Veeam Backup and Replication is a powerful solution for data protection and disaster recovery. It allows you to backup, replicate, and restore your virtual, physical, and cloud workloads with ease and efficiency. However, like any other software, it also requires proper security measures to prevent unauthorized access, data loss, or corruption.
In this blog post, I will share some tips and best practices on how to make Veeam Backup and Replication 12.1 more secure. Check also the Veeam Backup and Replication User Guide.
Upgrade to the Latest Version
The first and most important step is to upgrade to the latest version of Veeam Backup and Replication. Version 12.1 contains numerous enhancements and fixes that improve the security and performance of the product. To perform the upgrade, you need to be running version 10a or later on the supported operating system.
Use Strong Passwords and Encryption
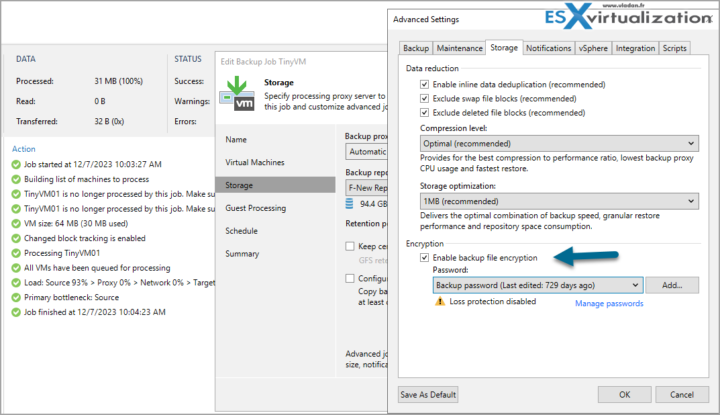
Another essential step is to use strong passwords and encryption for your Veeam Backup and Replication components and data. Veeam Backup and Replication supports various encryption standards and algorithms to protect your data at rest and in transit. You can encrypt your backup jobs, backup copy jobs, VeeamZIP jobs, and tape jobs with a user-defined password. You can also encrypt your backup repositories, backup servers, and enterprise manager servers with a storage key. For more information on how to use encryption, see the [Data Encryption] section of the user guide.
In addition to encryption, you should also use strong passwords for your Veeam Backup and Replication accounts, such as the Veeam service account, the Veeam backup administrator account, the Veeam enterprise manager account, and the Veeam guest processing account. You should also change the default passwords for the Veeam backup console, the Veeam backup enterprise manager web UI, and the Veeam backup RESTful API.
Configure Firewall Rules and Ports
To prevent unauthorized network access, you should also configure firewall rules and ports for your Veeam Backup and Replication components. Veeam Backup and Replication uses various ports for communication between the backup server, the backup proxy, the backup repository, the guest OS, and other components. You should open only the required ports and close the unused ones. You should also use secure protocols, such as HTTPS and SSH, for data transfer. For more information on how to configure firewall rules and ports, see the section of the user guide.
Apply Security Patches and Updates
Another important step is to apply security patches and updates for your Veeam Backup and Replication components and the underlying operating system. Security patches and updates fix known vulnerabilities and bugs that could compromise the security and stability of the product. You should always keep your Veeam Backup and Replication components and the operating system up to date with the latest patches and updates. You can use the Veeam Backup and Replication console or the Veeam Backup Enterprise Manager web UI to check for updates and install them. For more information on how to apply updates, see the section of the user guide.
Make sure your Windows server is fully patched and holds only the essential roles (not All-in-one as seen many times within SMB environments).
Use Multi-Factor Authentication and Kerberos Authentication
Another way to enhance the security of your Veeam Backup and Replication components is to use multi-factor authentication and Kerberos authentication. Multi-factor authentication adds an extra layer of security by requiring a second factor, such as a code or a token, to verify your identity. You can use multi-factor authentication for the Veeam Backup Enterprise Manager web UI and the Veeam Backup RESTful API. For more information on how to use multi-factor authentication, see the [Multi-Factor Authentication] section of the user guide.
