NSX for vSphere 6.1 shall be available during VMworld or the week after VMworld US. During the presentation which has been done by Brad Hedlund who works as an engineering architect at VMware, we had the chance to see all the features introduced and presented.
There is quite a few of them and it seems that VMware also going to come out with NSX for Multi hypervisor, as well as OpenStack Integration. Also interesting in this post – Micro Segmentation which allows to protect inside of the datacenter – is feature which is part of NSX for vSphere 6.1.
While the product's name announced is NSX for 6.1 one would think that vSphere 6.1 is already out. The reality is that the vSphere 6 (or 6.1) hasn't been announced yet and for now there is still the Public Beta of vSphere 6 where you can join, but you can't talk about what's in. The only info from the public beta that is out is the info about VVoLS. Virtual volumes (VVoLS) encapsulate virtual disks and other virtual machine files, and natively store the files on the storage system.
What's new in NSX for vSphere 6.1?
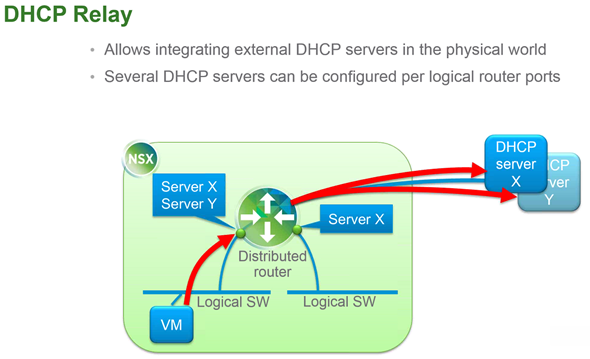
DHCP Relay
This is new feature which is new in NSX for vSphere 6.1 and allows integrating external DHCP servers in the physical world. There can be several DHCP servers which can be configured per logical router ports.
You can have distributed router where the kernel module in all the hypervisors which is providing the default gateway for the VMs, but also providing the routing from one logical switch to another right in the kernel or routing between logical switches and port groups.
It's possible to setup external DHCP servers to respond to DHCP requests from VMs which are attached to logical switches or distributed port group within NSX to which distributed router is attached to.
It's possible to define several DHCP servers.
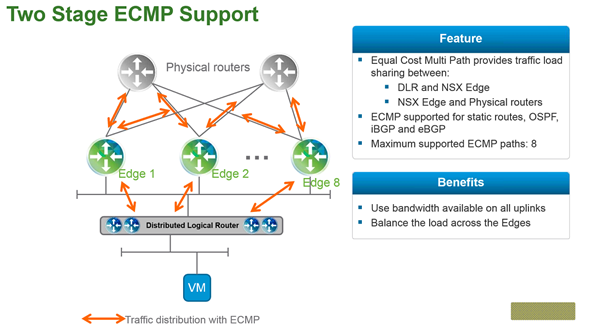
Two Stage ECMP Support
Equal cost multi path routing support for distributed logical router and also for NSX edges. There is the distributed router, which can have multiple upstream NSX Edges to egress traffic from, and also in the upper layer the NSX edges can have multiple upstream physical routers with Equal cost multi path routing to egress traffic from as well as receive.
Allows High availability and scale out.
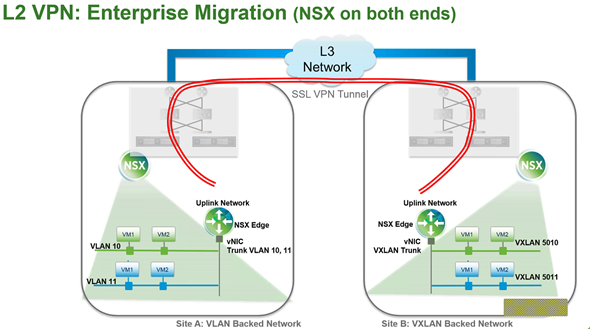
L2 VPN: Enterprise Migration (NSX on both sides)
This feature is an enhancements to previous version of NSX where previously on one VLAN could be trunked. It can be used for migration of workflows between datacenters. You can trunk multiple VLANS of multiple VXLANs from one datacenter to the other.
This function brings similar functionality as Cisco OTV (Example here), which is providing is a “MAC in IP” technique for supporting Layer 2 Vans over any transport. The L2 VPN provides trunking L2 network from one side to another over L3 network encrypted by SSL VPN tunnel.
Another use case would be for example to extend an NSX datacenter to non-NSX datacenter. See image below… In this case the remote site is not running an NSX. You can extend the L2 network from the remote site where you can deploy an NSX Edge and provide the VLAN trunking, to extend the L2 networks from the remote site into an NSX deployment into the datacenter.
