If you're one of our readers who has also a blog, then you might be interested in following tip allowing you to be safer. It happened to my server few months back and the folks at Hostcolor did alert me about my high CPU utilization and they did add a second layer of security for me. It's rather an elegant solution which does require to change the content of your .htaccess file, but allows to secure your WordPress blog. How-to Protect Your Blog from Brute Force Attacks is today's post.
There is several ways on How-to Protect Your Blog from Brute Force Attacks. One of the elegant ways is to add a second layer of security for accessing the wp-login.php page itself. This second layer of protection prevent accessing the wp-login.php page so the attacker can't actually brute force the wp-login page containing the login form…
To launch a brute force attack on a site that logs into a user account, you just need to send the login form POST requests with the guessed username and password. In case of WordPress, the POST request with the guessed username and password is made to wp-login.php file again and again.
And here is how the second layer of protection looks like. When you type the WordPress login url https://www.yourdomain.com/wp-admin you'll find a browser pop-up window like the one below….. Note that you can easily tell your browser to remember those credentials… so the next time it won't pop-out…
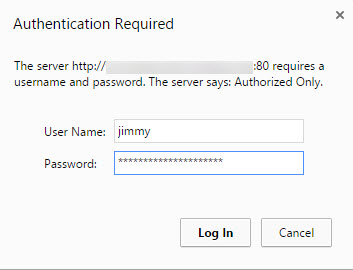
And then only you'll access the traditional WP-login.php page….
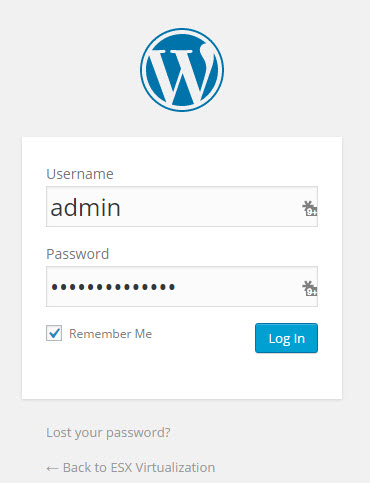
Pretty elegant solution IMHO…
Now, how do I do that? If you're using shared hosting and cpanel, then you might follow one of the procedures you can find for example here. Because you might not have an access via FTP to your .htaccess file.
But if you have an access to your .htaccess file it's enough to change its content and create another file where you store the login/password credentials.
How-to Protect Your Blog from Brute Force Attacks:
Go and generate strong password. You can use any of the online services for that, one of them is at http://passwords-generator.org/
Once you've uploaded the .htpasswd file, you need to tell .htaccess where it's at. Assuming you've put .htpasswd in your user's home directory and your htpasswd username is mysecretuser, then you put this in your .htaccess:
# Stop Apache from serving .ht* files
<Files ~ “^\.ht”>
Order allow,deny
Deny from all
</Files># Protect wp-login
<Files wp-login.php>
AuthUserFile ~/.htpasswd
AuthName “Private access”
AuthType Basic
require user mysecretuser
</Files>
The actual location of AuthUserFile depends on your server, and the ‘require user' will change based on what username you pick.
There is also an option to protect the access to the wp-admin by IP address, but you can use this only in case your ISP gave you a fixed IP.
Source: WordPress support
Update: A fellow blogger Bill Hess at PixelPrivacy has a good post about some good practices for managing (and not reusing) passwords. It's called The Real Life Risks Of Re-Using The Same Passwords – Check it out!
