This is a very important chapter VCP6-DTM Objective 1.5 – Prepare Environment for Horizon (with View). As without the proper setting of your AD groups, AD organizational units (OU), vCenter users (and priviledges) the environment will not meet the requirements and some components might not work correctly or users will get too many priviledges and perhaps put your company at risks. So to prepare a horizon environment is very important.
So in today's topic VCP6-DTM Objective 1.5 – Prepare Environment for Horizon (with View) we will teach you all that. All the VCP6-DTM exam topics will get covered and gathered on single WordPress page – VCP6-DTM Study Guide.
Knowledge
- Explain characteristics of required Active Directory domain accounts, groups, and permissions
- Identify and describe the Group Policy Object template files
- Describe Organizational Units for machine accounts
- Verify trust relationships
- Describe DHCP requirements for Horizon View desktops
Tools
- Horizon View Installation Guide
- Horizon View Security Guide
- Horizon View Administration Guide
- Setting Up Desktop and Application Pools in Horizon
- Horizon View Administrator
Explain characteristics of required Active Directory domain accounts, groups, and permissions
Microsoft AD is supported at the following AD levels:
Windows Server 2003, 2008, 2008r2, 2012 and 2012R2. View connection servers has to be joined to AD, but the server must not be a Domain controller.
You'll need few things:
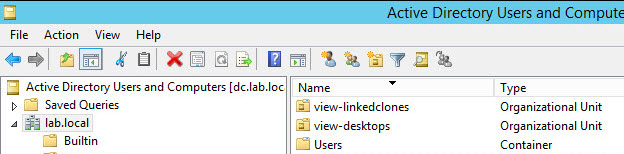
- Create an OU for Remote desktops
- Create Groups for users
- Create a user account for vCenter server
- Create a user account for Standalone View Composer server
- Create a user account for View Composer AD operations
Step 1: Create an OU for View Remote Desktops. In this OU will be all computer accounts used within view desktops. You can easily apply GPO on that OU. A GPO that will be different from other GPOs used in your environment. If using View composer you should create separate OU for linked-clone desktops.
Note: If you're using kiosk mode than you should also create an OU for those desktops running in locked-down kiosk mode. And also you should create an AD group for kiosk mode client accounts. It allows to separate the different settings, configuration and administration.
Step 2: Create Groups for users.
Create group viewusers and viewadmins. Like this you, again, can differentiate and setup different configs for both groups which won't have the same privileges on the environment. Users can only use the desktops while administrators can login as admin to the environment to perform administration tasks.
Step 3: Create vCenter service user account for vCenter server, in AD:
We'll name this account vcenterservice and this user account will be used when you'll be within View admin portal when adding vCenter server instance. This account is used when View interacts with vCenter (behind the scenes) when provision desktops, powers them on, or off etc. The privileges of this account should not be as high as administrator's account. There is no reason for that. The vcenterservice service user account must be in the same domain as your View Connection server, or in a trusted domain.
- Case A: Composer installed on the same machine as vCenter (if Windows) – you must add the vCenter server user to the local admin group on the vCenter server VM (or physical). This requirement allows View to authenticate to the View Composer service.
- Case B: Composer installed on separate machine – have to create a standalone View Composer Server user account that must be a local administrator on the View Composer
machine. (note we have done this in the Objective 1.2 for composer installation as we installed on separate VM)
Step 4: Create a user account for Standalone View Composer server – the same as case B. You must create separate user in AD in this case. view will use this account to authenticate to the view composer service on the standalone composer machine.
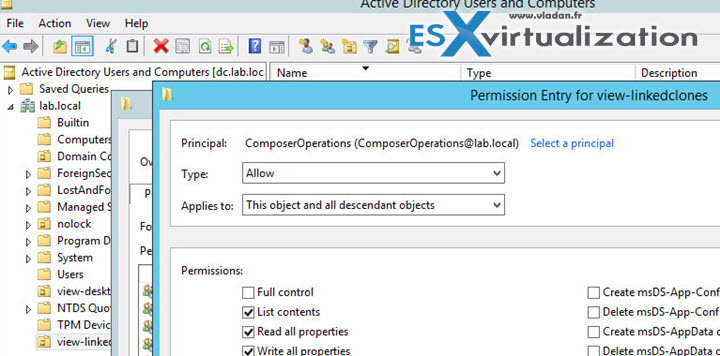
Step 5: Create a user account for View Composer AD operations – a special composer account is needed that view composer will use to join linked-clones to AD. A separate AD account shall be created for this purpose. You can give a minimum privileges to this account to ensure that this account can do only the tasks needed. In our case we have created a ComposerOperations user…. How?
