We're slowly and steady approaching the completion of our Community Study Guide for VCP-DCV certification exam. Today is a day where we go for another topic that is present on the latest VMware Blueprint, that covers all chapters of the VCP-DCV certification exam based on VMware vSphere 8.x. The topic is VCP-DCV on vSphere 8.x Objective 4.19.2 – Configure ESXi firewall.
A short chapter that is easy to check and learn. If you have a lab, you can just test it. If you don't, then read on….
The study guide page VCP8-DCV with all those individual chapters helps you with learning towards VMware certification exam (2V0-21. 23) and to became VCP-DCV on vSphere 8.x. Check the Official VMware VCP-DCV 2023 exam guide (blueprint) here. Also please check the certification requirements (depends on if you hold already a VCP etc..)
You can configure incoming and outgoing firewall connections for a service or a management agent from the vSphere Client or at the command line.
You can use the ESXi Shell or ESXCLI commands to configure ESXi at the command line to automate the firewall configuration.
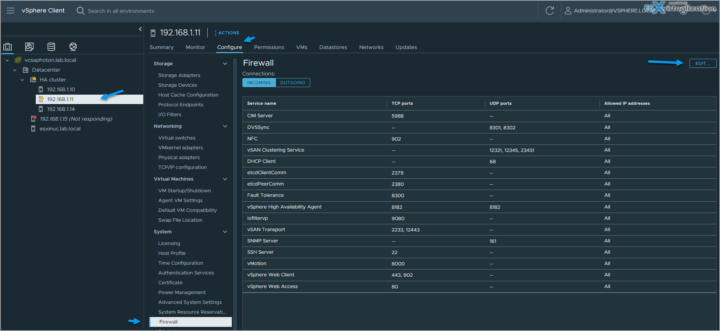
Log in to the vCenter Server by using the vSphere Client and browse to the host in the inventory > Click Configure, then click Firewall under System. You can toggle between incoming and outgoing connections by clicking Incoming and Outgoing.
In the Firewall section, click Edit. Select from one of the three service groups, Ungrouped, Secure Shell, and Simple Network Management Protocol. Select the rule sets to be activated, or deselect the rule sets to be deactivated.
For some services, you can also manage service details by navigating to Configure > Services under System. For some services, you can explicitly specify IP addresses from which connections are allowed.
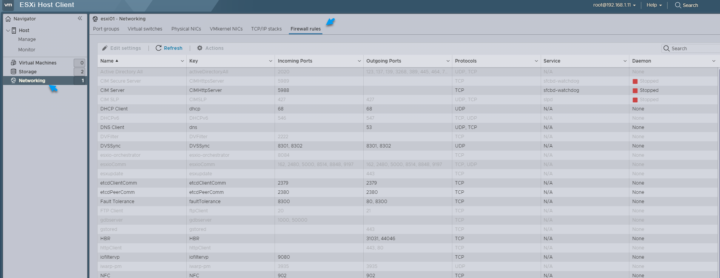
via host client:
Add allowed IP
To restrict traffic, change each service to allow traffic only from your management subnet. You can also deselect some services if your environment does not use them. To update the Allowed IP list for a service you can use the vSphere Client, ESXCLI, or PowerCLI.
Browse to the ESXi host. Click Configure, then click Firewall under System. You can toggle between incoming and outgoing connections by clicking Incoming and Outgoing.
In the Firewall section, click Edit. Select from one of the three service groups, Ungrouped, Secure Shell, and Simple Network Management Protocol.
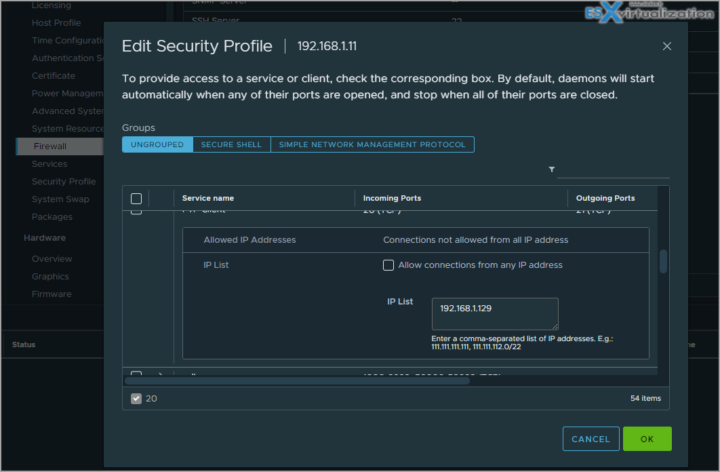
To display the Allowed IP Addresses section, expand a service.
