VMware Virtual Machine (VM) encryption is an essential feature in a data center that provides an additional layer of security to virtual machines. VM Encryption ensures that virtual disks containing sensitive data are encrypted, protecting the data against unauthorized access, theft, and data breaches. This post, VCP-DCV on vSphere 8.x Objective 1.8 – Describe the role of Virtual Machine Encryption in a data center, is part of our VCP8-DCV Study Guide Page. (work-in-progress)
The VMware Exam page is here on VMware’s website. The official code for this exam is 2V0-21. 23. The topic is part of the Official VMware blueprint. (direct link to the PDF). So, let's get back to the topic.
Regardless of which key provider you use, with vSphere Virtual Machine (VM) Encryption you can create encrypted virtual machines and encrypt existing virtual machines. Because all virtual machine files with sensitive information are encrypted, the virtual machine is protected. Only administrators with encryption privileges can perform encryption and decryption tasks.VM encryption will work by applying a new Storage policy to a VM.
VM Encryption is a Policy driven feature. You'll be able to encrypt the VMDK and the VM home files. There is no modification within the guest OS. It does not matter which OS you're running (Linux, Windows, DOS, iOS) or on which storage the VMs files are located (NFS, block storage, VSAN….). The encryption is happening outside of the Guest OS. The guest does not have an access to the keys.
The encryption works also for vMotion but both the source and the destination hosts must support it. We'll see the settings later in this post. It will get a key from the default key manager. It will be per-VM policy application model. It is easy to manage and also scalable.
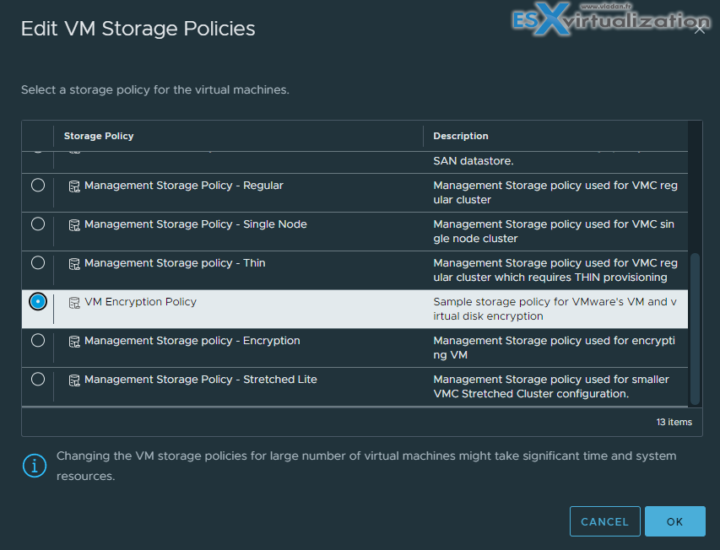
If you have some unencrypted VMs, it's fairly simple to encrypt them via a policy. The example within vSphere Web client bellow – apply encryption policy to two sample VMs…Right click on vm and select VM Policies > Edit Storage Policy.
VM encryption – How it works?
You have an encrypted VM after you have applied an encryption policy too. Then, a randomly generated key is created for each VM, and that key is encrypted with the key from the key manager. When you power On the VM which has the Encryption Storage policy applied to, vCenter retrieves the key from the Key Manager, sends that down to the VM encryption Module and unlocks that key in the ESXi hypervisor.
So all IO coming out from the virtual SCSI device goes through the encryption module before it hits the storage module within the ESXi hypervisor. All IO coming directly from a VM is encrypted.
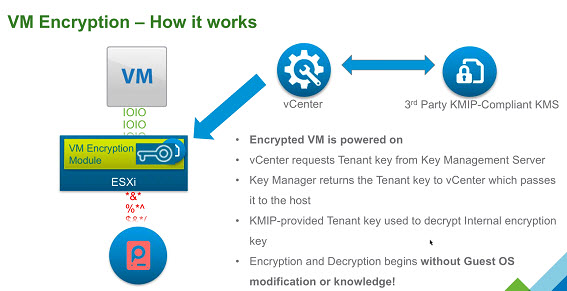
The workflow on activating the VM encryption would look like this:

To Decrypt a VM?
