Funny because we have blogged just recently about What is VMware ESXi Lockdown mode. We'll definitely cover more on today's topic.
vSphere 6.5 is slightly different ( from the UI perspective) compared to vSphere 6.0. The TABs are different, the UI has been streamlined in order to facilitate navigation or do fewer clicks for configuration and administration tasks.
Passing a VCP exam has some requirements. Depending if you are current VCP or not you may need to get some training first. In order to pass the VCP6.5-DCV certification exam, you must attend one of the required training courses and pass the vSphere 6 Foundations Exam or vSphere 6.5 Foundations Exam.
Attend one of those required courses:
VMware vSphere: Install, Configure, Manage [V6.5]
VMware vSphere: Install, Configure, Manage [V6.5] – On Demand
VMware vSphere: Optimize and Scale [V6.5]
VMware vSphere: Optimize and Scale [V6.5] – On Demand
VMware vSphere: Install Configure Manage plus Optimize & Scale Fast Track
VMware vSphere: Skills for Public Sector Customers [V6.5]
VMware vSphere: Fast Track [V6.5]
VMware vSphere: Troubleshooting Workshop [V6.5]
You can download your free copy via this link – Download Free VCP6.5-DCV Study Guide at Nakivo.
The exam prep guide (previously called “Exam Blueprint” ) PDF is a good start. Not only it lists all the objectives, but also, at the end of the document, you can find shortcuts to the different PDFs which are necessary for the study. We'll try to get all the information to each blog post, with links to sections presenting too large volume to be handled within a blog post. Already, those blog posts seem to be quite MEGA posts with over 2000 words each … -:) .
Let's get started. The links are only “hrefs” to the section within this document. Not external links.
VCP6.5-DCV Objective 2 – Secure ESXi and vCenter Server
- Configure Encrypted vMotion
- Describe Secure Boot
- Harden ESXi hosts
- Enable/Configure/Disable services in the ESXi firewall
- Change default account access
- Add an ESXi Host to a directory service
- Apply permissions to ESXi Hosts using Host Profiles
- Enable Lockdown Mode
- Control access to hosts (DCUI/Shell/SSH/MOB)
- Harden vCenter Server
- Control datastore browser access
- Create/Manage vCenter Server Security Certificates
- Control MOB access
- Change default account access
- Restrict administrative privileges
- Understand the implications of securing a vSphere environment
Configure Encrypted vMotion
With vSphere 6.5, vSphere, vMotion always uses encryption when migrating encrypted virtual machines. For virtual machines that are not encrypted, you can select one of the encrypted vSphere vMotion options.
For virtual machines that are encrypted, migration with vSphere vMotion always uses encrypted vSphere vMotion. You cannot turn off encrypted vSphere vMotion for encrypted virtual machines.
- Right-click a VM and select Edit Settings > VM Options > Click Encryption, and select an option from the Encrypted VMotion drop-down menu.
The default is Opportunistic.
- Disabled – Do not use encrypted vSphere vMotion.
- Opportunistic – Use encrypted vSphere vMotion if the source and destination hosts support it (both sides has to be on ESXi 6.5 version). Only ESXi versions 6.5 and later use encrypted vSphere vMotion.
- Required – Allow only encrypted vSphere vMotion. If the source or destination host does not support encrypted vSphere vMotion, migration with vSphere vMotion is not allowed.
For unencrypted VMs – All variants of encrypted vSphere vMotion are supported. Shared storage is required for migration across vCenter Server instances.
For encrypted VMs – migration across vCenter Server instances is not supported.
Describe Secure Boot
With secure boot enabled, a machine refuses to load any UEFI driver or app unless the operating system boot loader is cryptographically signed. Starting with vSphere 6.5, ESXi supports secure boot if it is enabled in the hardware.
Figure 1: VCP6.5-DCV Study Guide – UEFI Secure Boot
The ESXi secure boot process:.
-
ESXi bootloader contains a VMware public key. The bootloader uses this key to verify the signature of the kernel and a small subset of the system that includes a secure boot VIB verifier.
-
The VIB verifier verifies every VIB package that is installed on the system.
- The system boots with the root of trust in certificates that are part of the UEFI firmware.
Harden ESXi hosts
Only a limited set of services runs by default on each ESXi host.
- ESXi Shell and SSH are disabled by default.
- You can configure additional features such as lockdown mode, certificate replacement, and smart card authentication for enhanced security.
- An ESXi host is also protected with a firewall. You can open ports for incoming and outgoing traffic as needed but should restrict access to services and ports.
- Using the ESXi lockdown mode and limiting access to the ESXi Shell can further contribute to a more secure environment.
- Hosts are provisioned with certificates that are signed by the VMware Certificate Authority (VMCA) by default.
