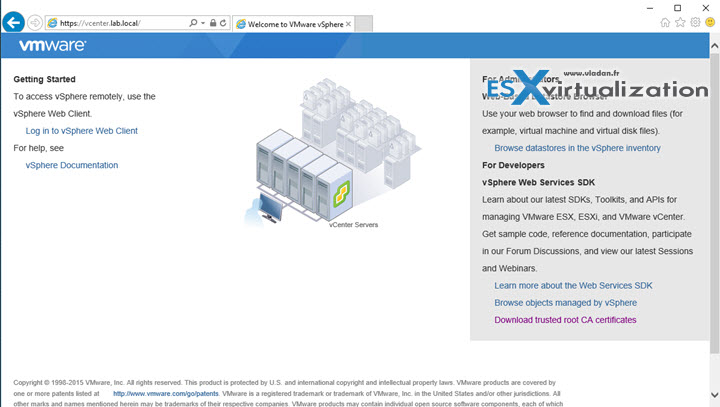
When you do this you get this view where you can click on a link Download trusted root CA certificates.
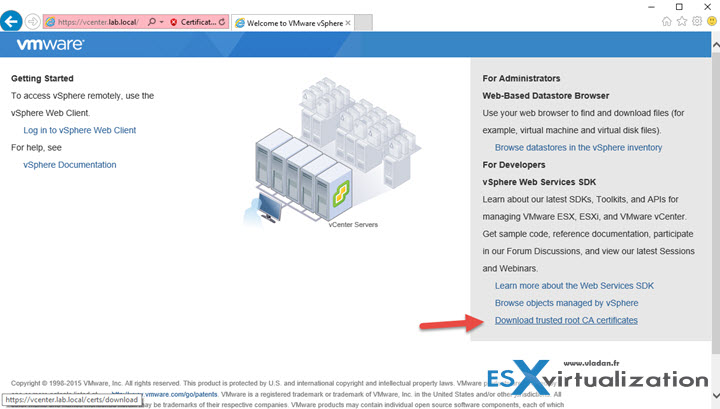
Click the link and go to your download folder where you'll find a file called download without an extension. Click save. You'll find the file in the Download folder, and it's name is Download too….
Next step is quite unattended. You'll have to change the extension and rename the file to download.zip in order to be able to extract the files (yes there are more than 1 file inside this file) from it…
So far so good. Now we need to extract the files out of the compressed file. Do a right click and select Extract All. You'll see that there are 2 files inside of the newly created folder called certs….
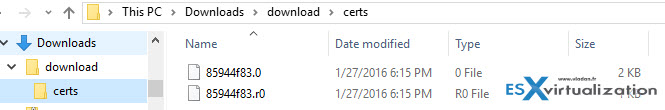
If you look closer, one of the files is with extension .0 and the other one with .r0
What we need is the .0
We'll rename the file to .cer
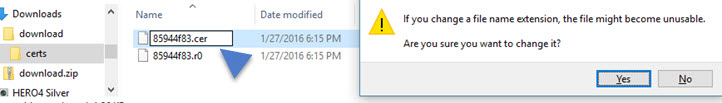
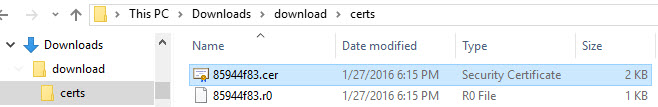
That's it. Now it gets an icon which is recognized by your (Windows) machine…
Now you'll need a cert manager console. Let's open cmd with admin priviledges. (I assume that you know how to do that, depending on which system you're working, if it's joined to a domain and if the user has local admin rights on that system.
certmgr.msc is the command
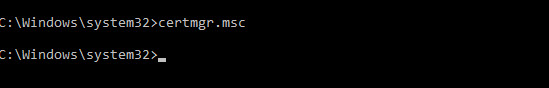
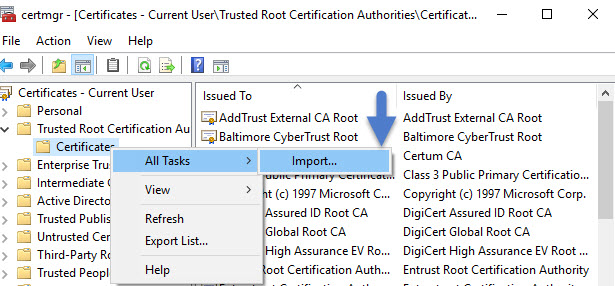
And it will open this console.. Do a right click on the sub-folder Certificates in the Trusted Root Certification Authorities > Import
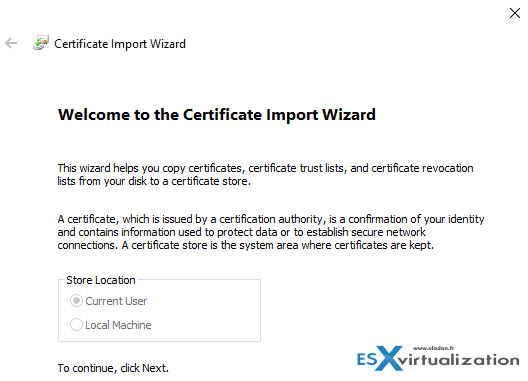
You'll see an assistant like this..
.
