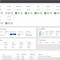
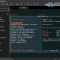
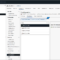
This is exciting. After successfully installed my Xen Orchestra in the lab (nested with VMware Workstation. BTW, you can also use VMware Workstation Player which is FREE), when testing XCP-NG (after some initial problems, now resolved) by reading the forums, I discovered that there is actually a host client! It’s name is XO Lite and […]
Another VMware Alternative – Verge.IO
Let’s continue our exploration about some viable VMware alternatives when it comes to infrastructure virtualization. As you could read in our introductory article – Best VMware Alternatives – ESXi FREE is DEAD – we will do some digging into some VMware alternatives which might be useful for users willing to step out of their comfort […]
XCP-NG Virtualization Platform with management by Xen Orchestra
One of the first virtualization platforms out there which is getting its popularity exploding is XCP-NG virtualization platform by vates.tech from France. It all started in 2011-2012 so it’s not a new platform. UPDATE: Make sure to read the update as I have finally managed to find the time and redeploy the Xen Orchestra. It’s […]
Best VMware Alternatives – ESXi FREE is DEAD
In this series of posts that we’ll be creating over the next couple of weeks, we’ll try to list the best VMware Alternatives for virtualization of servers. Many alternative vendors does not do VDI so we won’t include those in our series. VMware does VDI pretty well and their Horizon/One products got pretty good over […]
Microsoft Windows Server 2025 – What’s New recap
In a datacenter and cloud world that now only has eyes for Linux, few weeks back, Microsoft has announced that Windows Server 2025 will be the next edition of Windows Server. Windows Server 2025 will therefore be the next version of Microsoft’s operating system for servers and data centers. This version, which succeeds Windows Server […]
Windows 11 version 24H2 is next – This Fall
Microsoft has confirmed the next major update of Windows 11 and its name is Windows 11 version 24H2. This was somehow expected as Windows 12 development, that some of you were wishing to come, has not started yet. Windows 11 version 24H2 will bring many new features for end users (energy saver, scrollable quick settings, […]
Install StarWind VSAN via PowerCLI in VMware vSphere Environment
There is a nice technical paper at StarWind detailing the Install StarWind VSAN via PowerCLI in VMware vSphere Environment. When done, you’ll find your environment fully configured deployed with StarWind VSAN VMs (Controller virtual machines = CVM). This can be particularly useful when you have several branch offices to deploy using the same pattern. When […]
vSphere Configuration Profiles – How VMware vCenter Server 8.0 U2 Can Simplify and Optimize vSphere Infrastructure Administration
One of the key components of vSphere is VMware vCenter Server that allows you to manage multiple hosts connected, create clusters, datacenters and other objects, and also manage HA and vMotion operations. vCenter Server provide those various services and features that enable efficient and automated resource management and high availability for virtual machines, such as […]
Hornetsecurity Cyber Security Report 2024: What to Expect in the Microsoft 365 Threat Landscape
Hornetsecurity who is a provider of cloud-based email security solutions and data protection solutions (formerly Altaro VM Backup) has recently released its annual Cyber Security Report 2024, which analyzes the Microsoft 365 (M365) threat landscape based on real-world data collected from billion of emails processed in 2023. (3.5 billion every month). The report reveals the […]
How VMware VM Images Can Save Time for Administrators
I just wanted to quickly share a website which offers preinstalled VMware Images (also for other platforms). If you quickly want to test a VM that you don’t have a VM template available. In this post we’ll explore How VMware VM Images Can Save Time for Administrators. You can save some time by directly downloading […]
- « Previous Page
- 1
- …
- 4
- 5
- 6
- 7
- 8
- …
- 152
- Next Page »