- Go to AD and create a user account which you'll place to the viewlinked-clones OU.
- Apply following permissions to that OU (including those assigned by default):
- List Contents
- Read All Properties
- Write All Properties
- Read Permissions
- Reset Password
- Create Computer Objects
- Delete Computer Objects
NOTE Fewer permissions are required if you select the Allow reuse of pre-existing computer accounts setting for a desktop pool. Make sure that the following permissions are assigned to the user account:
- List Contents
- Read All Properties
- Read Permissions
- Reset Password
Make sure that the permissions apply to the OU and to all child objects!
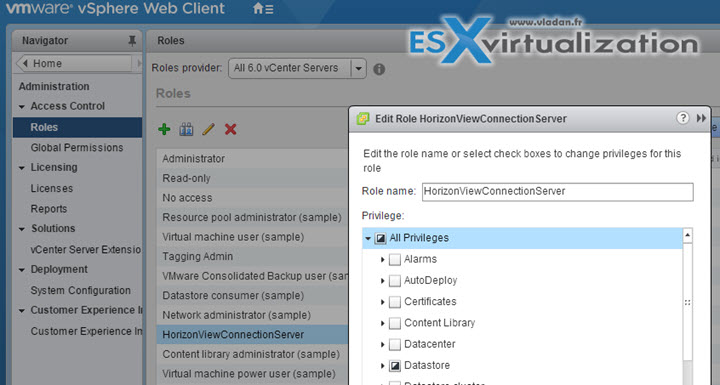
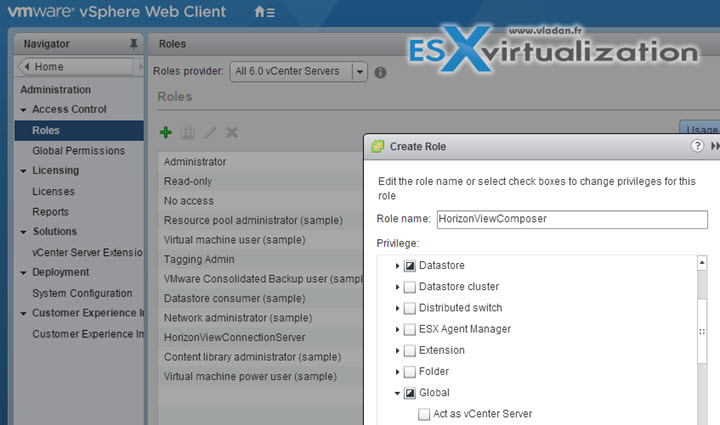
Create new role in vCenter server – We also need to create a new role in vCenter: > Administration > Roles > and assign privileges needed for that role.
HorizonViewConnection vCenter server role privileges:
We're using Composer, so we'll be using certain set of privileges in vCenter for that. If you don't use composer, than you'll most likely want to set this different way. See p. 83 of the Horizon View Admin guide.
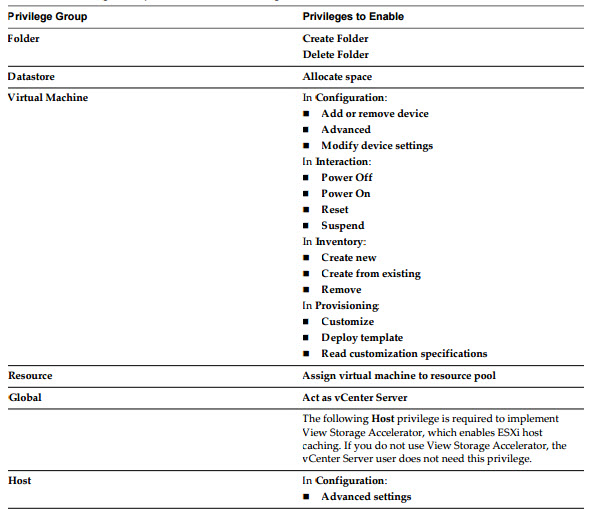
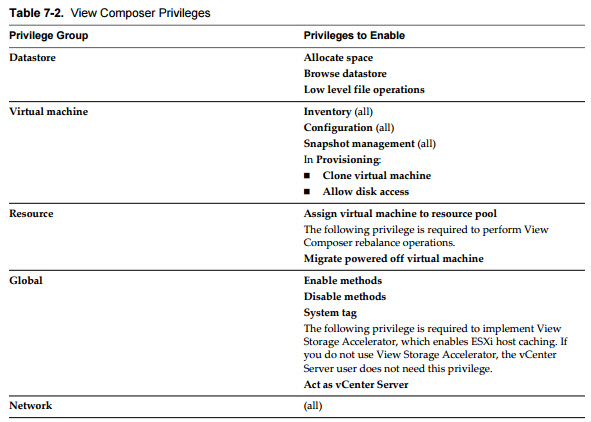
vCenter priviledges for HorizonViewComposer role:
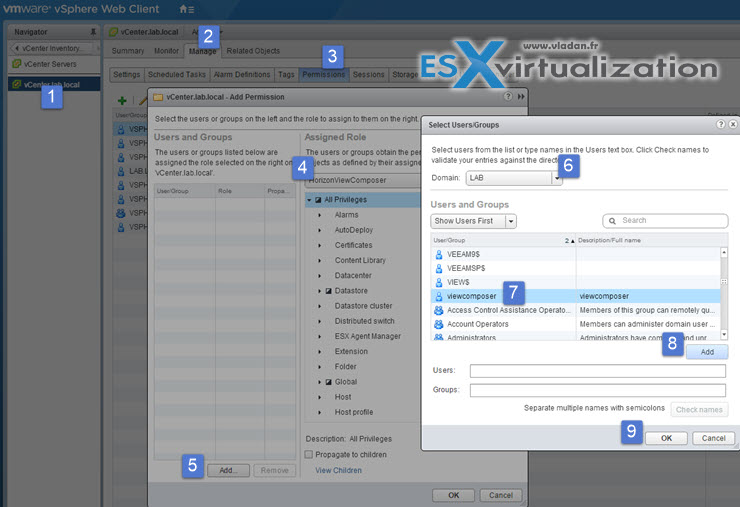
Once done we need to do one more thing while in vCenter admin UI. We need to assign permissions for composer service account that we created in our AD, to the vCenter root…
You see the required steps through the screenshot here….
Identify and describe the Group Policy Object template files
View provides several component-specific Group Policy Administrative (ADM and ADMX) template files. You can optimize and secure remote desktops and applications by adding the policy settings in these ADM and ADMX template files to a new or existing GPO in Active Directory. All ADM and ADMX files that provide group policy settings for View are available in a bundled .zip file named VMware-Horizon-View-Extras-Bundle-x.x.x-yyyyyyy.zip