- Both the sites could be NSX Free Edge
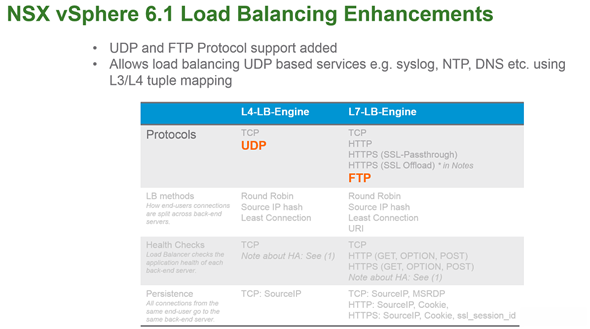
NSX for vSphere 6.1 Load Balancing Enhancements
The load balancer can be turned On on the NSX Edge. So you're able to have TCP as well as UDP load balancing.
Just a few enhancements here.
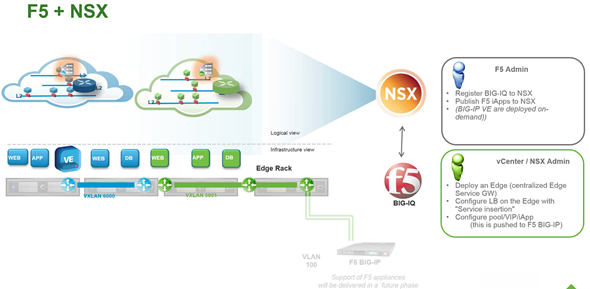
F5 and NSX
VMware is partnering with F5 to inject the nextgen firewall in NSX deployments.
When customer wants to deploy load balancer for their application, they have the choice between the load balancer present in NSX and F5 load balancer.
As concerning the deployment within vCenter, the admin will have the possibility to check a box to allow a service insertion, which would allow the F5 insertion.
Firewall Enhancements in NSX
- Firewall Reject action (not only allow or deny)
- Troubleshooting and Monitoring
- Advanced filtering of rules ( you can filter to find rules)
- CPU/Memory Thresholds (if CPU thresholds are reached, the admin will get notified)
- IPFIX Support in DFW (distributed firewall)
- Combined Edge and DFW Management (single management of rules for Distributed firewall, Edge or both)
- Network Oriented service insercion (NetSec Partner Redirection)
NSX Multi Hypervisor 4.2
- NSX Multi-Hypervisor is a minor release
- controller HA/Hitless upgrade
- DHCP Relay
- OVS performance enhancements
- Security profile scale enhancements
- Scale Targets unchanged
- Upgrade from any 4.1x release is supported
- Hearbleed issue fixed in 4.2 release
- GA in Q3 2014
Micro Segmentation
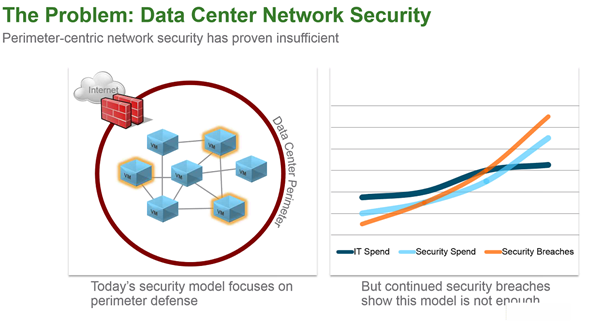
Apparently the micro segmentation is the feature that makes VMware to actually sell a lot of NSX, and clients are buying NSX to use that particular feature in their datacenters. Usually in traditional datacenters where a single firewall is protecting the whole datacenter – a problem can occur if someone break in. If does, then he(she) can do whatever he (she) want, because single firewall is protecting the environment.
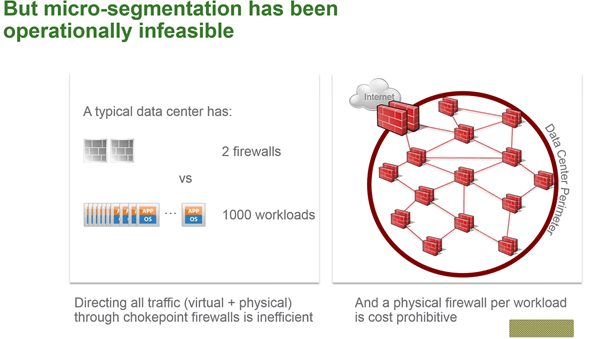
Usuall datacenter has 2 firewalls but the number of VMs counts in hundreds (thousands)….
That's why micro-segmentation (isolation) provides the best results. The firewall in VMs does not really help.
