Recent Shellshock bug in Linux Bash revealed the 24th of September was often compared to Heartbleed bug in terms of severity. Just to remind you, it affects all Linux/Unix systems using the original bash (which has been re-released for new distros already).
OSX users were told to deactivate the advanced Unix services, but apparently even after the release of Apple's patches there are still some areas under flaw.
The exploit is apparently very simple to use that many non patched Linux servers were used as botnets to launch DDOS attacks. The US government-backed National Vulnerability Database rated Shellshock 10/10 for severity.
Wikipedia:
Attackers exploited Shellshock within hours of the initial disclosure by creating botnets on compromised computers to perform distributed denial-of-service attacks and vulnerability scanning. Millions of attacks and probes related to the bug were recorded by security companies in the days following the disclosure.
VMware's products were also affected. Not the ESXi hypervisors as they don't use the bash but busybox. Some older version of VMware hypervisors are however affected because they are (were) using bash (ESX 4.0 and ESX 4.1).
Most Virtual appliances using bash will needs to be patched or if you're deploying new environment you can simply re-download new, updated release.
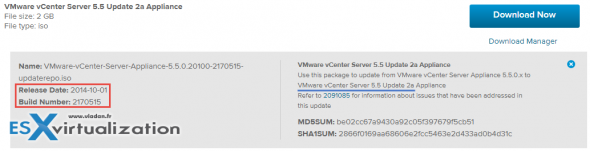
Here is an example of VCSA 5.5 U2a which is up to date (Shellshock patched) release of vCenter Server Linux appliance available from MyVMware…
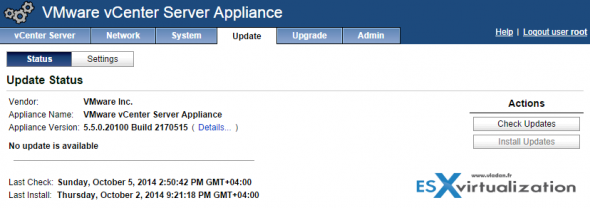
If you are running unpatched VCSA then simply go to the Update TAB (via https://IP_of_VCSA:5480 ) and hit the Check updates button and then the Install updates button. It's fast, convenient and easy.
VMware is working to release patches (even for older, unsupported products like vSphere 4.0). There is a VMware KB that is updated on regular basis and which informs about patches and products concerned by the security flaw. KB 2090740: Bash Code Injection Vulnerability via Specially Crafted Environment Variables (CVE-2014-6271 CVE-2014-7169, aka “Shellshock”).
Here are the product details as of today (but the list changes every day as VMware works on the problem and adding more links):
VMware (Virtual) Appliances
- EVO:RAIL 1.x (EVO:Rail ships with vCenter Server Appliance and vCenter Log Insight and will be re-released with updated versions of these appliances)
- Horizon DaaS Platform 6.x (See VMSA-2014-0010 for remediation details)
- Horizon Workspace 1.x, 2.x. (See VMSA-2014-0010 for remediation details)
- IT Business Management Suite 1.x (See VMSA-2014-0010 for remediation details)
- NSX for Multi-Hypervisor 4.x (See VMSA-2014-0010 for remediation details)
- NSX for vSphere 6.x (See VMSA-2014-0010 for remediation details)
- NVP 3.x (See VMSA-2014-0010 for remediation details)
- vCenter Converter Standalone 5.x (vCenter Converter Standalone is not a Virtual Appliance but includes a vulnerable version of bash)
- vCenter Hyperic Server 5.x (See VMSA-2014-0010 for remediation details)
- vCenter Infrastructure Navigator 5.x (See VMSA-2014-0010 for remediation details)
- vCenter Log Insight 1.0, 2.0 (See VMSA-2014-0010 for remediation details)
- vCenter Operations Manager 5.x (See VMSA-2014-0010 for remediation details)
- vCenter Orchestrator Appliance 4.x, 5.x (See VMSA-2014-0010 for remediation details)
- vCenter Server Appliance 5.x (See VMSA-2014-0010 for remediation details)
- vCenter Site Recovery Manager 5.x (vCenter Site Recovery Manager ships with vSphere Replication and will be re-released with an updated version of this appliance) (See VMSA-2014-0010 for remediation details)
- vCenter Support Assistant 5.x (See VMSA-2014-0010 for remediation details)
- vCloud Application Director 5.x, 6.x (aka vFabric Application Director) (See VMSA-2014-0010 for remediation details)
- vCloud Automation Center 6.x (Note: vCloud Automation Center 5.x is not a virtual appliance) (See VMSA-2014-0010 for remediation details)
- vCloud Automation Center Application Services 6.x (See VMSA-2014-0010 for remediation details)
- vCloud Director 5.x Appliance (See VMSA-2014-0010 for remediation details)
- vCloud Connector 2.x (See VMSA-2014-0010 for remediation details)
- vCloud Networking and Security 5.x (aka VMware Shield 5.x) (See VMSA-2014-0010 for remediation details)
- vCloud Usage Meter 3.x (See VMSA-2014-0010 for remediation details)
- vFabric Postgres 9.x (See VMSA-2014-0010 for remediation details)
- Viewplanner 3.x
- VMware Application Dependency Planner
- VMware Data Recovery 2.x (See VMSA-2014-0010 for remediation details)
- VMware HealthAnalyzer 5.x
- VMware Mirage Gateway 5.x (See VMSA-2014-0010 for remediation details)
- VMware Socialcast On Premise 2.x
- VMware Studio 2.x
- VMware Workbench 3.x
- vSphere App HA 1.x (See VMSA-2014-0010 for remediation details)
- vSphere Big Data Extensions 1.x, 2.x (See VMSA-2014-0010 for remediation details)
- vSphere Data Protection 5.x
- vSphere Management Assistant 5.x (See VMSA-2014-0010 for remediation details)
- vSphere Replication 5.x (See VMSA-2014-0010 for remediation details)
- vSphere Storage Appliance 5.x (See VMSA-2014-0010 for remediation details)
Check back this KB on regular basis – KB 2090740.