- You might consider using UEFI Secure Boot for your ESXi system.
- Join ESXi hosts to an Active Directory (AD) domain to eliminate the need to create and maintain multiple local user accounts. Using AD for user authentication simplifies the ESXi host configuration, ensures password complexity and reuse policies are enforced and reduces the risk of security breaches and unauthorized access. (Note: if the AD group “ESX Admins” (default) exists then all users and groups that are assigned as members to this group will have full administrative access to all ESXi hosts the domain.)
- Use ESXi lockdown mode – Enabling lockdown mode disables direct access to an ESXi host requiring the host be managed remotely from vCenter Server. Two modes available (normal and strict). Tip: What is ESXi Lockdown Mode? Users on the Exception Users list can access the host from the ESXi Shell and through SSH if they have the Administrator role on the host and if these services are enabled. This access is possible even in strict lockdown mode. Leaving the ESXi Shell service and the SSH service disabled is the most secure option
- ESXi.set-shell-timeout – sets a timeout to limit how long the ESXi shell and SSH services are allowed to run.
Check the VMware Security Hardening guides at VMware Blog.
Enable/Configure/Disable services in the ESXi firewall
For each ESXi host, you can create firewall rules.
Connect via vSphere web client > Configure > System > Security Profile > Firewall section > Edit > Select Rule > Enable/disable.
Select the rule sets to enable, or deselect the rule sets to disable. You can change startup policy to have a particular service started with the host or by port usage. Some services allows configuring IP address from which connections are permitted.
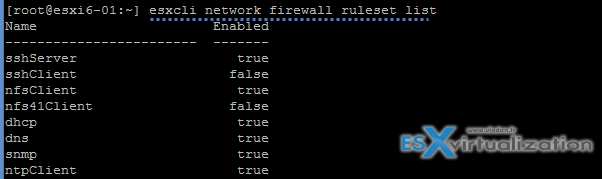
Check which services are active
esxcli network firewall ruleset list
Open firewall port via CLI:
esxcli network firewall ruleset set -e true -r httpsClient
Change default account access
The roles for ESXi are much simpler than roles for vCenter server, which we have covered in the VCP6.5-DCV Objective 1 – Configure and Administer Role-based Access Control. But also, the same as for vCenter server, there are some predefined roles and some other accounts for when the ESXi is managed via vCenter.
Since 6.0 there is a possibility also to use ESXCLI (via putty session for example, or directly via console) for account management. There are some commands for managing ESXi local user accounts.
esxcli system account
Predefined Roles:
- Read Only – Allows a user to view objects associated with the ESXi host but not to make any changes to objects.
- Administrator – Administrator role.
- No Access – No access role. This role is the default role. You can override the default role.
There is a single root user created by default when you install ESXi.
esxcli system account list
gives us this:
ESXi Privileges:
Best practice is to create at least one named user account, assign it full administrative privileges on the host, and use this account instead of the root account. Set a highly complex password for the root account and limit the use of the root account. Do not remove the root account.
For all versions of ESXi, you can see the list of predefined users in the /etc/passwd file.
root user – root user account has the Administrator role. That root user account can be used for local administration and to connect the host to vCenter Server. It's the account with the highest privilege.
For better auditing, create individual accounts with Administrator privileges. Set a highly complex password for the root account and limit the use of the root account, for example, for use when adding a host to vCenter Server. Do not remove the root account.
Best practice is to ensure that any account with the Administrator role on an ESXi host is assigned to a specific user with a named account. Use ESXi Active Directory capabilities, which allow you to manage Active Directory credentials. You can remove the access privileges for the root user. However, you must first create another permission at the root level that has a different user assigned to the Administrator role.
vpxuser – vCenter Server uses vpxuser privileges when managing activities for the host. vCenter Server has Administrator privileges on the host that it manages. For example, vCenter Server can move virtual machines to and from hosts and change virtual machine configuration.
The vCenter Server administrator can perform most of the same tasks on the host as the root user and also schedule tasks, work with templates, and so forth. However, the vCenter Server administrator cannot directly create, delete, or edit local users and groups for hosts. Only a user with Administrator privileges can perform these tasks directly on a host.
DCUI user – the DCUI user runs on hosts and acts with Administrator rights. This user’s primary purpose is to configure hosts for lockdown mode from the Direct Console User Interface (DCUI).
This user acts as an agent for the direct console and cannot be modified or used by interactive users.
Add an ESXi Host to a directory service
You can configure a host to use a directory service such as Active Directory to manage users and groups. When you add an ESXi host to Active Directory, the DOMAIN group ‘ESX Admins' is assigned full administrative access to the host if it exists.
