Usually it can hapend after restore operation. You restore an older VM and the Windows VM can't authenticate with the domain because the Trust Relationship between workstation and domain fails. You can see a nice error saying that “The Trust Relationship between this workstation and the primary domain failed”.
It can also happens if you restore from an older backup, which you have done on a physical system. Those backups can are usually done by imaging solutions, like the ones from Acronis (True Image) or Symantec (Norton Ghost) etc. Who do not know those, hein? But In this case also you'll face this problem with broken relationship. The default domain value is 30 days. After that each workstation do a reset of their computer account password in AD.
Now the easy way to fix this problem is probably to disjoint the workstation from the domain > reboot > and join the domain back again. Not a big deal you say, but sometimes it's not an option.
But wait there is better way. It's one liner and no need to reboot.
In fact you can use single command to reset the computer account. You need to log into computer under account which has local admin rights.
Here is the command:
netdom resetpwd /Server:DC /UserD:Administrator /PasswordD:mysuperpassword
Explications:
- Server:DC is my domain controller
- UserD:Administrator – is the user with domain admin rights
- PasswordD:mysuperpassword – is the administrator's password
This works for server systems but also for client systems. Unfortunately if you have Windows XP for example, the Netdom command won't work because the netdom.exe isn't installed. But you can copy it from Windows server CD or iso image.. (I know additional work)…
The Netdom.exe and Nltest.exe tools are located on the Windows Server CD-ROM in the Support\Tools folder. To install these tools, run Setup.exe or extract the files from the Support.cab file
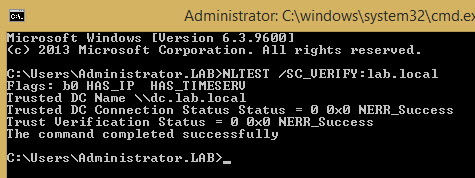
You can simply test if the secured channel has been reestablished. Just try on any domain connected workstation or server via this command:
nltest /sc_verify:lab.local
where lab.local is my lab domain….
The output looks like this:
Now I was thinking, there must be a GPO who manages the default value of computer passwords no? Yes there is! So for my lab environment I disabled the machine password change frequency comptetely!
It's Maximum Machine Password Age and it's located at:
GPO_name\Computer Configuration\Windows Settings\Security Settings\Local Policies\Security Options
The policy name is:
Domain Member: Disable machine account password change = Disabled
It's possible to turn it off there
Now you may not want do this on your production environment, because it's a security concern. Read the Microsoft's Technet link which explains this GPO in details here.




I got around this issue specifically with snapshots by changing the computer password age to 999 days on all my templates.
Which you can change in the registry settings:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Netlogon\Parameters]
“Update”=”no”
“DisablePasswordChange”=dword:00000001
“MaximumPasswordAge”=dword:000003e7
Thanks for sharing.
Dear Sim,
is your solution totally solve this issue? We have this issue around 30 days after we deploy pc using cloning solution.
Thank you and appreciate your reply
Thanks thats what i need!
Could you explain this statement.
“After that each workstation do a reset of their computer account password in AD.”
This means that the workstation itself makes the computer password reset under the built-in System account when it becomes necessary?