There is a new free utility from Microsoft called Local Administrator Password Solution (LAPS) which enhances a security on domain managed workstations (servers) by managing the local admin passwords in the domain on those systems. The tool might interest a system admins which want to reinforce their domain security as it allows setting a different, random password for the common local administrator account on every computer in the domain.
The utility does not working as usual software solution, but rather as local client-side extension. LAPS uses a Group Policy client-side extension (CSE) that you install on managed computers to perform all management tasks. So the MSI shall be installed on every computer you want to manage local admin password, in your domain.
In every company there are some locally written software solutions which needs a local admin account to run properly. Systems where local admin password is compromised can be used to elevate priviledges from local/admin to a domain/admin. So good practice is to change the local admin password on those systems on regular basis, but everyone knows that this task is quite impossible in larger organization.
Local Administrator Password Solution (LAPS) – The Features:
Security:
- Randomly generate passwords that are automatically changed on managed machines.
- Effectively mitigate PtH attacks that rely on identical local account passwords.
- Enforced password protection during transport via encryption using the Kerberos version 5 protocol.
- Use access control lists (ACLs) to protect passwords in Active Directory and easily implement a detailed security model.
Manageability:
- Configure password parameters, including age, complexity, and length.
- Force password reset on a per-machine basis.
- Use a security model that is integrated with ACLs in Active Directory.
- Use any Active Directory management tool of choice; custom tools, such as Windows PowerShell, are provided.
- Protect against computer account deletion.
- Easily implement the solution with a minimal footprint.
- Periodically randomize local administrator passwords to ensure that password updates to Active Directory succeed before modifying local secrets and passwords.
- Centrally store secrets in the existing Active Directory infrastructure.
- Control access through Active Directory access control list (ACL) permissions.
- Transmit encrypted passwords from computers to Active Directory via encryption using the Kerberos version 5 protocol and the Advanced Encryption Standard (AES) cypher by default.
System requirements:
- Checks whether the password of the local Administrator account has expired.
- Generates a new password when the old password is either expired or is required to be changed prior to expiration.