A special AD group named “ESX Admins” shall be manually created before a host is joined to Microsoft AD. Why? Because like this All members of this group (ESX admins) are automatically assigned to the Administrator role on the host when this host is joined to an AD. If not the permissions have to be applied manually.
Select your host > Configure > System > Authentication Services > Join Domain > Enter your Microsoft domain name > Use a user and password who has permissoin to join the host to the domain > Click OK.
Apply permissions to ESXi Hosts using Host Profiles
Host profiles allow you to “standardize” configurations for ESXi hosts and automate compliance for settings you have set on a reference host. Host profiles allow you to control many aspects of host configuration including memory, storage, networking, and so on.In some cases, host profiles can be also useful when for example you need to reset esxi root password on a host.
- Select the host profile > Click Actions > Edit Settings > Expand Security and Services
- Select the Permission Rules folder > click the Plus Sign
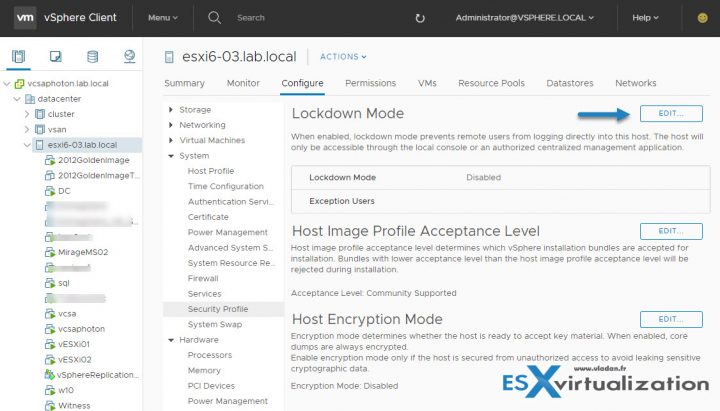
Enable Lockdown Mode
Lockdown Modes:
- Disabled – Lockdown mode is disabled.
- Normal – The host can be accessed through vCenter Server. Only users who are on the Exception Users list and have administrator privileges can log in to the Direct Console User Interface. If SSH or the ESXi Shell is enabled, access might be possible.
- Strict – The host can only be accessed through vCenter Server. If SSH or the ESXi Shell is enabled, running sessions for accounts in the DCUI.Access advanced option and for Exception User accounts that have administrator privileges remain enabled. All other sessions are terminated. DCUI is stopped.
Select your host > Configure > System > Security Profile > Edit.
Accounts in the Exception User list for lockdown mode who have administrative privileges on the host. The Exception Users list is meant for service accounts that perform very specific tasks. Adding ESXi administrators to this list defeats the purpose of lockdown mode.
Where to add an account to the Exception Users list?
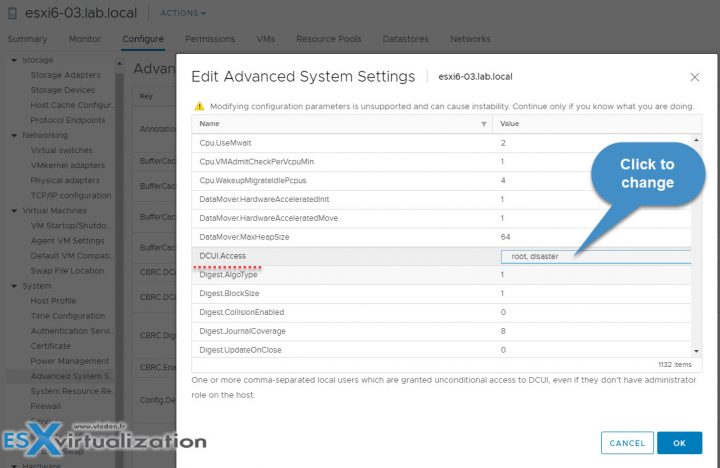
You’d have to first create a local ESXi user and then specify this advanced settings on per-host base. So in my case, I created a sample local ESXi user called “disaster” through ESXi host client which is a local ESXi user.
So in order to modify the Exception users list, you’ll have to use the vSphere HTML5 client of vSphere Web Client. To access this setting you Select your host > System > Advanced System Settings > within the list find the DCUI.Access > click to add another local ESXi user there. The root user is already present there by default.
The exception users can only perform tasks for which they have privileges for. So even if you create your local user and put him on the Exceptions list, the user won’t be able to connect unless you give him a privilege.
Control access to hosts (DCUI/Shell/SSH/MOB)
You can control the access to the DCUI/Shell and SSH. The MOB is the managed object browser (MOB) and provides a way to explore the VMkernel object model. vSphere 6.0 and later has, the MOB is disabled by default because it could be exploited by hackers.
To Enable MOB:
Select host > Advanced System Settings > Advanced > Config.HostAgent.plugins.solo.enableMob > modify the value.
