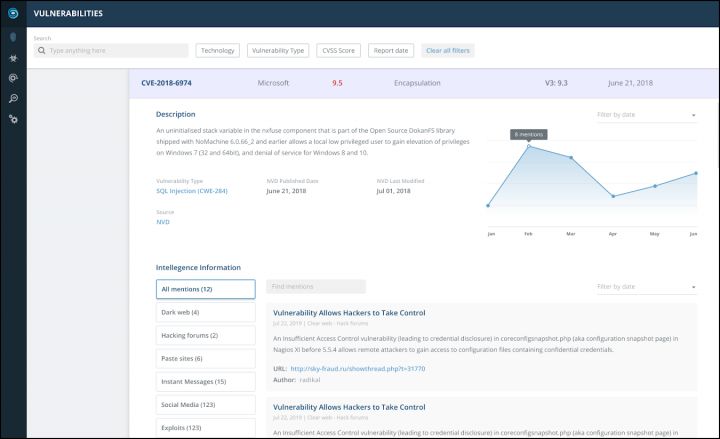
With the growth of cyber threats all over the globe, many enterprises, service providers and IT admins are looking for a solution to be alerted, be protected or better, actively suppress potential threats. Today we’ll talk about cybersecurity and services allowing to detect and fight cyberthreats, phishing and fraud or impersonating.
Many people imagine that malware, viruses and other cyberthreats and cyberattacks are just the one main side of the cyberthreats and the others are less important. Well, impersonating, scams and organized crime that uses mirrored sites of an original (legal) website, are also a kind of cybersecurity risk.
How does a phishing attack work?
Basically, hacker’s setup up phishing domains, e.g. my-paypal.co and then try to lure customers into giving up their bank login details. The real legit website is a victim. They then sell this information to shady operators on the Dark Web – this can also be known as a “data leak”.
What is Domain Name Monitoring?
One way to steal data is to use a technique called phishing, where cybercriminals use fake (or spoofed) domain names in email phishing attacks to get a hold of your login credentials. There are so many domains being registered and activated each day over thousands of different TLD’s that its almost impossible to track if your brand has been implicated in.
In this example, one company called IntSights can help. They get alerts about new domains with brand mentions and can automatically take actions that shut the malicious domain down for you.
This is just an example with banking details. There are many more indeed and I can even add my own example. Their dark web monitoring services go as far as tracking email campaigns with phishing material in it.
IntSights Threat Intelligence Platform (TIP)
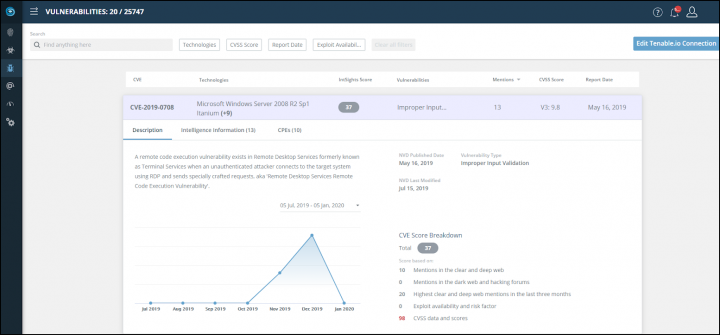
It is a cloud-based platform so no local installation is necessary at your end. The platform is able to centralize and organize the treat sources into one easy dashboard. IntSights has an in-house automated remediation service that helps customers to take down malicious content published on the web.
They’re able to track not only fake websites, but also mobile applications, fraudulent social media pages or pages that contain sensitive data with a possible attack intention.
Identify compromised credentials – possibility to instantly identify and lock down credential leaks by using a leaked credentials database. The system monitors the dark web and when found, with a built-in custom policies, triggers custom reset notification.
The User interface showing an overview different vulnerabilities and their sources.
Other tracking features:
- Files or malicious items which were used to attack a customer, like leaked login credentials, credit card information, or other private database information.
- Domain name monitoring – this can be an example of a registered malicious website that uses very similar domain name (ex. cocacola.com vs colacola.com).
- Domains that were involved in phishing campaigns against IntSight’s customers or their customers.
- Track code and file sharing sites where they monitor possible exploits, sensitive data or leaked credentials. When matched they initiate a removal request for you.
- IOC Enrichment helps inform you about possible cyber-attacks, network breaches, and malware infections
IntSights works hand in hand with many sources such as social media, app stores, domain registrars, paste sites (Pastebin, Ghostbin), code sites (GitHub), web hosting providers and more.
 How do they achieve this?
How do they achieve this?
It is an automatic process with manual interventions here and there. For example, the contact of the website owner or domain registrar to have the webpage shut down or suspend is automatic after the detection.
The system then provides them the details of the attack and suspicious content.
For social media fake pages, they first identify the fake which must be really identical to the original (same logo, industry, etc).
The remediation team from IntSights monitors the automatic process and makes manual intervention when needed once there is a reply from a service provider, a web hosting company or so.
Final Words
From my own personal experience, I can tell that I have had a similar experience with my ESX Virtualization blog 5-8 years ago. Someone made a mirror copy with a different domain extension and tried “just” to make some money by placing affiliate links into the text of all my posts, to sell IT products etc. Each time I published a new article the cyber-criminal had his/her site updated (probably automatically via script).
My SEO went down, and my web traffic as well. Google found duplicated content on the internet and hit me with bad SERP results. I had a hard time letting them take that site down and explain that it’s not me who created duplicated content. As you can see, even such a small entity like mine can find benefit from the new services that exist around today and you might not be aware of.
IntSights was founded in 2015 by former members of an elite intelligence unit in the Israel Defense Forces. Today, IntSights is trusted by many of the world’s largest companies to detect, analyze, and neutralize cyber threats across the clear, deep, and dark web. BTW, recently they helped Europol to shut down the largest dark web marketplace in Europe.
More posts from ESX Virtualization:
- vSphere 7.0 U2 Released
- vSphere 7.0 Download Now Available
- vSphere 7.0 Page [All details about vSphere and related products here]
- VMware vSphere 7.0 Announced – vCenter Server Details
- VMware vSphere 7.0 DRS Improvements – What's New
- How to Patch vCenter Server Appliance (VCSA) – [Guide]
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)