- Validates the new password against the password policy.
- Reports the password to Active Directory, storing it with a confidential attribute with the computer account in Active Directory.
- Reports the next expiration time for the password to Active Directory, storing it with an attribute with the computer account in Active Directory.
- Changes the password of the Administrator account.
There are two main components within LAPS:
- First – modifies the forest’s schema to include two new fields to store the password generated on the client.
- Second – Group Policy extension that runs on the client to report the new password back to Active Directory. This requires modifying Active Directory and every client in the environment.
Installation
Install the Management UI on a domain controller….
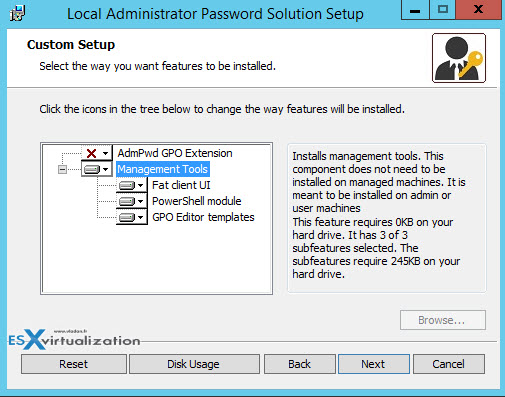
And the GPO Extension on each of the management computers in your domain… (Note that you can deploy the MSI using GPO as well…)
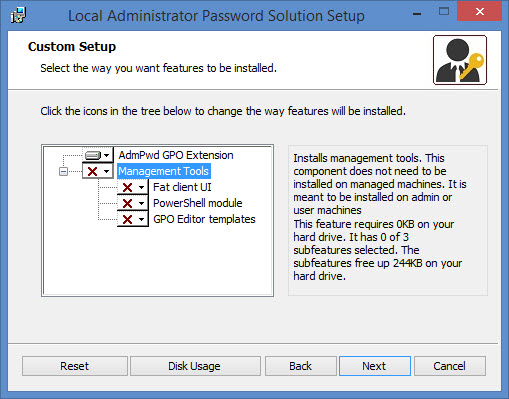
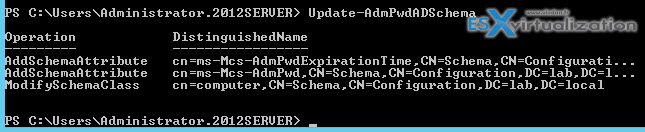
Next you'll have to run two PowerShell commands:
1. run this:
Import-module AdmPwd.ps
2. run this:
Update-AdmPwdADSchema
Next you'll need to edit the group policy in order to start using this tool:
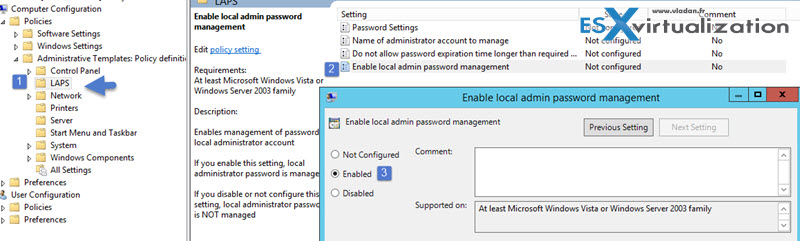
Note that you can also change the default password setting policy. By default this solution uses a password with maximum password complexity, 14 characters and changes the password every 30 days. You can change the values to suit your needs by editing a Group Policy.
You can check the new attributes in the computer's account properties (double click the computer account in your AD > Attribute editor). Make sure that you are in the Advanced View ….
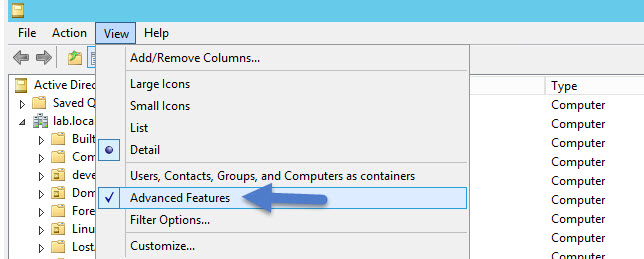
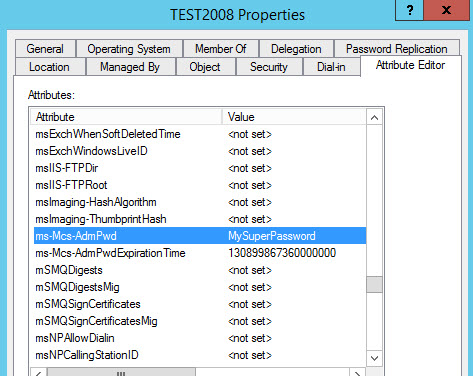
And then double click the computer account, scroll down to check the local password…
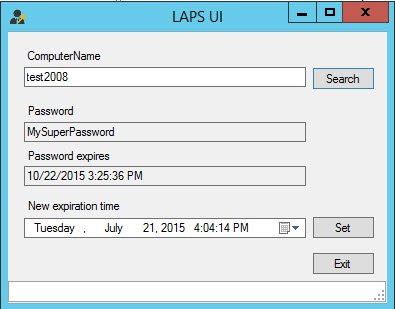
The LAPS UI allows you to set a new expiration time or force an immediate expiration. In case the password or expiration fields are blank, then it's possible that the account used does not have enough permissions to read the attribute in your AD.
Then you can execute the Admin tool on your Domain controller and set different time for expiration.
Be sure to check the steps in the Admin guide which is included with the utility. The tool is bundled as x32 and x64 versions as many of the domain admin clients are x32 systems.
Download and more information:
- Microsoft Knowledge Base Article 3062591
- Microsoft Download Center
Source: Technet

LAPS SCCM integration: https://gallery.technet.microsoft.com/LAPS-Extension-for-SCCM-e8bd35b1