In the Allowed IP Addresses section, deselect Allow connections from any IP address and enter the IP addresses of networks that are allowed to connect to the host.
Separate IP addresses with commas. You can use the following address formats:
192.168.0.0/24
192.168.1.2, 2001::1/64
fd3e:29a6:0a81:e478::/64
Example from the lab…..
For the list of supported ports and protocols in the ESXi firewall, see the VMware Ports and Protocols Tool™ at https://ports.vmware.com/.
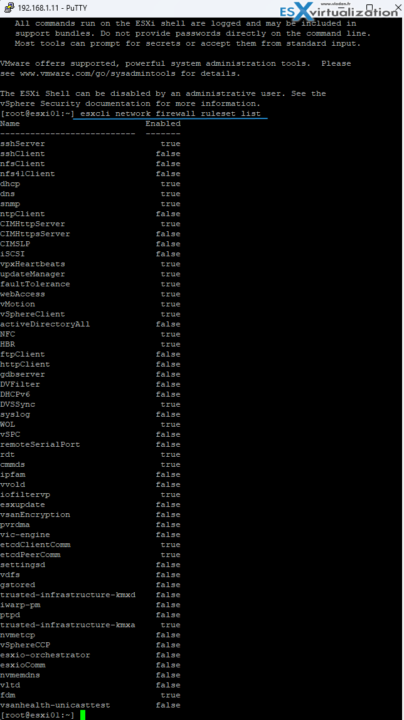
Some of the Firewall commands you can use via ESXi Shell:
esxcli network firewall get – Return the status of the firewall and list the default actions.
esxcli network firewall set –default-action – Set to true to set the default action to pass. Set to false to set the default action to drop.
esxcli network firewall set –enabled – Activate or deactivate the ESXi firewall.
esxcli network firewall load – Load the firewall module and the rule set configuration files.
esxcli network firewall refresh – Refresh the firewall configuration by reading the rule set files if the firewall module is loaded.
esxcli network firewall unload – Destroy filters and unload the firewall module.
esxcli network firewall ruleset list – List rule sets information.
esxcli network firewall ruleset set –allowed-all – Set to true to allow all access to all IPs. Set to false to use a list of allowed IP addresses.
esxcli network firewall ruleset set –enabled –ruleset-id=<string> – Set enabled to true to activate the specified ruleset. Set enabled to false to deactivate the specified ruleset.
esxcli network firewall ruleset allowedip list – List the allowed IP addresses of the specified rule set.
esxcli network firewall ruleset allowedip – add Allow access to the rule set from the specified IP address or range of IP addresses.
esxcli network firewall ruleset allowedip remove – Remove access to the rule set from the specified IP address or range of IP addresses.
esxcli network firewall ruleset rule – list List the rules of each ruleset in the firewall.
You can see that both the ESXi Host Client and vSphere Web Client allow you to open and close firewall ports. But you can only manage predefined ports. Can we create custom firewall ports? Yes, however, you'll need to use the VMware command-line interface (CLI) for the job, and I'm not sure that's a supported scenario.
Hopefully this chapter will help you to study towards VMware VCP-DCV Certification based on vSphere 8.x. Find other chapters on the main page of the guide – VCP8-DCV Study Guide Page.
More posts from ESX Virtualization:
- VMware vSphere 8.0 U1 Announced (NEW)
- VMware vSAN 8.0 U1 What's New? (NEW)
- vSphere 8.0 Page
- Veeam Bare Metal Recovery Without using USB Stick (TIP)
- ESXi 7.x to 8.x upgrade scenarios
- A really FREE VPN that doesn’t suck
- Patch your ESXi 7.x again
- VMware vCenter Server 7.03 U3g – Download and patch
- Upgrade VMware ESXi to 7.0 U3 via command line
- VMware vCenter Server 7.0 U3e released – another maintenance release fixing vSphere with Tanzu
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
- Homelab v 8.0 (NEW)
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)