As the title shows, this post is about private VLANs (PVLAN). This topic shows on VCAP exams, but also on VCP based exams. So if you're studying for VCAP or VCP, this article might be your interest. VMware vSphere and Private VLANs are great topic, but not easy.
Usually you can separate traffic and secure your environment by using VLANS, but private VLANs allows further segmentation and creation of private groups inside each of the VLAN. By using private VLANs (PVLANs) you splitting the broadcast domain into multiple isolated broadcast “subdomains”.
Private VLANs needs to be configured at the physical switch level (the switch must support PVLANs) and also on the VMware vSphere distributed switch. (Ent. Plus is required). I'ts more expensive and takes a bit more work to setup. Is that why it's not widely used?
There are different types of PVLANs:
Primary:
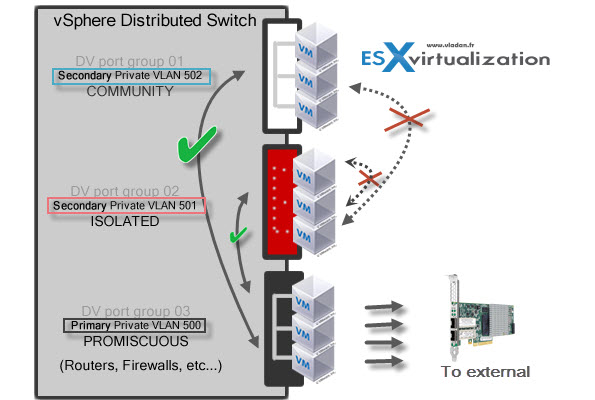
Promiscuous Primary VLAN – Imagine this VLAN as a kind of a router. All packets from the secondary VLANS go through this VLAN. Packets which also goes downstream and so this type of VLAN is used to forward packets downstream to all Secondary VLANs.
Secondary:
Isolated (Secondary) – VMs can communicate with other devices on the Promiscuous VLAN but not with other VMs on the Isolated VLAN.
Community (Secondary) – VMs can communicate with other VMs on Promiscuous and also w those on the same community VLAN.
The graphics shows it all…
So where we configure PVLANs in vSphere?
VDS is a vSphere Enterprise Plus feature as we need vSphere Distributed Switch (vDS) to configure PVLANs. Then it's quite straightforward:
The VCAP exam is based on vSphere 5.0 or 5.1, so you'll probably won't have an access to create vDS version 5.5 and have an access to the latest features, which brought the 5.5 version. So you'll have the possibility to create vDS version 4.0 … up to 5.5.
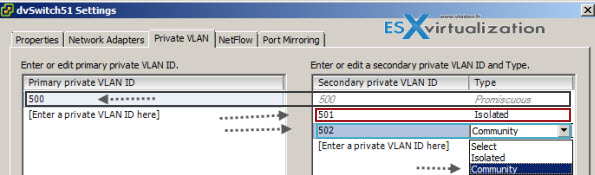
The next step is to create some PVLANs. You'll be doing it at the vDS level, so select and right click the vDS > Edit Settings > Private VLAN tab. Once there you can add some PVLANs. Notice the Secondary Promiscuous was created automatically when you created the Primary private VLAN.
So in my example above I created Primary Private VLAN 500 which automatically created secondary PVLAN 500. Then I only could create an Isolated Secondary VLAN 501 and Community VLAN 502.
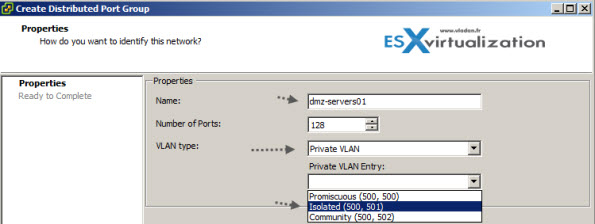
Now we have those PVLANs created and this gives us the possibility to use them for new or existing port groups. Example below I'm creating new port group with some name and after selecting the PVLAN, a new drop-down menu appears which gives the option to choose an entry between the Isolated, or Community.
Private VLANS definitions:
- Promiscuous – A promiscuous port can communicate with all interfaces, including the isolated and community ports within a PVLAN.
- Isolated – An isolated port has complete Layer 2 separation from the other ports within the same PVLAN, but not from the promiscuous ports. PVLANs block all traffic to isolated ports except traffic from promiscuous ports. Traffic from isolated port is forwarded only to promiscuous ports.
- Community– Community ports communicate among themselves and with their promiscuous ports. These interfaces are separated at Layer 2 from all other interfaces in other communities or isolated ports within their PVLAN.
On the VCAP5-DCA Blueprint it's the Objective 2.2 – Configure and Maintain VLANs, PVLANs and VLAN Settings and you are required to have VLANs and PVLANs knowledge with also:
- to be able to determine use cases for and configure VLAN trunking
- to be able to determine use cases for and configure PVLANs
- Use command line tools to troubleshoot and identify VLAN configurations
Command Line Tools
There are commands which can be run via VMA, others via vCLI or directly SSh to the ESXi via Putty:
esxcli network vswitch standard list – shows the standard vswitch settings
Etc… if you put -h for help you can get the options showed at different levels
esxcli network -h shows options for fence, firewall, ip, vswitch, nic…. etc.
Enjoy…
The article was published first at ESX Virtualization website. Feel free to subscribe via RSS or by e-mail to get the latest news to be delivered via weekly newsletter.