If you don't change the default VMware vCSA password policy for an administrator within the vSphere.local domain, you will get a notification 30 days before the password expires.
This is not the root password of the VCSA appliance. We wrote how to reset root password for VCSA appliance here. (Post include a detailed video too). This is not either a notification of password expiry for Administrator from Microsoft Active Directory (AD) domain.
Usually, the right way to integrate VMware vCSA (or vCenter server installed on Windows) to an existing Microsoft Active Directory (AD) environment, is to join VCSA to a Microsoft AD and add a new identity source (Microsoft AD) so you can manage the vCenter with your existing corporate environment. We have written a post on it here.
But this is not always the case. There can be vSphere installations which are isolated from production environments, there can be other use cases such training/learning systems which do not use AD at all. In all those cases you'll be using the domain which you'll set up during the VCSA deployment – vSphere.local is the default (but you can perfectly deploy and setup another domain). And in this case you'll be dealing with
But the main point of this post is to get to the place where you can change this setting.
VCSA 6.5 Password Expires in X days Notification – How to change?
Note that you only see the password expiry for the default vSphere.local domain (not your Microsoft AD).
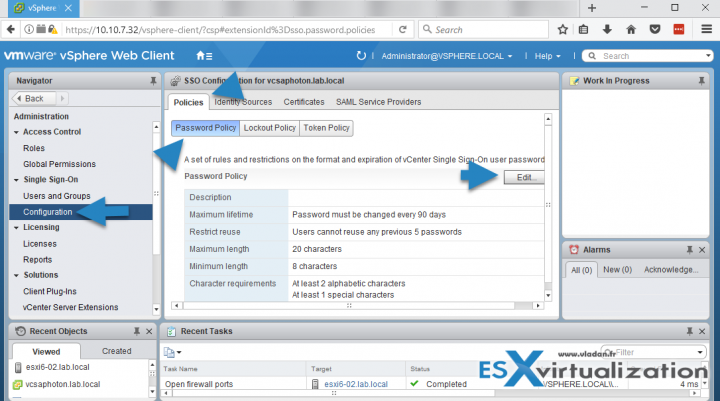
The password for administrator account is managed by vCenter Single Sign-On password policy, which applies only to the vSphere.local (or the one you have setup during the install) domain.
The steps to change the vCenter SSO policy:
Connect to your vCSA appliance Go to Home > Select Single Sign-ON > Configuration > Policies > Password Policy > Edit.
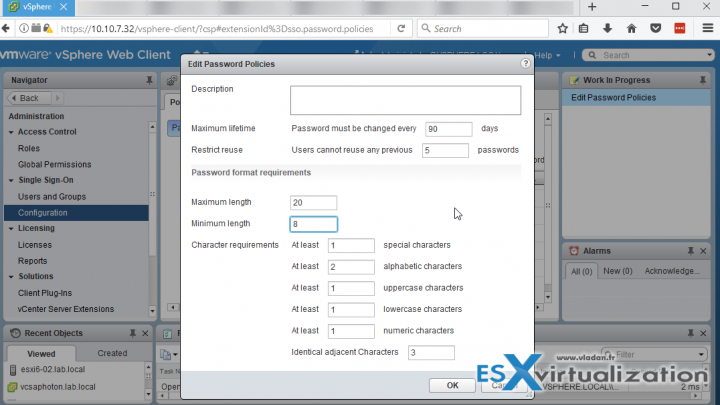
There you'll get a possibility to edit the existing policy which fixes the password behavior. At the same time, you'll have a possibility to change the password complexity requirements…
vCSA Password requirements and Lockout behavior.
By default, this password must have this following requirement:
- At least 8 characters
- At least one lowercase character
- At least one numeric character
- At least one special character
The password for this user cannot be more than 20 characters long.
Administrators can change the default password policy.
