Veeam 12.1 Four-Eyes is a configuration where by using a new control mechanism, you'll be able to approve certain operations in Veeam Backup and Replication, but only with the help of another Veeam admin. In other words, for example, you want to delete some backups. With this feature activated, you'll need another admin who will approve this operation. It's kind of a safe guide to prevent you to accidentally deleting your backups. This also makes it more difficult for the ransomware guys which now need both accounts to delete your backups…..
How to Protect Your Data with Four-Eyes Authorization
As you know, data protection is a crucial task for any organization, especially in the era of cloud computing, where data can be stored and accessed from anywhere. However, data protection also comes with risks, such as accidental or malicious deletion, corruption, or encryption of backups. To prevent these risks and ensure compliance with regulations and policies, you need a reliable and secure backup solution that can protect your data from unauthorized access or modification.
One of the features that Veeam Backup & Replication 12.1 offers is four-eyes authorization, which is a new control mechanism that requires additional approval to certain operations in Veeam Backup & Replication given by another user with the Veeam Backup Administrator role. This feature allows you to reduce the risk of accidental actions affecting sensitive data by requiring two users to approve any operation that involves deleting backup files or snapshots from the disk or configuration database. There are also other operations, such as:
- Veeam Backup & Replication supports four-eyes authorization for the following operations:
- Deleting backup files or snapshots from the disk or configuration database
- Deleting information about unavailable backups from the configuration database
- Removing backup repositories, storage, and service providers from the backup infrastructure
- Adding, updating, and deleting users or user groups
- Enabling and disabling multi-factor authentication (MFA) for all users and user groups
- Resetting MFA for a specific user
- Enabling, updating and disabling automatic logoff for all users and user groups
How does four-eyes authorization work?
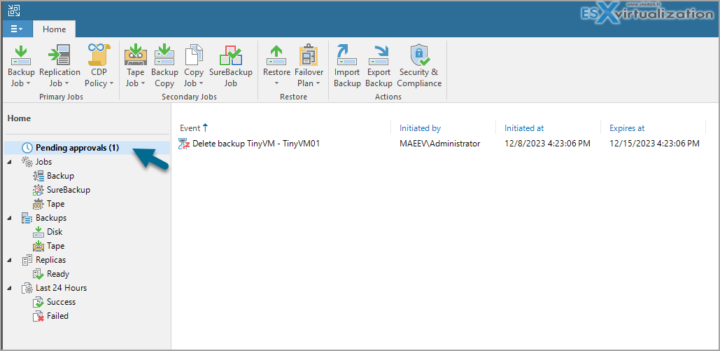
Four-eyes authorization works by displaying a request for additional approval in the Home view of Veeam Backup & Replication 12.1 under the Pending approvals node1. The request shows the operation that needs approval and the reason why it is sensitive. The requesting user can either approve or reject the request within a specified time limit. If approved, the operation proceeds as normal. If rejected, an error message is displayed.
All users with the Veeam Backup Administrator role also get email notifications if you configured global email notification settings. They can view the pending requests in their email inbox and decide whether to approve or reject them.
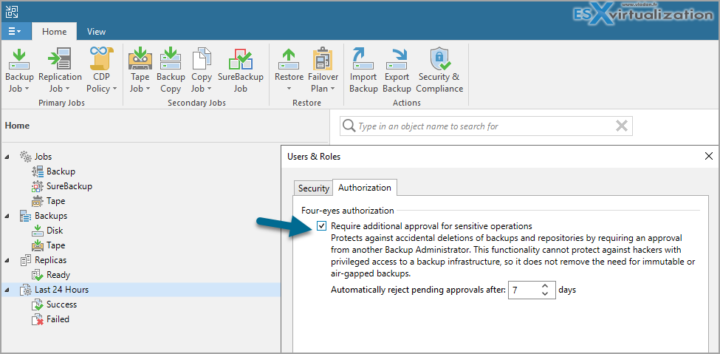
You can activate the feature when going to the Main menu > Users and Roles > Authorisation TAB
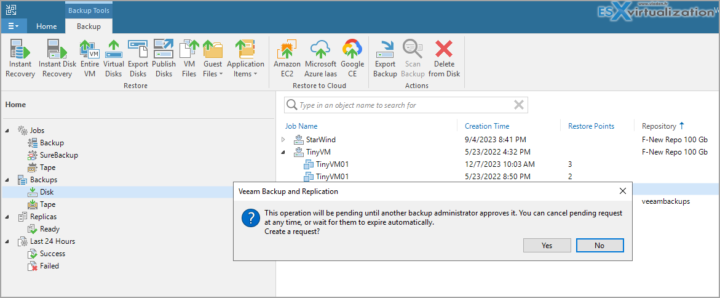
Then if you create another user on your Windows server, then add this user to be an admin (within your Veeam backup console), you can try it. In my case, I did initiate a delete of one restore point of my test-VM. As you can see, I got a message saying that
This operation will be pending until another bakcup administrator approves it.
