Microsoft has released a final version of free utility called Enhanced Mitigation Experience Toolkit 4.0 (EMET). A mitigation technology is protection against attackers, where a malicious code cannot be executed to infect Windows systems. EMET can act at different levels. At system level, at process level, or at the application level.
There were always some kind of protection present in Windows systems (since Windows XP), but for example the DEP in Win XP (Data Execution Prevention) could not be configured for individual applications. EMET can configure the application protection individually.
This product can be downloaded from Microsoft, from the download section. This small MSI package (8.3 Megs) installs on your system, sits there along with your antivirus/antispyware solution, and allows to detect zero day threats. It's in case your antivirus solution is not efficient and the virus is already on your system, then EMET can protect against a malicious code execution. An old software, which cannot get rewritten, and needs to be protected, can be protected by EMET.
EMET comes with built-in support for enterprise deployment, so it can be deployed via Group Policy or System Center Configuration Manager. EMET needs DotNET 4.0 to function. In case you're running Windows 8 and Internet Explorer 10, you'll need to install KB2790907 from Microsoft.
EMET is compatible from Windows 2003 SP1 all the way up to Windows Server 2012. As a client systems, EMET supports Windows XP SP3 and higher (Including W8). The very useful User Guide in PDF is part of the download.
Which Applications are protected by default?
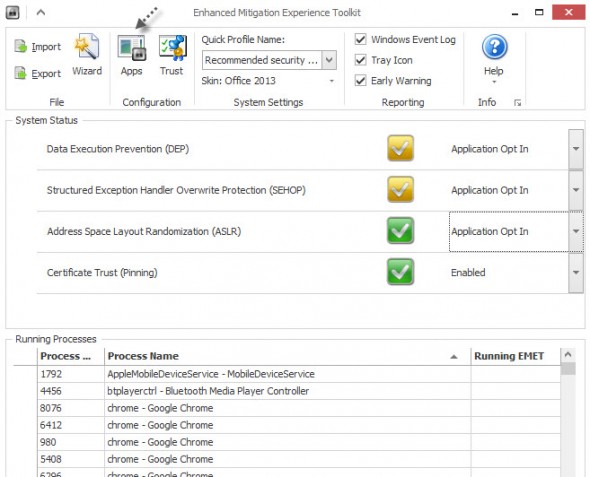
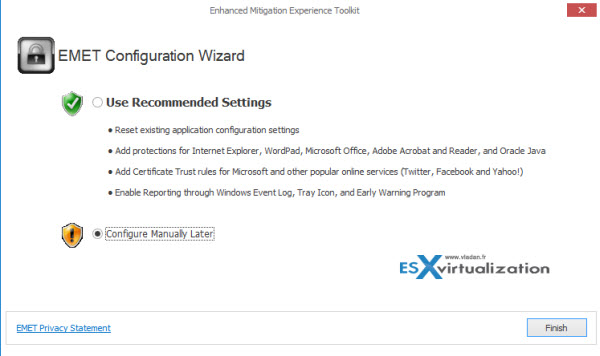
The products starts with an assistant. If you choose to use defaults, you'll find out which applications on your system are protected by default by clicking the Apps button.
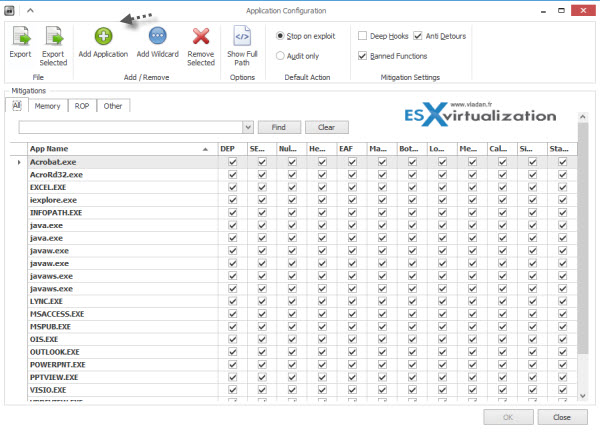
The detailed list of applications will appear on separate window. You can change the values by unchecking the check boxes.
If you want to start with blank list, you can choose “configure manually later” and select/add individually applications that you want to protect, one by one.
Enhanced Mitigation Experience Toolkit 4.0 What's it good for? Which protection EMET provide?
EMET version 4.0 can already protect against many exploits which are currently in use and contain some features and changes that stops or slow down the attacker:
- Certificate Trust: considering the raise of PKI-related attacks, we decided to implement a configurable SSL Certificate Pinning to try to detect Man in the Middle attacks that leverage SSL/TLS certificates. The Certificate Trust feature in EMET is rule-based and allows to pin a specific SSL/TLS certificate to a trusted Root Certificate Authority.
- ROP mitigations and hardening: in the last Technical Preview release of EMET, we introduced some mitigations to try to stop ROP-based attacks by implementing some of the winner ideas of the BlueHat Prize contest. With this new EMET release we hardened the ROP and other mitigations to detect and stop novel attack techniques.
- Early Warning Program: this feature will allow EMET to send contextual data back to Microsoft, through the standard Windows Error Reporting channel, every time that an exploit has been detected and stopped. We are adding this feature to help us respond to new 0day exploits as soon as possible.
- Audit mode: if an exploit is detected, EMET will not terminate the attacked process but it will just report the attack and let the process continue. This mode is only applicable to certain mitigations, for example the anti-ROP ones, that detect the attack when the process is not already in a crashed state. This feature is useful for enterprise customers for testing purposes and to spot false-positives and app-compat problems without compromising the user experience.
Thoughts:
I would see some usage scenarios, with older systems, which must use for example older versions of Internet Explorer, due a compatibility with custom written applications. It looks like a powerful solution which allows protection of individual applications, which admins can't migrate users elsewhere, for various reasons.
I think it's no brainer. A very small amount of memory is consumed by EMET, and it's free… EMET can be downloaded from Microsoft. It's a Free Download. Enjoy… -:) If you want more details on DEP … here is the link on Microsoft's website.
Fell free to subscribe to our RSS Feed.

I don’t want to get off on a rant here, but I don’t know why everyone is giving such high acclaims and accolades about this programe? It’s horrible! Every since our central office puked it out onto our subnets there has been nothing but trouble. Login freezes, slower operating, frequent IE crashes, frequent CAD program crashes, one of my guy’s dual monitors will not work anymore. At this point can I say for sure beyond a reasonable doubt that it’s EMET causing all of this? No, but but it seems almost TOO awfully circumstantial that it was the only thing new installed at the end of one week and all of these issues began the beginning of the next week. Maybe I could be just jumping to conclusions,……but I doubt it. I mean for crying out loud .NET 4 is a prerequisite for it. That should say enough right there. Exactly how many patches has there been for .NET now? Something with that many revisions is a dead give away of shoddy ground work to begin with. Do we really need yet another peice of crap background service running anyways?