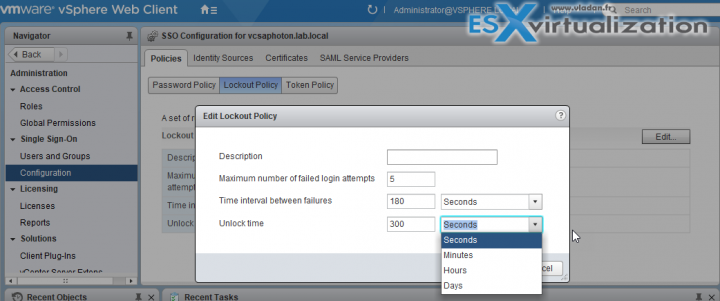
vCenter Single Sign-On Lockout Behavior
I think it's worth to note the lockout behavior while we're here. The lockout behavior is basically fixing what happens when you enter your administrator password wrong for 5 times (default). The account is locked out and during this time you can't do anything, just wait….
What's happening is that you have to wait 180 seconds before you can start logging back again. Users are locked out after a preset number of consecutive failed attempts.
By default, users are locked out after five consecutive failed attempts in three minutes and a locked account is unlocked automatically after five minutes. You can change these defaults using the vCenter Single Sign-On lockout policy
You can change these defaults using the vCenter Single Sign-On lockout policy.
Best practices?
- If you're using the Microsoft AD as an identity source then you'll manage your users/passwords/password lockout policies/restrictions through Microsoft AD.
- VMware recommends to configure NTP, and also restrict network access by opening only the required ports for vCenter/vCSA in your firewall. (Check the full list of ports through VMware Docs).
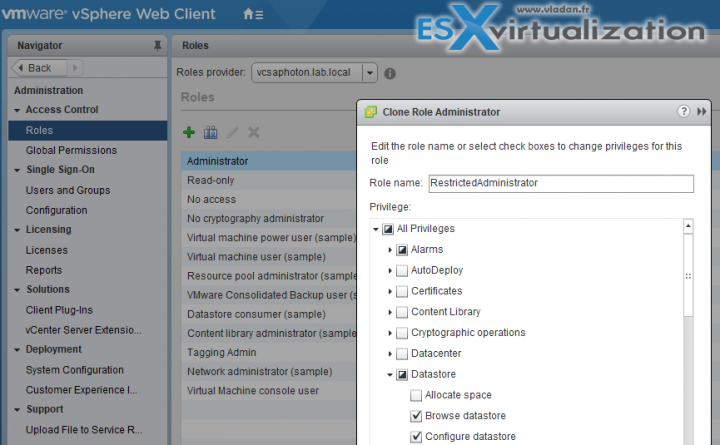
- Create a custom role instead of default administrator – Not all administrator users must have the Administrator role. Instead, create a custom role with the appropriate set of privileges and assign it to other administrators.
You can clone the default admin and then uncheck privileges which you don't want the other administrators can use.
- Datastore access – Assign the Datastore > Browse Datastore privilege only to users or groups who really need those privileges. Users with the privilege can view, upload, or download files on datastores associated with the vSphere deployment through the Web browser or the vSphere Web Client.
Wrap-up:
To well understand the separation of the default vSphere.local (or the one you have set up during the deployment of VCSA) and the Microsoft AD is essential. Since I had received few questions on this recently, I thought that it was a good way to enforce the knowledge with a blog post.
Worth to note that in case you deploy Platform service component (and SSO) on a separate VM you'll have to change the default policy on the PSC (not on vCSA). For that, just connect to the PSC VM through this url:
https://psc_IP/psc
Well, that's about it. Stay tuned for more.
More from ESX Virtualization
- How to unlock the VMware VCSA root password?
- How To Reset ESXi Root Password via Microsoft AD
- How To Create VMware ESXi ISO With Latest Patches
- How to reset ESXi 6.x root password and under which conditions
- How to reset Single Sign-On (SSO) password in vSphere
Stay tuned through RSS, and social media channels (Twitter, FB, YouTube)