And you can see that a new node has appeared. This node called Pending aprovals has all the requests for the operations which needs four-eyes authorisation.
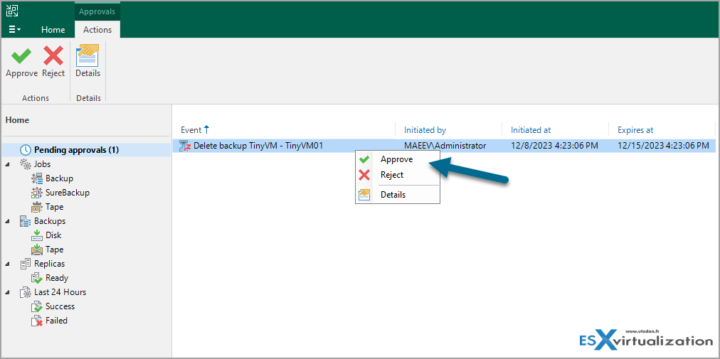
Now let's login as another admin. (Note the change of color of my backup console. For me I have blue color, the other admin did not personalize the default green). And as you can see, the other admin has the option to Approve or Reject (when I was logged in and created the deletion request, I had it grayed out!).
What are the benefits of four-eyes authorization?
Four-eyes authorization provides several benefits for data protection:
- It enhances security by preventing unauthorized or accidental deletion or modification of backups.
- It improves accountability by requiring two users to approve any sensitive operation.
- It simplifies management by reducing manual tasks and errors.
- It supports compliance by ensuring that only authorized users can perform certain operations.
Note: You can also configure other settings related to four-eyes authorization in that dialog box, such as:
- The time limit for approving requests (default is 7 days).
- The email recipients for receiving notifications (default is all administrators).
- The email subject for notifications (default is “Pending Approval”).
- The email body template for notifications (default is “You have received a pending approval request from [requester name] for [operation name]”).
Conclusion
Four-eyes authorization is a new feature in Veeam Backup & Replication 12.1 that helps you protect your data from unauthorized access or modification by requiring two users to approve any sensitive operation in Veeam Backup & Replication. This feature enhances security, improves accountability, simplifies management, and supports compliance.
To enable four-eyes authorization in Veeam Backup & Replication 12.1, you need to configure some settings in Users and Roles > Authorization dialog box.
You can also download a free trial version of Veeam Backup & Replication 12.1 here and try it yourself.
Detailed articles about v12 new features:
- What is Inline Entropy Analysis in Veeam Backup and Replication 12.1
- Veeam 12.1 Download Available – Start Your Download Engines
- Veeam 12.1 Biggest Features
- Your repository is full – How to move your backups to another repository with Veeam backup?
- Practical Tips to protect your Veeam Backup Repositories
- Veeam Backup and Replication v12 – Get the latest ISO
- What is Veeam VHR and how to quickly install and create hardened repository?
- Don’t miss this Veeam v12 Download with latest cumulative patches
- Practical Tips to protect your Veeam Backup Repositories
- Veeam Backup and Replication 12 (Beta2) Installation
- Veeam Backup and Replication 12 (BETA) – adding Hardened Linux Repository
- Veeam Immutable Backups – Your protection against Ransomware
More posts from ESX Virtualization:
- VMware vSphere 8.0 U2 Released – ESXi 8.0 U2 and VCSA 8.0 U2 How to update (NEW)
- What’s the purpose of those 17 virtual hard disks within VMware vCenter Server Appliance (VCSA) 8.0?
- VMware vSphere 8 Update 2 New Upgrade Process for vCenter Server details
- VMware vSAN 8 Update 2 with many enhancements announced during VMware Explore
- What’s New in VMware Virtual Hardware v21 and vSphere 8 Update 2?
- Homelab v 8.0
- vSphere 8.0 Page
- Veeam Bare Metal Recovery Without using USB Stick (TIP)
- ESXi 7.x to 8.x upgrade scenarios
- A really FREE VPN that doesn’t suck
- Patch your ESXi 7.x again
- VMware vCenter Server 7.03 U3g – Download and patch
- Upgrade VMware ESXi to 7.0 U3 via command line
- VMware vCenter Server 7.0 U3e released – another maintenance release fixing vSphere with Tanzu
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)

Does this protect against backup deletion when the target is iSCSI? Which target is best supported by Veeam for such protection?