Go and browse for the certificate…
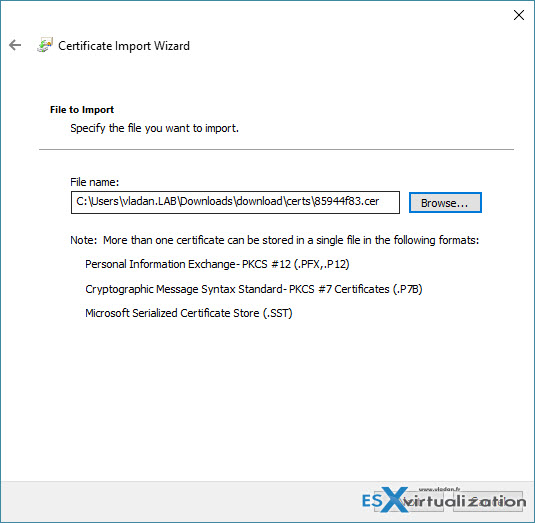
The Trusted Root certification authorities certificate store is pre selected. Click the next button to import the certificate.
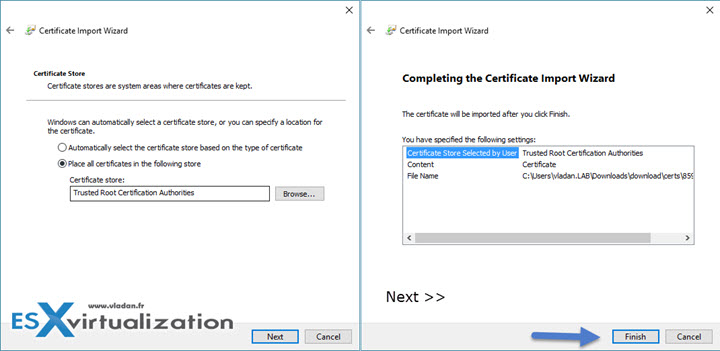
And the final confirmation looks like this…
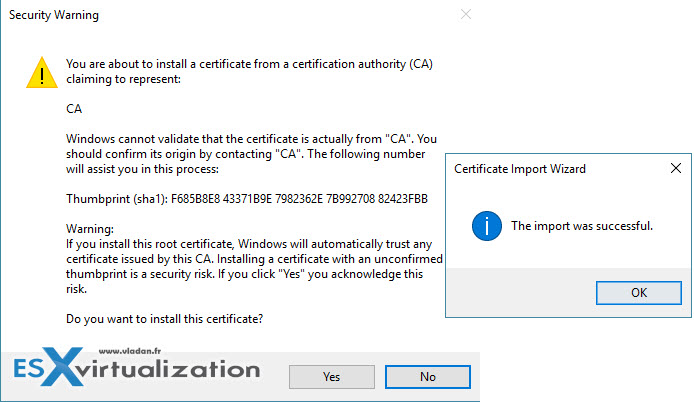
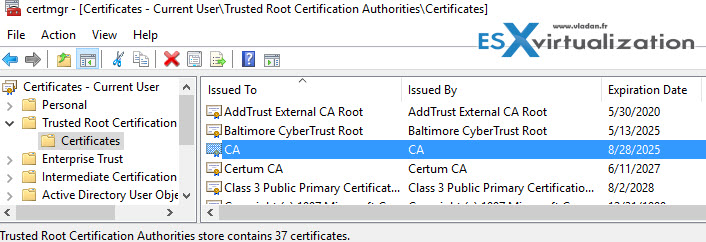
You can verify within the console that the certificate (called CA) is there…
And now when you close and start again your browser, you don't see a warning… -:)
As you could see, the procedure is quite simple to follow. I hope you have enjoyed it…

I guess this works only for vCenter Server Appliance, not for the Windows vCenter Server. For the Windows vCenter Server, you won’t get the “Download Truster Root CA Certificate” link. Is there any other workaround for the Window vCenter Server?
No, I just reproduced it in my lab where I run Windows based vCenter server…
This is specific to version 6.x+ correct? I don’t see a download link for the certificates with 5.5 Update 3
Yes. My environment is 6.x and I haven’t tested on 5.5 u3. If you’re saying that the link isn’t there, then it’s true…
My environment is 5.1.
I get certificate from vCenter Server (Windows) at C:\ProgramData\VMware\SSL\ca_certificates.crt
Hi Vlandan,
I have 5.5 and 6.x, only in the 6.x we have the option “Download Truster Root CA Certificate” link.
For 5.x we can find the same .0 file in C:\ProgramData\VMware\SSL, after renamed to .cer we can import also and works.
Luciano Patrao
Thanks for the comment Luciano….
Cheers,
Vladan
Thank you very much Vladan!
Great article! One change I noticed recently with VCSA 6.5.0a is that the download.zip now extracts to subdirectories, here’s my example filename, imported into Windows 10 just fine:
download/certs/win/926c2d7b.0.crt
Great article! I was going to use cert manager but this was much easier… thanks 🙂
Hello, Vladan. This will be my first time leaving a reply on your web site albeit being your regular reader. I appreciate your kind and nice guiding for many VMware world people.
I followed every details from your guide for this topic in my own lab environment of 6.5 VCSA.
However, it showed the usual warning message with all the browsers.
I am not sure it might have changed something in 6.5 VCSA.
Anyone having same issue?
Hi Hahn, thanks for reading my blog. It’s possible as vCSA 6.5 has regular updates and upgrades since this original article. I haven’t tested with the latest upgrade though. Usually, when you put a cert into the root authority cert store, the pop-up should disappear. But certs are pain -:).
Hello, Vladan. Surprisingly fast replay. :->
It was my bad. I kept trying to access the vcenter with the IP address, not the FQDN!!
It was fine, working as expected.
I changed the old CA signed certificate with new one in the View environment for my client yesterday.
Then, I had the same failure with accessing the IP address!!
“It’s the FQDN, stupid!!” will be my jingle for the time being.