To install:
- Unzip the file and copy the View Persona Management ADM Template file, ViewPM.adm, to your Active Directory server.
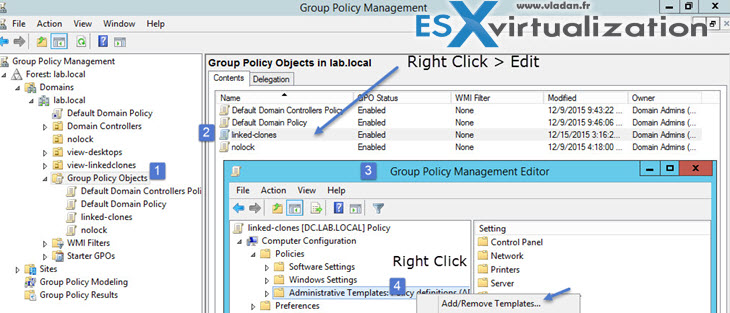
- On your Active Directory server, open the Group Policy Management Console. (gpmc.msc)
- In the left pane, select the domain or OU that contains your View machines.
- In the right pane, right-click the GPO that you created for the group policy settings and select Edit.
- Right-click Administrative Templates under Computer Configuration > select Add/Remove Templates.
- Click Add, browse to the ViewPM.adm file > click Open.
- Click Close to apply the policy settings in the ADM Template file to the GPO.
The name of the template appears in the left pane under Administrative Templates….
Describe Organizational Units for machine accounts
Details in the text above…
Verify trust relationships
In case you have more than one domain, you must establish trust relationship between those domains. This must be an external non-transitive two-way trust. Users are authenticated against Active Directory for the View Connection Server host's domain and against any additional user domains with which a trust agreement exists.
View connection server instance traverses trust relationships beginning with its own domain. For small number of domain which has good connectivity the filtering isn't necessary, but can help in access time when domains get larger or the connectivity between those domains doesn't perform well. In this case it's possible to use vdmadmin command to configure domain filtering which limits the domains that View connection server instance searches and displays to users.
Describe DHCP requirements for Horizon View desktops
To be defined…