In this post we'll try to dive into some real threads which you might encounter this year. In no particular order we'll have a look at some ransomware. Where they come from, what they do, how they work and at the end, some possible preventions.
Ryuk ransomware was first observed in August 2018. It is a variant of the Hermes 2.1 ransomware, sold on the underground forum exploit.in from February 2017 by the cybercriminal group CryptoTech for around 300 dollars…
Ryuk uses what they call a dropper. Small app that drops one of the two versions of a data encryption module (32- or 64-bit) on the victim’s computer. The dropper then executes the main attack. After a few minutes of inactivity, Ryuk seeks to stop more than 40 processes and 180 services, in particular those related to antivirus softwares, databases and backups. It ensures its persistence through the creation of a registry keys. An US-based Fortune 500 company, EMCOR, which is one of the victims of this particular attack that took down some of its IT systems.
Ryuk is one of the most active ransomware and it blocks access to the system or the device until the ransom is paid of.
Netwalker ransomware – which is also known as Mailto, is one of the newest variants of the ransomware family. Targets enterprises, government agencies and also healthcare organizations. NetWalker ransomware attacks and compromises the network of its victim and encrypts all the Windows devices that are connected to it. When executed, it uses an embedded configuration that includes ransom notes, file names, and several configuration operations.
You can get infected in two ways:
- via VBS script that is attached to Coronavirus phishing emails
- Executable files that spread through networks
(img source: zdnet)
Tycoon Ransomware – This malware is kind of another type because it uses Java as an spread environment. It is deployed in a trojanized version of the Java Runtime Environment. It is compiled in ImageJ, a Java image format, for malicious purposes.
It targets Windows and Linux environments where the Java image format is used to conduct the attacks. It uses different types of techniques that help it to stay hidden. Tycoon denies access to the administrator after it infects the system.
Then it attacks on the file servers and domain controllers. It leverages weak or compromised passwords and is a common attack vector that exploits servers for malware.
(img: zdnet)
Snake – This ransomware, also called EKANS spelled backwards, is targetting many industrial networks and is able to put out of work many industrial control system processes. It gets access to the administrator credentials and then encrypts all the files on the network. The victim has no other choice to pay, or to restore all the systems from backups (if any).
How do you get Snake? Via phishing email….
It works by removing the target computer’s Shadow Volume Copies (VSS) and then shuts down a number of processes. Clever. Snake ransomware was discovered by researchers from MalwareHunterTeam.
Once encryption is complete, there is a note is created on the user’s desktop called “Fix-Your-Files.txt”. The text file basically shows you how your data is now locked with “military grade encryption algorithms” and that you can get them unlocked by purchasing a decryption tool from the hackers by contacting a specific email address… Pretty common.
(img: phishingtackle)
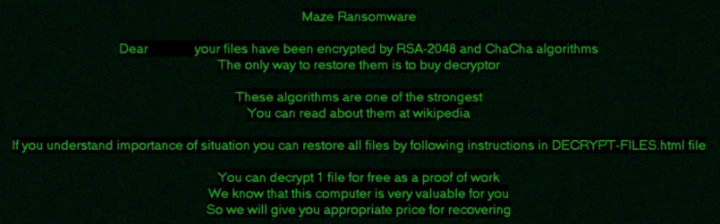
Maze – encrypts all files and demands for the ransom to recover the files. Typical behavior. It also uses different tacktiques and threatens to release sensitive information on the internet if the victim fails to pay the demanded ransom. The target are big compagnies, such as Xerox, Canon….
The malware has used different techniques to gain entry, mainly using exploits kits, remote desktop connections with weak passwords or via email impersonation or, as in the Italian case, via different agencies or companies, i.e. the Italian Revenue Agency. These emails came with a Word attachment that was using macros to run the malware in the system.
Maze is a complex piece of malware that uses some tricks to frustrate analysis right from the beginning. Maze is a ransomware created by skilled developers. It uses a lot of tricks to make analysis very complex by disabling disassemblers and using pseudocode plugins.
Disable macros in Office programs and never enable them unless it is essential to do so.
(img: VMware)
What are some preventive measures against ransomware attacks?