A physical firewall per workflow is not cost effective (too expensive)
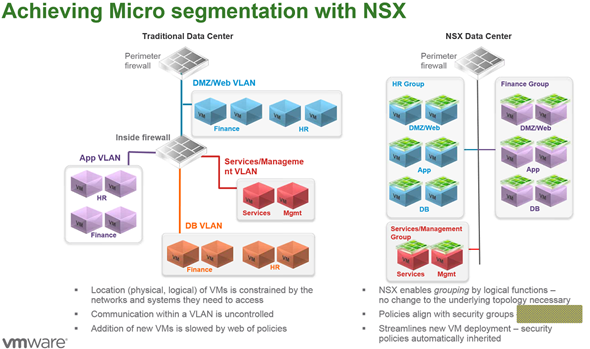
The solution is to provide firewall services through the hypervisor's kernel module. Distributed firewall kernel module provides a protection to VMs so when VM is created, a firewall policy is attached to that VM. So if the VM is moved to another host, the policy follows.
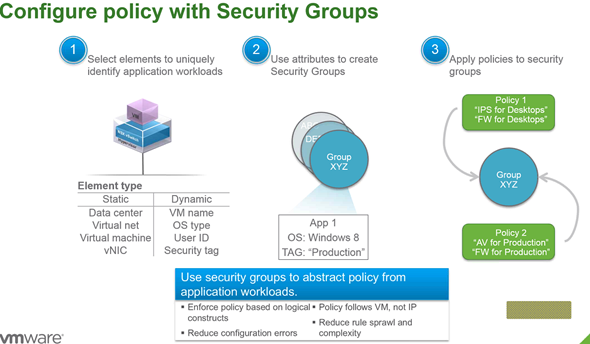
If VM is deleted, the policy gets deleted as well. It's not VLAN centric security deployment but rather creating in security groups which can be static or dynamic. And VMs are attached to those groups. The policy is applied to the group. It simplifies the topology.
It works through the identification of workflows, use attributes to create security groups and then apply policies to those security groups. Here is another screenshot to ilustrate.
The micro segmentation provides better security inside of the datacenter.
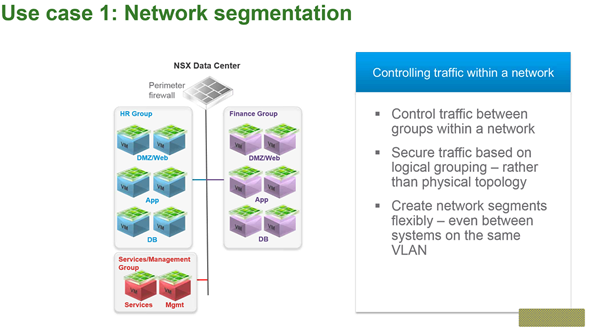
Example 1:
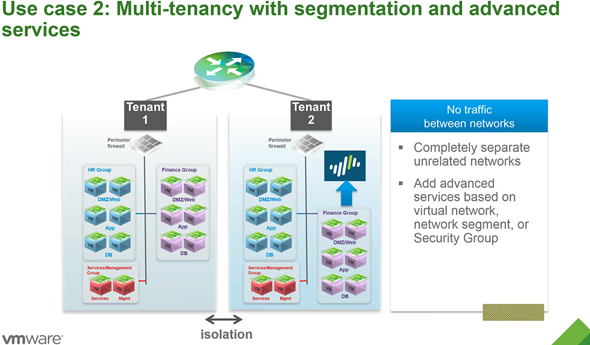
Example 2:
Networking is quite a complex topic. During VMworld the NSX team will provide many product demos and examples.
If you're not present at VMword San Francisco, you can still register for VMworld Barcelona.
Special Report:
- VMware EVO:RAIL – New hyper-converged solution by VMware
- What's New in VMware NSX For vSphere 6.1 (This post)
- VMware OpenStack Integration
- Infinio Accelerator v2.0 Announced with FC, iSCSI, FCoE, NFS and Enviromnents with Multiple Protocols
- VMworld 2014 FlowGrab Beta Launching Centralized Workflow Repository
- Fujitsu One Of the First OEM Partners Announcing VMware EVO: RAIL Integration
- vRealize Cloud Management Platform, vCloud Suite 5.8, vCloud Air Object Storage…
- DataDog Adds VMware vSphere Support
- vMotion Enhancements in vSphere 6.0 – Long Distance vMotion, Across vSwitches and Across vCenters
- VMworld 2014 US Keynotes Day1 and Day 2 Videos
- Rapid-Cloning Technology (project Fargo) and copy-on-write architecture – Future of Desktop Virtualization
Stay tuned via RSS or Twitter.