Harden vCenter Server
If the local Windows administrator account currently has the Administrator role vCenter Server, remove that role and assign the role to one or more named vCenter Server administrator accounts.
You can create custom roles or use the No cryptography administrator role for administrators with more limited privileges.
- Minimize access – do not let users to login directly to vCenter server host machine.
- Restrict DB user privileges – The database user requires only certain privileges specific to database access. Some privileges are required only for installation and upgrade. You can remove these privileges from the database administrator after vCenter Server is installed or upgraded.
- Restrict Datastore Browser Access – Assign the Datastore.Browse datastore privilege only to users or groups who really need those privileges
- Modify password policy for vpxuser – By default, vCenter Server changes the vpxuser password automatically every 30 days.
Check vSphere 6.5 security guide for further hardening tips. (Page 98-110) There are also details about default open ports (too large to list it all here), different sections for vCenter on Windows and for vCSA (Linux appliance).
Control datastore browser access
VMware vSphere allows to grant or refuse access to individual objects of the infrastructure. This can be a host, folder, datastore etc. Datastore access is granted via the Datastore.Browse datastore privilege.
Assign the Datastore.Browse datastore privilege only to users or groups who really need those privileges. Users with the privilege can view, upload, or download files on datastores associated with the vSphere deployment through the Web browser or the vSphere Web Client.
Create/Manage vCenter Server Security Certificates
When ESXi and vCenter Server communicate via TLS/SSL for management traffic. In vSphere 6.0 and later, vCenter Server supports the following certificate modes for ESXi hosts:
VMware Certificate Authority (default) – Use this mode if VMCA provisions all ESXi hosts, either as the top-level CA or as an intermediate CA. By default, VMCA provisions ESXi hosts with certificates. In this mode, you can refresh and renew certificates from the vSphere Web Client.
Custom Certificate Authority – Use this mode if you want to use only custom certificates that are signed by a third-party or enterprise CA. In this mode, you are responsible for managing the certificates You cannot refresh and renew certificates from the vSphere Web Client. Unless you change the certificate mode to Custom Certificate Authority, VMCA might replace custom certificates for example, when you select Renew in the vSphere Web Client.
Thumbprint Mode – vSphere 5.5 used thumbprint mode and this mode is still available as a fallback option for vSphere 6.x. In this mode, vCenter Server checks that the certificate is formatted correctly, but does not check the validity of the certificate even expired certificates are accepted. Do not use this mode unless you encounter problems that you cannot resolve with one of the other two modes. Some vCenter 6.x and later services might not work correctly in thumbprint mode.
Using Custom ESXi Certificates – If your company policy requires that you use a different root CA than VMCA, you can switch the certificate mode in your environment after careful planning. The recommended workflow is as follows:
- Obtain the certificates that you want to use.
- Remove all hosts from vCenter Server.
- Add the custom CA's root certificate to VECS (VMware Endpoint Certificate Store)
- Deploy the custom CA certificates to each host and restart services on that host.
- Switch to Custom CA mode. See “Change the Certificate Mode,” on page 56.
- Add the hosts to the vCenter Server system.
Switching from Custom CA Mode to VMCA Mode
If you are using custom CA mode and decide that using VMCA works beĴer in your environment, you can perform the mode switch after careful planning. The recommended workflow is as follows.
- Remove all hosts from the vCenter Server system.
- On the vCenter Server system, remove the third-party CA's root certificate from VECS.
- Switch to VMCA mode. See “Change the Certificate Mode,” on page 56. (Link as above).
- Add the hosts to the vCenter Server system.
Control MOB access
See section “Control access to hosts (DCUI/Shell/SSH/MOB)”.
Change default account access
With this, we understand that we must change the default roles. Check Change default account access section above.
Restrict administrative privileges
Not all administrator users must have the Administrator role. You might want to create a custom role with the appropriate set of privileges and assign it to other administrators. Users with the vCenter Server Administrator role have privileges on all objects in the hierarchy.
Follow the principle of least privilege. Clone and customize role for nodes you need, and then assign this role to administrators.
Understand the implications of securing a vSphere environment
Being secured but not too “locked”, have a good balance between security and manageability. Making any changes to the security of the vSphere environment might have perhaps large impacts on the manageability of the environment for you and your team.
You should always analyze your needs, your risks, and your requirements. Then change the security of your environment.
There is more to come, more to study. Check our VCP6.5-DCV Study Guide Page.
More from ESX Virtualization:
- What is The Difference between VMware vSphere, ESXi, and vCenter
- How-to Create a Security Banner for ESXi
- What is VMware Memory Ballooning?
- VMware Configuration Maximums
- How to Install latest ESXi VMware Patch – [Guide]
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)