- Start educating employees with security awareness training to create a cyber-resilient working culture.
- Use a strong password policy to reduce risks of password sharing at work and the habit of password reuse.
- Keep a backup of sensitive data on offsite data centers and limit access to confidential files or the organization’s assets.
- Beware of clicking links or attachments that come within unsolicited emails.
Backup, backup, and backup. AND protect your backups so they don't get encrypted!
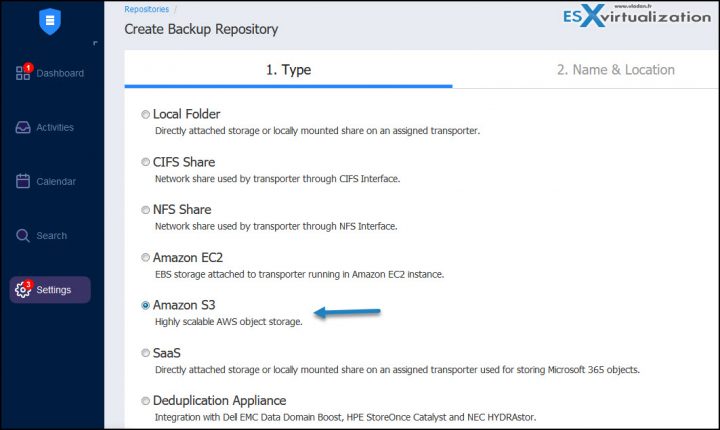
This is becoming an essential strategy against complete loss of your data (if you don't want to pay). It's important that you have a backups stored elsewhere, with some kind of airgap or immutability. Many backup vendors are jumping into this and providing you with a possibility to backup to the cloud where you can setup an immutability. You'll be able to set an immutability flag (It is a native function called “object lock” present within Amazon AWS.
This immutability is to prevent accidental deletion of data by admins, malware, or an admin with bad intentions. (Yes, even that can happen). After you set the lock for let's say 3 days, your backups cannot be deleted during that period. It is as simple as that. It is an object lock which applied to every bit which is copied to the cloud storage.
Nakivo Backup and Replication has recently released bring this functionality and is able to use immutability providing Ransomware-Proof Backups with Amazon S3 Object Lock. This Amazon S3 Object Lock functionality uses the write-once-read-many (WORM) model meant to ensure that objects are immutable for as long as required. Once set, the retention period cannot be shortened or disabled, not even by the root user.
Amazon S3 Object Lock support allows companies to:
- Protect their backups stored in Amazon S3 from overwriting and deletion.
- Set retention periods to keep objects immutable for as long as you need.
- Protect their backup data against ransomware and meet compliance requirements
Check out Nakivo here.
More posts from ESX Virtualization:
- vSphere 7 U2 Released
- vSphere 7.0 Download Now Available
- vSphere 7.0 Page [All details about vSphere and related products here]
- VMware vSphere 7.0 Announced – vCenter Server Details
- VMware vSphere 7.0 DRS Improvements – What's New
- How to Patch vCenter Server Appliance (VCSA) – [Guide]
- What is The Difference between VMware vSphere, ESXi and vCenter
- How to Configure VMware High Availability (HA) Cluster
VMware Education (On Demand Courses)
- VMware vSphere: Install, Configure, Manage [v7] – On Demand
- VMware vSphere: Optimize and Scale [v7] – On Demand
- VMware vSphere: Install, Configure, Manage [V6.7] – On Demand
- VMware NSX-T Data Center: Troubleshooting and Operations [V2.4] – On Demand
- VMware vSphere: What's New [V6.7 to V7] – On Demand
- VMware vSphere: Optimize and Scale [V6.7] – On Demand
- VMware VCP Exam Vouchers – VCP exam vouchers may be used as payment for different VMware certification exams:
***********************************
VCA | VCP | VCAP or VCIX exam vouchers
***********************************
- VMware Learning Credits – Learning Credits provide the dual benefit of funding a well-trained IT staff, along with discounts options of up to 15 percent. Customers can schedule training when and how they need it. Customers can buy credits at the time of license purchase or as a stand-alone purchase
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)