VMware ESXi hypervisor has a default password complexity turned on. It is to restrict admins using week passwords which is good. The ESXi password restrictions are set by the Linux PAM module pam_passwdqc, because VMware ESXi uses that module within the hypervisor. In this post, we will recap how to disable VMware ESXi complex passwords.
We will show the modification option and where to go on the ESXi host (it is a per-host advanced setting) for the ones who haven't looked at it yet, but we also warn you that it is definitely not a best practice to do that on production systems. We'll also show how to reset things back to default.
You might find it useful on a demo/lab system where you don't want to fill in strong passwords while learning some CLI commands for example. You might just have an ESXi system which is a standalone system for monitoring purposes and you don't want to bother with complex passwords. The use cases can be different.
ESXi enforces password requirements for access from the Direct Console User Interface, the ESXi Shell, SSH, or the VMware Host Client.
By default, you have to include a mix of characters from four character classes: lowercase letters, uppercase letters, numbers, and special characters such as underscore or dash when you create a password. This is a hard requirement with the default password policy for ESXi.
By default, password length is more than 7 and less than 40 characters. Also, passwords cannot contain a dictionary word or part of a dictionary word.
Before we jump into the settings itself, let's talk about the requirements that ESXi 6.x has.
The password policy in ESXi 6.x has some requirements, such as length, complexity, uppercase etc:
- Passwords must have characters from at least three character classes. (Uppercase characters (A-Z), Lowercase characters (a-z), Digits (0-9), special characters (~!@#$%^&*_-+=`|\(){}[]:;”‘<>,.?/)
- Passwords which has characters from three character classes must be at least seven characters long.
- Passwords which has characters from all four character classes must be at least seven characters long.
- An uppercase character at the beginning of a password does not count toward the number of character classes used.
- A number that ends a password does not count toward the number of character classes used.
- The password cannot have a dictionary word or part of a dictionary word. This prevents hackers which using a “dictionary method” with their BOTS to guess your password.
Disclaimer:
Use on your own risk and on a lab system.
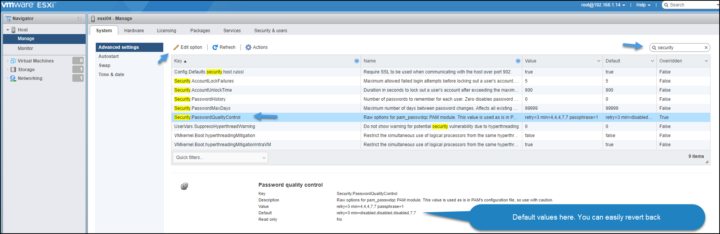
After login into the ESXi host as a root user, go to System > Advanced Settings and put the string into the search window to filter and hit enter.
The password complexity is enforced by a policy on the ESXi host. There is an advanced setting called “Security.PasswordQualityControl”
The default values are:
ESXi 6.x setting: retry=3 min=disabled,disabled,disabled,7,7
We will change it temporarily to let’s say:
retry=3 min=4,4,4,7,7 passphrase=1
We can use a passphrase with a single word only for our password.
To do so, type “security” into the search box > select the “Security.PasswordQualityControl” > then click Edit Option.
Security Default Settings on ESXi
You can change the required length and character class requirement or allow passphrases, but let's first disable the complexity by entering some numbers into the X1 for example.
As you can see from the image above, you have a default setting there. At any time, you can revert back to defaults by a simple click.
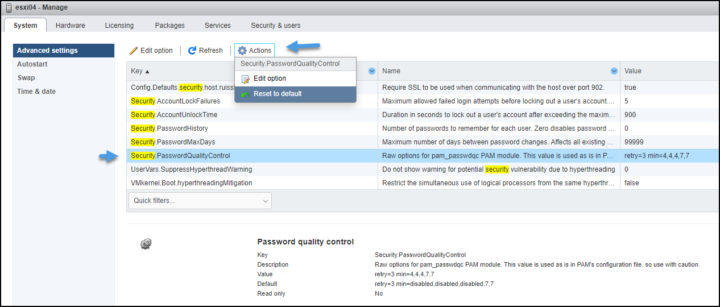
To do so, you just once again select the “Security.PasswordQualityControl” > Then click the Actions > Reset to default.
Reset back to default option
The following options may be passed to the module:
min=N0,N1,N2,N3,N4
Let's break down the different options:
N0 – This is the number of characters which are necessary when the password has only one character class.
N1 – This one is the number of characters required when the password contains characters from two character classes.
N2 – Third one is the number of characters required when the password contains a phrase.
N3 – Next one is a number of characters necessary when the password contains characters from three character classes.
N4 – This position show us a number of characters which are required when the password has characters from four character classes.
Note: The first and last position does not count to the complexity level, so if you have password starting (ending) with an uppercase, this won’t count for the complexity.
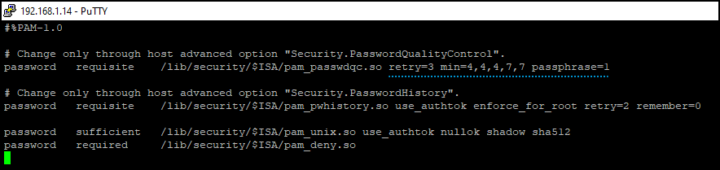
You can also verify the settings through an SSH client such as Putty. You can download a free Putty client from this page.
After connecting to your ESXi host, you can open the config file via this command
vi /etc/pam.d/passwd
Password complexity settings view via Putty client
Here is the man page of pam_passwdqc – check it out! With plenty of examples.
Update: Reboot your ESXi host to validate.
Final Words:
As I said in the beginning, changing the defaults is something I don’t recommend doing on production systems, but if you’re running a lab environment and you don’t want always to type complex passwords when connecting to your ESXi hosts, this might be the way. You can change the settings via SSH client or via Host client only using your web browser.
Don’t consider this as some breakthrough article as most of the time you manage ESXi hosts via vCenter anyway so this post is most likely only for standalone and isolated hosts.
VMware ESXi and its default security settings are hardened to prevent easy access and softening those rules are not supported by VMware. It only makes sense to respect it but you might have some corner case scenarios like lab learning or simple monitoring systems where you do not need any password complexity rules.
More from ESX Virtualization
- 5 Ways to Change Hostname of your ESXi host
- How To Disable Timeout on your ESXi Host Client – The Easy Way [Tip]
- How to reset ESXi 6.x root password and under which conditions
- VMware API Explorer Is a Free Built-in Utility in VCSA
- V2V Migration with VMware – 5 Top Tips
- ESXi Free Version – 3 Ways to Clone a VM
- What is ESXi Compatibility Checker?
- How To SlipStream Latest VMware ESXi patches into an Installation ESXi ISO File
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)

I think you missed the “reboot” step. I remember doing this last time because our fav password did not fit the min req so I had to loosen this up and I think I had to reboot for it to take effect. It’s been a couple of years so I could be wrong.
Hey Totie, absolutely. Reboot is necessary otherwise it won’t work. Thanks for the reminder. -:)
too many word, but what is the answer for the question:
How to disable VMware ESXi complex passwords?
is it: retry=3 min=4,4,4,7,7 passphrase=1
Any option to set ESXi 6.5 root passowrd history