Kerberos authentication is a network authentication protocol that uses tickets to authenticate users and services. You can use Kerberos authentication for the Veeam service account, the Veeam backup administrator account, the Veeam enterprise manager account, and the Veeam guest processing account. You can also use group managed service accounts (gMSAs) to simplify the management of service accounts. For more information on how to use Kerberos authentication and gMSAs, see the [Kerberos Authentication] section of the user guide.
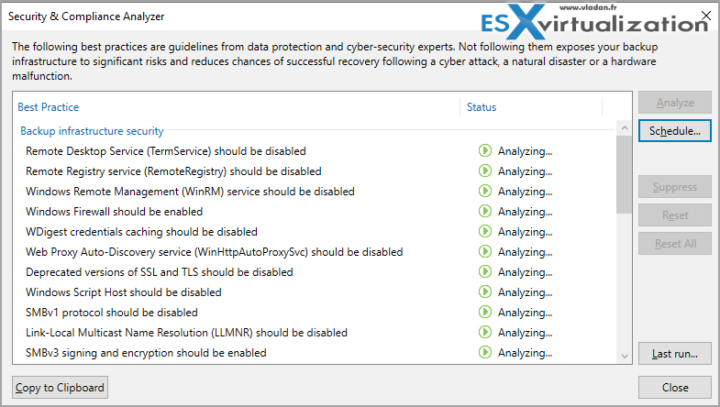
Use the New Built-in Security And Compliance Analyzer
Conclusion
We just scratched the surface. I'll do a follow-up article on this. Stay tuned. These are just some of the tips and best practices on how to make Veeam Backup and Replication 12.1 more secure. By following these steps, you can ensure that your data is protected from unauthorized access, data loss, or corruption. You can also improve the performance and reliability of your Veeam Backup and Replication components.
Detailed articles about v12 new features:
- Veeam 12.1 Four-Eyes Authorization – prevent accidental deletion of backups and other operations with two different persons only
- What is Inline Entropy Analysis in Veeam Backup and Replication 12.1
- Veeam 12.1 Biggest Features
- Veeam 12.1 Download Available – Start Your Download Engines (with Install video)
- Your repository is full – How to move your backups to another repository with Veeam backup?
- Practical Tips to protect your Veeam Backup Repositories
- Veeam Backup and Replication v12 – Get the latest ISO
- What is Veeam VHR and how to quickly install and create hardened repository?
- Don’t miss this Veeam v12 Download with latest cumulative patches
- Practical Tips to protect your Veeam Backup Repositories
- Veeam Backup and Replication 12 (Beta2) Installation
- Veeam Backup and Replication 12 (BETA) – adding Hardened Linux Repository
- Veeam Immutable Backups – Your protection against Ransomware
More posts from ESX Virtualization:
- VMware vSphere 8.0 U2 Released – ESXi 8.0 U2 and VCSA 8.0 U2 How to update (NEW)
- What’s the purpose of those 17 virtual hard disks within VMware vCenter Server Appliance (VCSA) 8.0?
- VMware vSphere 8 Update 2 New Upgrade Process for vCenter Server details
- VMware vSAN 8 Update 2 with many enhancements announced during VMware Explore
- What’s New in VMware Virtual Hardware v21 and vSphere 8 Update 2?
- Homelab v 8.0
- vSphere 8.0 Page
- Veeam Bare Metal Recovery Without using USB Stick (TIP)
- ESXi 7.x to 8.x upgrade scenarios
- A really FREE VPN that doesn’t suck
- Patch your ESXi 7.x again
- VMware vCenter Server 7.03 U3g – Download and patch
- Upgrade VMware ESXi to 7.0 U3 via command line
- VMware vCenter Server 7.0 U3e released – another maintenance release fixing vSphere with Tanzu
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)