You may ask: How do I decrypt a VM then? It is very simple. By changing the Storage Policy back to a Datastore default. The VM's files, the VMDKs will be decrypted.
What Components Does vSphere Virtual Machine Encryption Not Encrypt?
Some of the files that are associated with a virtual machine are not encrypted or partially encrypted.
- Log files – Log files are not encrypted because they do not contain sensitive data.
- Virtual machine configuration files – Most of the virtual machine configuration information, stored in the VMX and VMSD files, is not encrypted.
- Virtual disk descriptor file – To support disk management without a key, most of the virtual disk descriptor file is not encrypted
Who Manages encryption?
It is not vCenter server, which is only a client. The 3rd party Key management Server (KMS) is the one responsible for the encryption of the key and the management.
With that you may ask who will be able to manage encryption of your VMs? Does all your vSphere admins needs to have access to encryption? Possibly. But possibly NOT. VMware has created a new default role ”
VMware has created a new default role “No Cryptography Administrator“.
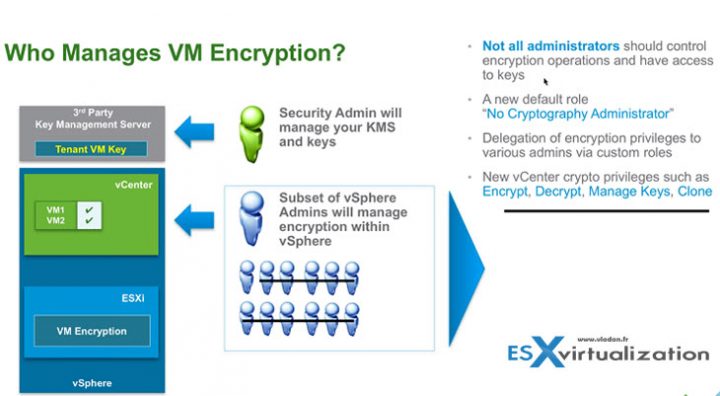
You'll find this new role within the Roles, as usually. The new role will have still all the other privileges like a “standard” admin, but less the Encryption rights.
There Power ON, Off, shut down, vMotion etc…
No operations like:
- Manage key servers
- Manage keys
- Manage encryption policies
- No console access to encrypted VMs
- No upload/download encrypted VMs
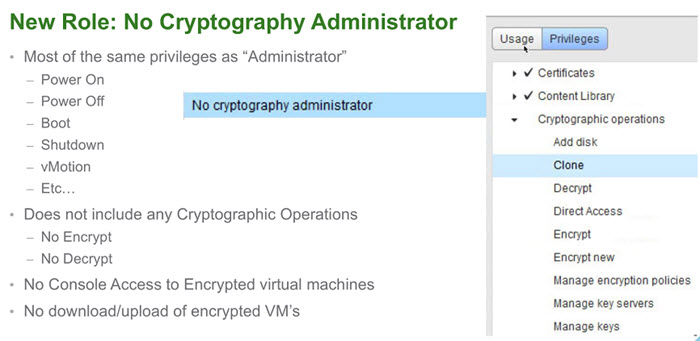
All permissions are customizable.
Hopefully this chapter will help you to study towards VMware VCP-DCV Certification based on vSphere 8.x. Find other chapters on the main page of the guide – VCP8-DCV Study Guide Page.
More posts from ESX Virtualization:
- Homelab v 8.0 (NEW)
- vSphere 8.0 Page (NEW)
- Veeam Bare Metal Recovery Without using USB Stick (TIP)
- ESXi 7.x to 8.x upgrade scenarios
- A really FREE VPN that doesn’t suck
- Patch your ESXi 7.x again
- VMware vCenter Server 7.03 U3g – Download and patch
- Upgrade VMware ESXi to 7.0 U3 via command line
- VMware vCenter Server 7.0 U3e released – another maintenance release fixing vSphere with Tanzu
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)